Equation Group: Meet the NSA 'gods of cyber espionage'

Over the last couple of years we have been hearing about ever more sophisticated pieces of malware. From Stuxnet and Flame to Gauss and most recently Regin, all have shown increasing levels of technical prowess and all have been linked in some way with the US government.
These were thought to be the pinnacle of a huge investment in offensive cyber capabilities by the world's wealthiest country.
That was, until we learned about Equation.
Described by Kaspersky Lab, the Moscow-based security company which uncovered it, as "an almost omnipotent cyberespionage organisation", the group has been called the "God of cyberespionage" and may have been operating undetected for almost two decades.
While Kaspersky's report reveals much about the group, it barely touches the surface of the capabilities of what is likely the most highly-prized jewel in the NSA's cyberespionage crown.
Here we look at Equation, its origins, its targets, its attack techniques and how it managed to infect the hard drives of more than a dozen manufacturers - a feat of such technical dexterity that it "exceeds anything [Kaspersky experts] have ever seen before."
What is the Equation group?
In its report, Kaspersky stops short of explicitly pointing the finger of blame at the United States, but leaves enough indicators that readers are left in no doubt as to the identity of this elite hacking squad.
The malware used by the Equation team shares many similarities with the likes of Stuxnet, Flame, Gauss, and Regin, with a worm called Fanny, created to bridge air-gap systems, using two of the same zero-day vulnerabilities which were subsequently used by Student.
In its report Kaspersky says the Equation group malware could have been used to deliver the Stuxnet malware. The group also used a virtual file system which was present in the Regin malware, which leaked Snowden documents show was used by the NSA to infect state-owned Belgian firm Belgacom.
Finally, an advanced keylogger known as Grok is referenced in the Equation team's source code. The name Grok was previously mentioned in another leaked Snowden document about an NSA-developed keylogger of the same name.
It may not be spelled out explicitly, but there is no doubt that the US government is sponsoring the actions of the Equation group.
Why the name 'Equation team'?
Kaspersky Labs experts say the reason they have dubbed this group the Equation team is "because of their love for encryption algorithms and obfuscation strategies and the sophisticated methods used throughout their operations."
How long has Equation group been operating?
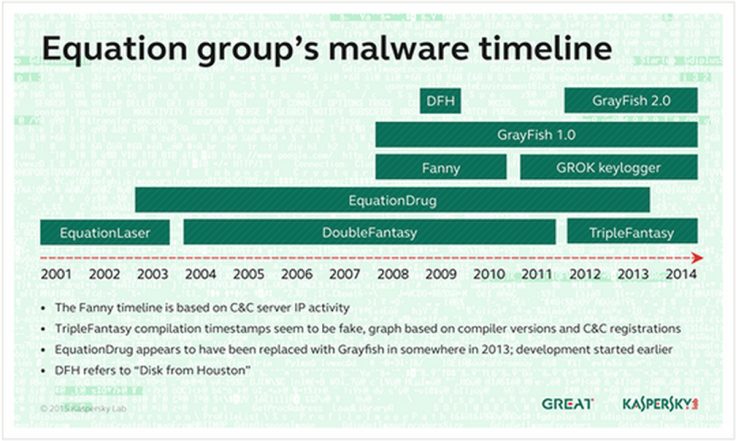
It is difficult to say for certain, but Kaspersky has discovered command and control (C&C) servers which were registered as far back as 1996, suggesting the group could have been operating for almost two decades.
The earliest malware the security company has encountered so far was compiled in 2002, while the group's main C&C servers were registered in August 2001.
During their time in operation, the group worked with other powerful groups, including those developing and deploying Stuxnet and Flame, but Equation was always in a position of authority, as it had access to exploits earlier than the others.
If you look at the timeline of events, it seems that Equation's operations were kick-started around 2001, which would coincide with the beginning of the War on Terror in the wake of the 9/11 attack on New York.
What targets has Equation attacked?

