Android.Bankosy: Trojan that steals one-time passcode from Android devices found

A Trojan that steals data from compromised Android devices was found to be quite active in the last quarter of 2015. Dubbed Android.Bankosy, the malware steals the one-time passcode (OTP) sent to the user's Android mobile through voice calls generated by two-factor authorisation (2FA) systems.
The authorisation is a process that requires users to secure their account, something more than just a password. In the 2FA system, the second factor, which is OTP, is sent to the user's mobile phone through a short messaging service (SMS). But hackers always found various means to install malware on the phones or intercept the SMS that contains the OTP. Aware of this, some financial institutions such as banks are delivering the OTP through voice calls directly instead of SMS, which the malware creators have become aware of.
How attackers use Android.Bankosy
The malware was first spotted by cybersecurity firm Symantec. There are no details as to how many Android phones are affected by Android.Bankosy which gives backdoor access to hackers when the malware is installed on the compromised device.
The malware collects system-specific information and sends it to the command and control (C&C) server. After registering the Android device in the server, the malware uses an ID to communicate further with the server and receive command from there.
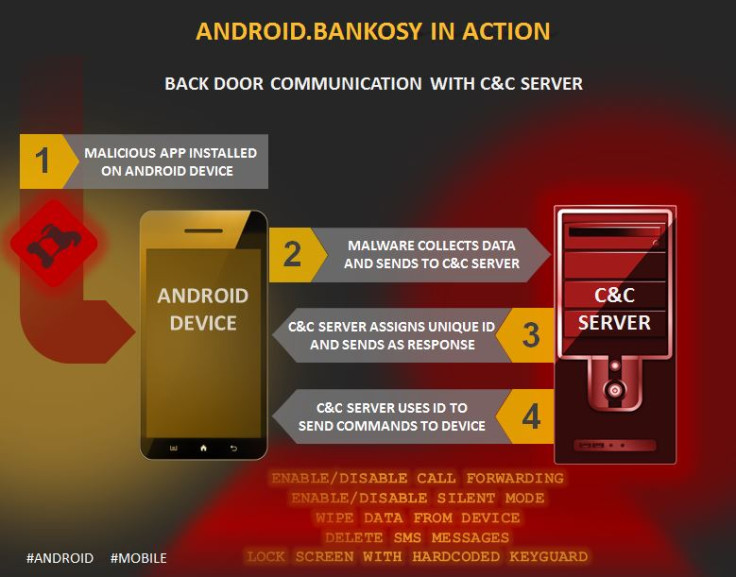
Call forwarding to perform transaction
Most of the commands sent from C&C are common financial Trojans such as intercepting incoming SMS, deleting SMS or wiping data. One of the significant commands for Android.Bankosy is call forwarding. The malware starts a call with the number that is obtained from the C&C server to enable call forwarding. The user of the Android device remains completely unaware of the incoming calls as the back door is capable of disabling and enabling silent mode and locking the device.
The attacker, having access to the user's credentials, can get started with the financial transaction, once the call forwarding is set on a compromised device. When the system prompts to enter the second authentication step, the hacker actually takes advantage of this, and gets call through the call forwarding and enters the second factor to complete the transaction.
To guard against the malware, Symantec advises users to keep the software of their phones updated. Avoid downloading apps from suspicious sources. Always pay attention to the permission you give when requested by an app. To keep your phone protected against malware attack, install a security app such as Norton. Finally, do not forget to create a backup of the data of your Android device.
© Copyright IBTimes 2024. All rights reserved.





