Fancy Bears hacker group planned to disrupt Britain's general election
Cybersecurity experts say evidence shows the group is backed by the Kremlin.

The group behind hacks, including an cyberattack on French TV networks that replaced programming with Islamic State (IS) propaganda and the release of World Anti-Doping Agency (Wada) records is preparing attacks on UK targets.
Every British government website and all major British broadcasters, including the BBC, were being lined up for a cyberassault by the Fancy Bears hacker group, aimed at causing chaos and sowing disinformation.
British intelligence officials have indicated that the hacks would have been part of a Russian-backed attempt to disrupt 2015's general election.
According to the Sunday Times, Government Communications Headquarters (GCHQ) moved to defeat the threat, notifying the TV channels and "deploying a capability to protect government networks".
The latest release from the Fancy Bears came on Saturday (23 September). It is the fifth leak in their distribution of Wada records, revealing the confidential medical information of 41 international athletes from Canada, Croatia, Denmark, Germany, Great Britain, Italy, Japan, Serbia, South Africa, Switzerland, Sweden and the US.
The Swiss cyclist and Rio 2016 gold medallist Fabian Cancellara, the US distance runner Galen Rupp, the British cyclist Steve Cummings and the American golfer Patrick Reed were all named in the leak.

As well as Cummings, five more Great Britain athletes had their medical data leaked by the hackers: the sprinter Harry Aikines-Aryeetey, the sailors Sophie Ainsworth and Saskia Clark, rowing's Richard Chambers and the gymnast Nile Wilson.
The data lists the therapeutic use exemptions (TUEs) given to the athletes which allowed them to take drugs that would not be allowed normally under Wada rules.
Who are Fancy Bears?
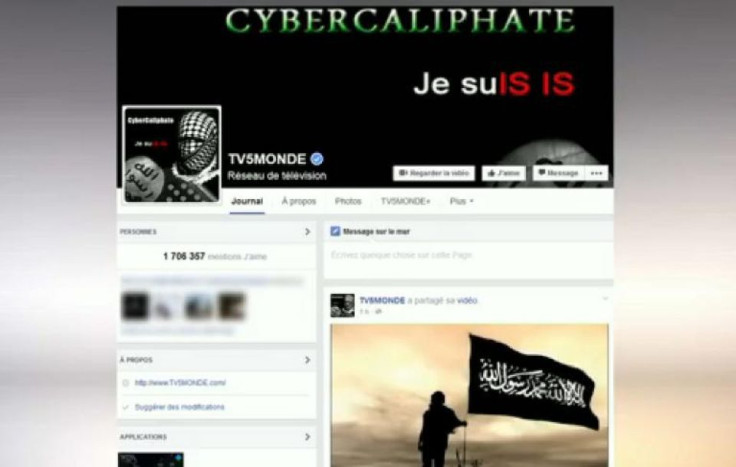
The group has been associated with a wide-ranging portfolio of hacks, including the disruption of French TV network TV5Monde in April last year.
That hack took 11 of its channels off-air and flooded its website and Facebook with IS (Daesh) propaganda.
An attack on the Democratic National Committee (DNC), which resulted in the leaking of 20,000 emails through WikiLeaks, has also been pinned on the group.
Reports have linked the group with a number of different aliases, including APT28, Strontium and the Sofacy Group. Cybersecurity companies Crowdstrike and ThreatConnect have both presented evidence they believe places the group in Russia.
Crowdstrike's Dmitri Alperovitch identifies Fancy Bears as "a Russian-based threat actor, which has been active since the mid-2000s and has been responsible for targeted intrusion campaigns against the aerospace, defence, energy, government and media sectors.
"Their victims have been identified in the United States, Western Europe, Brazil, Canada, China, Georgia, Iran, Japan, Malaysia and South Korea.
"Extensive targeting of defence ministries and other military victims has been observed, the profile of which closely mirrors the strategic interests of the Russian government, and may indicate affiliation with the GRU, Russia's premier military intelligence service".
ThreatConnect has linked Fancy Bears to the cyberattack that heralded Russia's ground assault on Georgia in 2008, when the servers used by the president, the parliament and the foreign ministry were taken down.
"Georgia in a lot of ways was one of the real opening shots in how we see Russia using cyber as an instrument of national power, fully integrated with their national objectives," said Toni Gidwani, chief researcher for ThreatConnect.
"The ultimate sponsor [of Fancy Bears] is the Russian government," says Chris Porter, a manager at cyber-security firm FireEye told the Sunday Times. "Most of the targeting they do is consistent with the requirements of the Russian ministry of defence."
Analysis of Fancy Bears shows it operates almost exclusively during Moscow business hours, and metadata from software left in infiltrated systems is written in Russian.
© Copyright IBTimes 2024. All rights reserved.





