Just One in Five Emails Sent in 2012 Were Legitimate
Such is the overwhelming volume of spam and malicious email sent today, only 20 percent of all messages are sent for legitimate reasons.

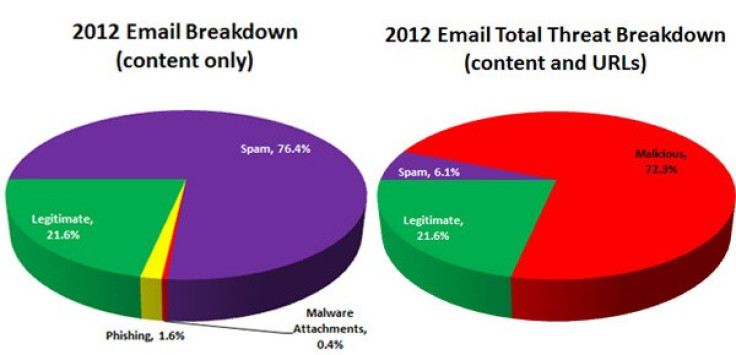
Throughout 2012 spam emails sent reached a level of more than quarter of a million every single hour, equating to 2.2 billion spam emails during the year.
According to the Websense Threat Report 2013, spam email is no longer a mere nuisance, with 92 percent of spam including links to malicious websites which often pointed to phishing, malware and other malicious content.
As shown in the charts below, relatively few emails actually contained malicious content; however, a huge percentage of non-legitimate emails contained malicious web links.
This trend was reflected in a 600 percent increase in the number of malicious website identified in 2012 compared to 2011 by Websense. "That is quite an astonishing amount." Carl Leonard, Senior Security Research Manager at Websense said.
The increase in the EMEA region was around 500 percent, while the US saw an increase of more than 700 percent, which Leonard said indicates that the threat has never been greater to enterprises and individuals.
"These are sobering facts for those who thought email threats were declining or not evolving alongside other cyberthreats. As with most mobile and social threats, email typically plays a more innocent-appearing role in the early stages of an attack; its intent is to lead users to web content that carries out the most malicious activity," Websense said in its report.
Only the beginning
While spam email may be the beginning of an attack, 2012 also saw the rise of much more targeted email attacks, known as spear phishing. This type of attack uses social engineering to identify a specific individual within a specific company and sees cyber criminals craft individual emails for that target.
A spear-phishing attack begins with a cybercriminal performing online "reconnaissance" to compile information on a targeted victim's work, education, hobbies or other interests.
The emails appear to come from legitimate sources and contain documents or links which are relevant to the target. For example the chief financial officer of a company could be targeted with email which appears to come from the HR department and contains a document purporting to show the annual wage bill.
Once the target opens the document or clicks the link, malware is secretly installed on the PC and from there the malware authors can gather sensitive information as well as spread within the company's network.
Leonard said that while the attacks are highly targeted, the malware being used isn't necessarily cutting edge:
"[The cyber criminals are] not necessarily using the most complex malware but it's a combination of factors. It looks very appealing to the recipient, something that they would be more inclined to execute, click on the link etc. They are using the very best social engineering can offer to encourage people to click the link, open the attachment."
Source
The United States was the number on source of phishing emails in 2012, followed by the Bahamas, Canada, Germany and the UK.
Websense said that the location of spam and phishing hosts shifts frequently, with Brazil, Egypt, Israel and other countries all appeared in the top five at various times during the year.
"Hosts may even change in the middle of an attack in response to obstacles, such as when a host detects unusual activity and interrupts the attack. And many attacks actually use multiple hosts, to send the most email in the shortest time," the report said.
One aspect of phishing attacks which remained constant last year was the fact that two-thirds of phishing emails were sent on Mondays and Fridays, the days when users are more distracted with personal concerns - making them more likely to fall prey to attacks.
Method
Another method being employed by cyber criminals to make their malicious emails look more authentic is using legitimate-appearing events, brands, and web link in their email attacks to mask their intentions.
During 2012, one of the most common subjects used was the London Olympics providing many opportunities for abuse; for example, many email attacks took place months before the opening ceremonies, using offers of fake tickets, travel and other Olympic-related items.
Cyber criminals also showed that they could think on their feet taking advantage of unplanned events, such as a celebrity death or a natural disaster, as they reacted in less than 12 hours on average.
© Copyright IBTimes 2024. All rights reserved.






