Businesses and Employees at Risk Using iPhones and iPads for Work
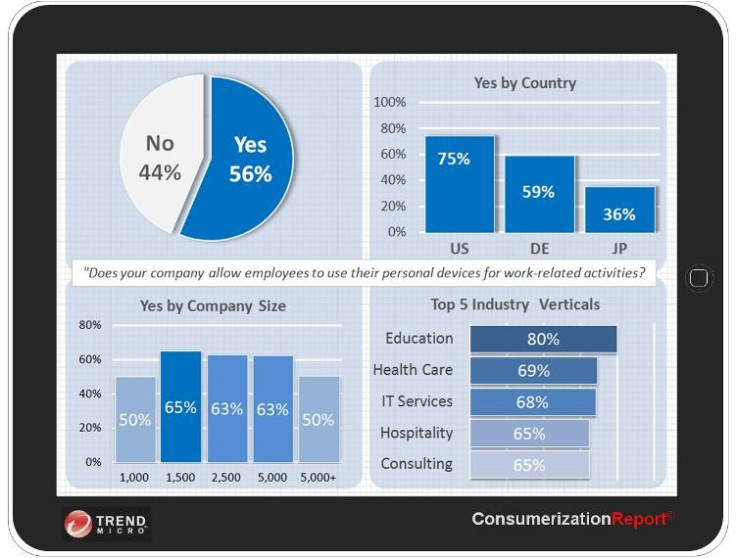
According to the Trend Micro Consumerization Report 2011, up to 75 percent of companies in the US are now allowing employees to use their own phones, tablets and laptops for work and in most cases are even supplementing the cost of these devcies.
While there are benefits for both sides with this new Bring Your Own Device (BYOD) trend, Senior Director of Consumerization at Trend Micro, Cesare Garlati warns that unless both the employers and employees educate themselves, it could lead to multi-million pound litigations and the loss of irreplaceable personal information.

While the US shows the largest percentage of BYOD uptake in the world, Europe is not far behind and is catching up all the time. Employees are certainly pushing for this to happen, but Garlati also believes this is something which has been hastened by company CEOs who want to use their own iPhones, Android tablets of Ultrabooks for work. And if CEO's can do it, then why not everyone else?
For years, companies have been pushing enterprise-ready devices on employees, primarily in the form of BlackBerry phones and locked-down laptops which were rightly seen as the most secure way of accessing work email and files while on the move.
However a combination of events has led to this changing rapidly in the last couple of years. We have seen the advent of the smartphone and tablet, and the pervasive nature of this technology means that people own one or the other, or indeed both.
Add to this the downfall of BlackBerry maker RIM in the last 12 months, including a worldwide service outage, and it is easy to see why people are more than happy to bring their own phones to work.
Benefits
And there are major benefits to this system. From the company's point of view there are two main benefits. The first, is "business agility" which Garlati categorises as the ability to adapt quickly to the changes in the environment by relying on the technology.
"Innovation is happening at Google and at Apple, it is not happening at IBM or Oracle, the traditional enterprise companies," Garlati, who previously worked for Oracle, said.
Another benefit for companies is a lower capital expenditure due to the phones and tablets now being purchased costing relatively little, partly due to them being subsidised by networks. The consumer devices now in use are also a lot cheaper than the enterprise-class phones and laptops traditionally purchased by businesses - which came with a lot of added extras such as security software.

Another benefit for companies is that because employees are using their own phones or tablets, they tend to check their emails more and inadvertently do more work, and even if this is just 20-30 minutes a day, it adds up to a significant amount of time over the year.
For employees the benefit is being about being able to use your new phone, tablet or laptop at work and not being forced into using a device which is locked down by the companies' IT department and which is not very nice to use.
Risks
However, despite the benefits, there are serious risks for both parties. Companies face the added cost of providing helpdesk support for a wide range of devices and operating systems, where before it would have dealt with a single phone, single operating system and possibly just two versions of one laptop.
