AdGholas malvertising spreading Mole ransomware linked to UCL cyberattack
The massive malvertising group has shifted focus from dishing out banking malware to serving up ransomware.
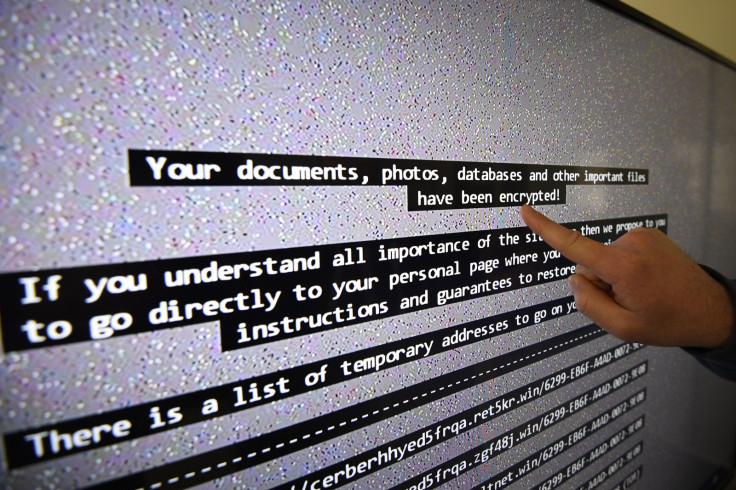
The University College London (UCL) ransomware attack that shut off access to sensitive files on shared drives last week has been linked to the massive and proliferate AdGholas malvertising campaign. Security experts say that the group behind AdGholas has shifted focus from dishing out banking malware to serving up ransomware in new attacks.
According to security researchers at Proofpoint, the malvertising campaign also affected several other "high-profile" websites as well. Researchers said that the group used the Astrum Exploit Kit to spread the Mole ransomware, a CryptoMix variant.
"The level of complexity of this particular infection chain also suggests a higher-than-average level of sophistication on the part of the threat actors. Although the current volume of exploit kit activity is far less than we observed at the beginning of 2016, we continue to see significant evolution in the space, with notable "zero-click-required" campaigns particularly from AdGholas and Astrum EK," Kevin Epstein, VP of the Threat Operations Center at Proofpoint told IBTimes UK.
Researchers found an IP address linked to a Mole ransomware C&C (command and control) server involved in the attacks. The domain was also found used in several other malvertising campaigns across Great Britain, Australia, Canada, Italy, Monaco, Liechtenstein, Luxembourg, Switzerland, Japan, Taiwan, and the United States.
"It appears that between June 14 and 15, Astrum was dropping Mole ransomware in the United Kingdom and likely in the US," Proofpoint said.
Meanwhile, UCL said yesterday (20 June) that all services are now back to working normally after the university's personal storage and shared drives were restored on Friday (16 June).
"If the malicious payload in this case hadn't been ransomware, which is obviously much more visible to users than the banking Trojans these threat actors normally distribute, the victims might never have known they were infected," Epstein told us. "It isn't necessary to click on an ad in a modern malvertising attack; a user on a targeted, vulnerable PC only needs to visit a page displaying a malicious ad to be infected with the payload of the threat actor's choice."
AdGholas' shift in focus to ransomware also indicates a troubling escalation of interest among cybercriminals in launching such attacks. The recent massive WannaCry attacks have highlighted the major threat that ransomware poses to businesses and organisations. A combination of malvertising and ransomware hints at how cybercriminals adapt to adopting new attack vectors.
"AdGholas malvertising redirecting to the Astrum Exploit Kit is the most evolved blind mass infection chain known today," Proofpoint said.
"Cybercriminals continue to develop ransomware, and leading universities like UCL, whose systems contain highly valuable data, are clearly targets," Epstein added. "Universities and other institutions need to constantly review the preventative steps they are taking to minimize risk of an attack across email, mobile devices, web browsing and other network-exposed surfaces."
© Copyright IBTimes 2024. All rights reserved.






