Britney Spears' Instagram is toxic: Hackers use celeb's account to hide malware code
The Turla cyber espionage group is hiding links to its C&C servers in Instagram comments to avoid detection.
A Russian cyber espionage group has found a new way to hide its nefarious activities on the internet by posting links in code as comments on celebrity Instagram accounts.
Cybersecurity firm ESET detected that the Russian hacking group Turla has been hiding links for its malware to pick up in coded messages in the comments on Britney Spears' Instagram account.
Turla has existed for well over a decade and is well known for creating and distributing advanced persistent threat (APT) malware designed specifically to extract data from nations, businesses and organisations for political espionage purposes.
Once the malware takes over a target's computer, it can quietly monitor the computer and send data back to the hackers' command and control (C&C) servers over a long period of time without being detected, acting like an automated spy.
To prevent cyberattacks, apart from disclosing security vulnerabilities in popular software and operating systems, cybersecurity researchers and law enforcement agencies also analyse the code in malware to locate the address to C&C servers so they can block traffic from being sent to the hackers and get the servers and domains shut down.
Turla has been trialling different methods to hide the IP addresses of its C&C servers so that cybersecurity experts can't stop them. In 2015, the hacking group hijacked unencrypted satellite internet connections belonging to satellite internet providers in the Middle East and Africa to send data via the satellite links, but now Turla has moved onto an even cleverer method.
Hacking a Firefox extension to look for coded Instagram comments
The hacking group's latest technique involves sending malicious Microsoft Word documents in a mass email spearphishing campaign. If the target opens the malicious email attachment, malware that installs a JavaScript backdoor onto the victim's computer hidden in a Firefox browser extension.
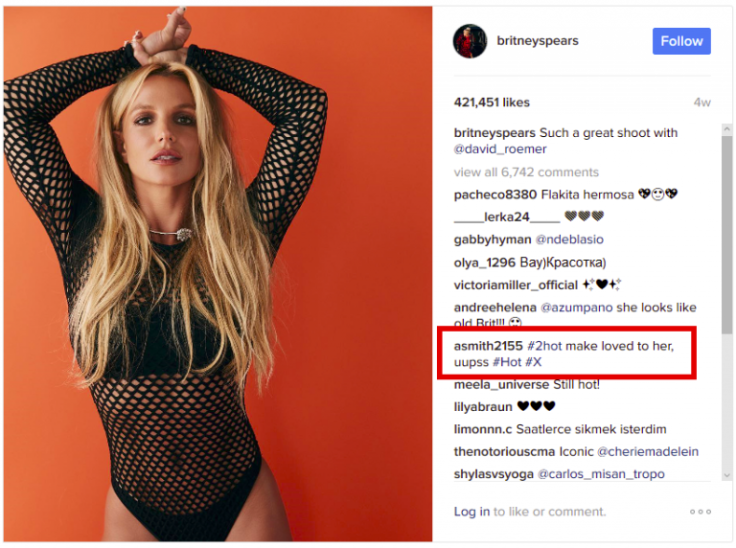
The malware steals data from the target's machine and then it wants to send the data back to the hackers' C&C server, but it needs a URL. In the sample seen by ESET, the malware scans all the comments on photos on Britney Spears' Instagram account and computes a custom hash value.
Only one comment has a hash value of 183, which matches the number that the malicious Firefox extension is looking for.
The comment itself looks innocent enough – it comes from a user called asmith2155 and says, "#2hot make loved to her, uupss #Hot #X" – but if the malware takes the comment and runs it through the computer's regular expression engine (RegEx), it will come back with a bit.ly link that the malware can then use to send stolen data to the C&C server.
ESET believes that Turla is only testing out this technique at this stage, because when the firm's cybersecurity researchers analysed the bit.ly link, it showed that it had only been visited 17 times, which is far too few if it were in operation.
"The fact that the Turla actors are using social media as a way to obtain its C&C servers is quite interesting. This behavior has already been observed in the past by other threat crews such as the Dukes. Attackers using social media to recover a C&C address are making life harder for defenders," ESET's senior malware researcher Jean-Ian Boutin writes in a blog post.
"Firstly, it is difficult to distinguish malicious traffic to social media from legitimate traffic. Secondly, it gives the attackers more flexibility when it comes to changing the C&C address as well as erasing all traces of it. It is also interesting to see that they are recycling an old way of fingerprinting a victim and finding new ways to make the C&C retrieval a bit more difficult."
© Copyright IBTimes 2024. All rights reserved.