Secondly, and much more importantly, while the consumer devices may be nice to use, they are far from secure, or as Garlati puts it: "These things are sexy, but not secure at all." Because employees are using these devices to access sensitive work emails and files, they are leaving themselves vulnerable to attack: "They shouldn't be asking if we will see a security breach, companies should be asking when there will be a security breach."
Garlati highlights one situation in relation to Dropbox, which many people use to transfer large files due to limitations placed on work emails. While Dropbox is inexpensive and easy to use, it has "no security at all," according to Garlati. Last June for four hours, Dropbox had a security breach which meant that anyone could access any of the 80 million accounts without entering a password.
However Dropbox counters this argument, saying it does have security including Secure Sockets Layer (SSL) and AES-256 bit encryption. The Dropbox website claims: "Your files are actually safer while stored in your Dropbox than on your computer in some cases. We use the same secure methods as banks." While it did admit the security breach, it pointed out that only one percent of users logged in during the four hour window. It should also be pointed out that Trend Micro has a similar product to Dropbox called SafeSync.
But what are the dangers for you as an employee? Garlati has written about a case where a woman used her iPhone for work. She signed the acceptable usage policy and is given access to corporate email on the go.
The woman's performance dipped and after six months she was let go. As part of the termination process her company remotely wiped all information on her iPhone. It turned out that the woman's performance dipped because her son was dying of cancer and a couple of weeks prior to her being fired, her husband had taken a picture of the woman and her son on the iPhone, which was the last one she had of the two of them together. This photo was destroyed by the company's remote wiping of information. The woman sued for damages.
Before you get too worried, this case is fictional and was created and debated at last year's International Legal Technology Association (ILTA), where attorneys and expert witnesses came to the conclusion that the value of that deleted photo would be £3.15m ($5m).
This is a growing problem in the corporate world where remote information deletion, employee tracking and monitoring of internet use are becoming more and more commonplace and companies for the most part do not understand their liability or how to address the issue.
"The story for the enterprise is to understand this and learn how to embrace it. Don't try to fight it, because what we see is companies saying no, you cannot do it," Garlati says.
Education
Education is key to make sure that both businesses and employees pay more attention to exactly how BYOD and consumerization in general will affect their lives. "There is a lack of understanding, a lack of education. They [businesses] are using old solutions for new problems."
Some companies are getting the message, even to the point of using cartoons and social media to try and inform their employees as to what the policies actually mean. However, this is still a minority and most companies are looking at it in the old way, believing that just because you ticked a box or signed a piece of paper, they are covered.
The companies which are making a change are the bigger companies whose deep pockets can afford to make the change. Garlati believes that small to medium sized companies don't have the resources to make the changes and this could spell trouble.
Asked if these problems could lead to a reversal in the current trend of consumerisation, Garlati is insistent that BYOD is here to stay: "It cannot be stopped. Even companies that try to say no, they are just hiding their heads in the sand."
One of the main reasons for the high possibility of a security breach is that employees will do anything and everything to circumvent the restrictions put in place by IT departments and will take pleasure in doing so.
Garlati believes IT centres should treat employees like customers to get them to understand just what the security risks are, but unfortunately most just don't. "They don't really treat employees like customers, it's more like the 'human factor risk', the 'layering between the screen and the chair'. I mean there is a whole terminology there that is....my goodness. If that is how you look at your internal customer, it's not surprising this is happening."
The problem is clearly two-fold. Companies have been caught on the hop and are not reacting fast enough to the changing work environment and, unless they clearly explain the policy to your employees, the liability will lie with the enterprise, even if you put a 20-page document in front of your employees and get them to tick a box.
On the other side of the coin, employees don't really know what they are getting into when signing the policy documents given to them by the company and for the most part don't want to know. They need to educate themselves with regard to what it means to use the iPhones or iPads for work and understand the significant risk involved of losing important and irreplaceable personal data from their devices.
© Copyright IBTimes 2024. All rights reserved.






