Android Malware shows Limitations of Google's Security [VIDEO]
Deficiencies in the way the Android mobile operating system identifies and deals with malware have been highlighted once again with the discovery of Android.Dropdialer on Google Play.
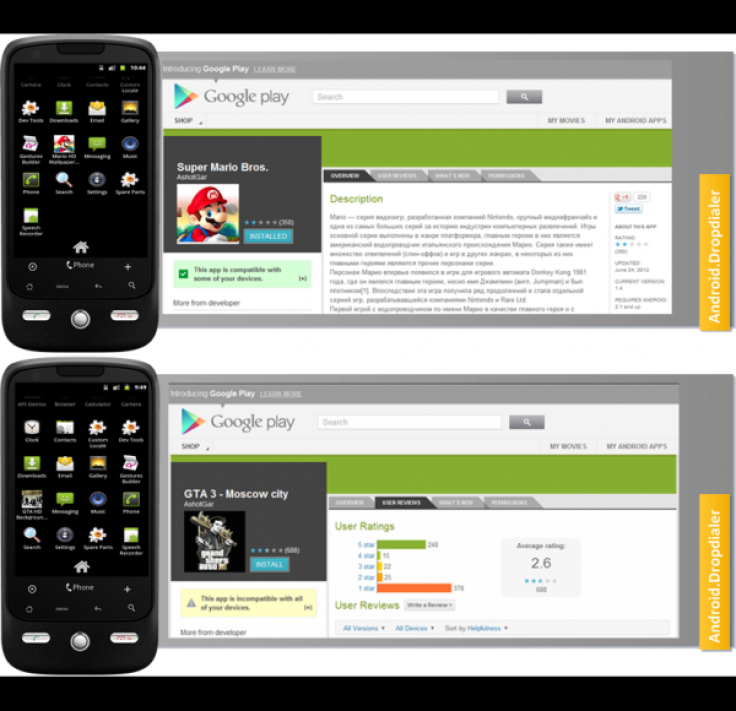
The virus, which was first detected by security firm Symantec, was found in two popular games in the Google Play store, Super Mario Bros. and GTA 3 Moscow City. Both games were posted on Google Play (formerly Android Market) on 24 June and since then generated between 50,000 and 100,000 downloads.
"What is most interesting about this Trojan is the fact that the threat managed to stay on Google Play for such a long time, clocking up some serious download figures before being discovered. Our suspicion is that this was probably due to the remote payload employed by this Trojan," Symantec's Irfan Asrar said on the company's blog.
This technique is not new however, and the same security expert spoke about this method of slipping malware onto the Android platform a year ago. Using this technique, the author of a piece of malware would break it up into separate, staged pieces in order to avoid detection by the automated security set-up which is in place for apps looking to be listed on Google Play.
Once the user installs the initial piece of the malware code, it would then download another piece of the malware, in this case called Activator.apk which was stored on Dropbox. Once this was installed the malicious software then sent out premium rate SMS messages without your knowledge.
Permission
However, in the blog post, Asrar shows an image (below) which suggests that users are told before installing the Activator.apk piece of the malware that they will be allowing the app to send these messages, therefore some of the blame should fall on those users who chose to ignore this warning.
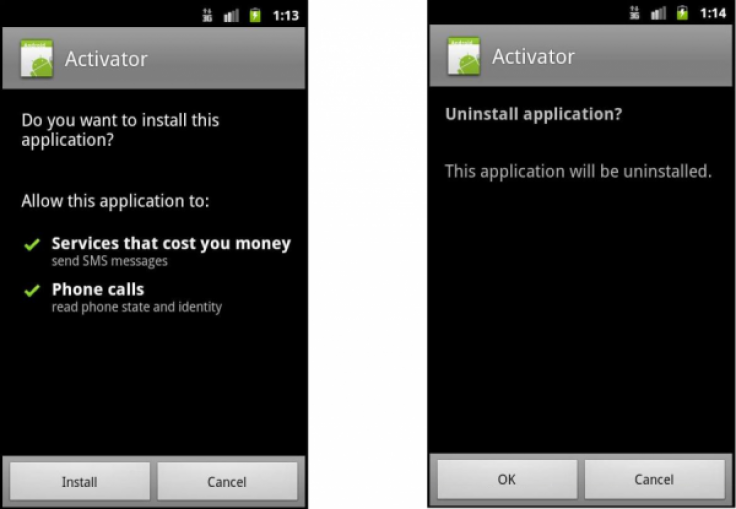
Once the costly text messages have been sent, the app prompts you to uninstall it, an obvious attempt to hide the true intent of the malicious app. According to Asrar, the app is targeting users in Eastern Europe mainly.
We have asked Google for a response to the issue but at the time of publication we have received no response. Android Security did however remove the offending apps from Google Play, once it was informed by Symantec.
Security expert at Trend Micro, Rik Ferguson has previously told us that the open nature of Android makes it an easy target for cyber criminals and Ferguson says criminals are mimicking what they did previously on PCs.
"I think that criminals are trying and testing the same and similar techniques that have already been successfully used against PCs for many years and the ones that work out will stick."
© Copyright IBTimes 2024. All rights reserved.