As you can see in the graphic above, Equation has attacked victims in 30 countries and in a wide range of industries. Iran, Russia, Pakistan and Afghanistan are among the most targeted countries.
While Kaspersky has counted only 500 victims worldwide, it assumes the real figure is in the tens of thousands. This is due to the longevity of the group's operation as well as the fact the infections have a self-destruct mechanism which wipes any record from the victim's system.
Targets are chosen with "surgical precision" according to Kaspersky and when the group cannot verify the identity of a target's PC, it used validator malware to first confirm the identity of a target before deploying its more powerful tools.
What piece of malware did Equation develop and use?
While the group has used a range of sophisticated pieces of malware and attack techniques during the course of its operation, Kaspersky has identified six unique pieces of malware which it has tied to the group:
- EquationLaser - An early implant used around 2001–2004 and compatible with Windows 95/98.
- DoubleFantasy - This Trojan is used by the group to confirm the target is the intended one. If the target is confirmed, they get upgraded to a more sophisticated platform such as EquationDrug or GrayFish. Also used as a way of keeping a backdoor open into interesting systems.
- EquationDrug (also known as Equestre) - One of the group's most complex espionage platforms created as an upgrade to EquationLaser. The basic features of the malware give attackers full control over the operating system but if more is needed the attackers can upgrade it with new plugins. Kaspersky found 35 different plugins for EquationDrug and 18 drivers. The malware also has a self-destruct mechanism if it doesn't receive instructions from the C&C server for a period of months.
- TripleFantasy – A full-featured backdoor sometimes used in tandem with GrayFish, this piece of malware appears to be an upgrade of DoubleFantasy, and is possibly a more recent validator-style plugin.
- GrayFish – Put simply, this is the most sophisticated attack platform from the Equation group. It resides completely in the registry, relying on a bootkit to gain execution at OS startup. When the computer starts, GrayFish hijacks the OS loading mechanisms by injecting its code into the boot record. In fact, after infection, the computer is not run by itself any more: it is GrayFish that runs it step by step, making the necessary changes on the fly.
- Fanny - Fanny is a computer worm created by the Equation group in 2008 and distributed throughout the Middle East and Asia. Fanny used two zero-day exploits, which were later uncovered during the discovery of Stuxnet. When a USB stick is connected to a PC the malware automatically executes, allowing Equation to infect air-gap systems - those secure systems not connected to the internet.
Equation infected hard drive firmware
However, above all of these sophisticated pieces of malware, the single greatest achievement of Equation (in the eyes of Kaspersky Lab experts at least) was its ability to infect a hard drive's firmware.

The Equation team were ultimately able to infect hard drives from 12 different companies including Western Digital, Maxtor, Samsung, IBM, Micron, Toshiba, and Seagate - meaning that the vast majority of the world's PCs were compromised.
Equation's rewriting of the firmware sees it create a secret section within the drives which are resistant to even military grade wiping and reformatting.
Despite the power of this attack vector, Kaspersky says Equation used the technique sparingly:
"The Equation group's HDD firmware reprogramming module is extremely rare. During our research, we've only identified a few victims who were targeted by this module. This indicates that it is probably only kept for the most valuable victims or for some very unusual circumstances."
Which operating systems were attacked?
Predominantly the Windows operating system, but Kaspersky says it has seen indications that non-Windows malware does exist. It has seen evidence that a large number of infected users in China are using Mac OS X, suggesting a Mac OS X version of DoubleFantasy also exists.
The security company said that there are indications that the group has been able to compromise Apple's hugely popular iPhone too.
How did Kaspersky discover Equation?
During its investigation of the highly sophisticate Regin malware Kaspersky discovered a computer in the Middle East it dubbed the Magnet of Threats because in addition to Regin, it was also infected by a number of other pieces of malware including Turla, ItaDuke, Animal Farm and Careto/Mask.
The biggest mistake made by the Equation group however was its failure to renew up to 20 of its 300 C&C servers. Kaspersky quickly registered these domains and over the last 10 months used them to sinkhole (redirect) communications with Equation-infected machines.
This investigation led to the uncovering of EquationDrug and by looking for similarities "using statistical analysis and correlation as well as C&C-based pivoting" it identified several other malware families including DoubleFantasy, EquationLaser, Fanny, GrayFish, and TripleFantasy.
Is Equation still in operation?
Costin Raiu, director of Kaspersky Lab's global research and analysis team, told Ars Technica that he was still seeing about a dozen machines that report to the C&C servers from countries that include Russia, Iran, China, and India.
Raiu added that 90% of the servers used by Equation were shut down last year, which could indicate a reaction to the huge trove of leaks from Edward Snowden about the NSA.
Considering the technical skill shown by Equation, it is unlikely that they have been shuttered completely. It is more likely that they are continuing to operate but using new and as-yet-undiscovered piece of malware.
© Copyright IBTimes 2024. All rights reserved.






