FBI criminal complaint reveals alleged Isis hacker Ardit Ferizi really wasn't that hard to catch

The FBI continues to insist that backdoors are needed and encryption is evil because all the terrorists are using it, but its most recent criminal complaint reveals that terrorists are just like regular consumers – they are all using social media and free webmail.
Ardit Ferizi, 20, is a Kosovo citizen who was arrested by Malaysian police on 15 September following a tip-off from the US government. It is alleged that Ferizi hacked and released personally identifiable information relating to over 100,000 US service members and federal employees, and that he was passing the information onto the extremist group Islamic State (Isis) in August.
Ferizi, who entered Malaysia in August 2014 to study computer science and forensics, is believed to be the leader of a Kosovar internet hacking group called Kosova Hacker's Security (KHS). He will be extradited to the US, where he will stand trial on charges of unauthorised access to a computer, aggravated identity theft and providing material support to a designated foreign terrorist group.
In 2015, the FBI has consistently insisted that encryption is a bad thing, and that tech companies must prevent it as data sent through encrypted channels make it difficult for the Feds to spy on terrorists and foreign governments.
This is all well and good, but the criminal complaint filed by the FBI and a US magistrate judge shows that Ferizi was caught because he used social media, which as we all should know, really isn't that secure.
IP address linked Twitter, Facebook and malware
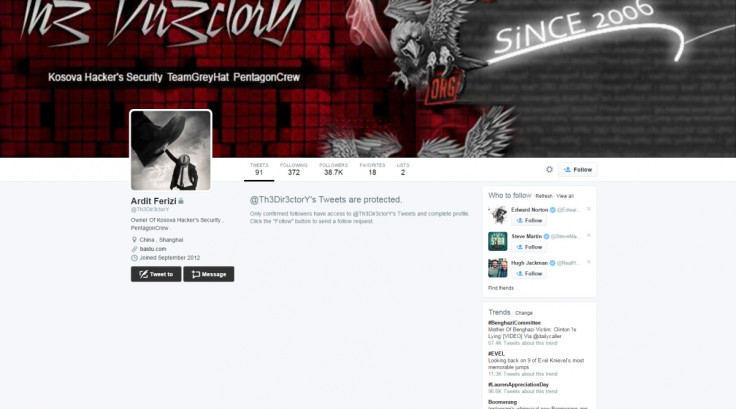
The complaint explains that Ferizi stated his real name on his Twitter account @Th3Dir3ctorY and linked to an article about the KHS where he was interviewed, and even identified himself as the owner of the hacker group.
His Twitter account was tied to a Hotmail account tied to an IP address in Kosovo, and he logged on to Twitter from various internet service providers in Malaysia without encrypting his internet traffic, so his IP address, 210.186.111.14, was clearly visible.
Even better, after the hacker broke into the "victim company" in the US to steal the data, he created an account with the identity "KHS", and the malware was injected using the IP address 210.186.111.14.
When the company finally realised that malware had been implanted in their system to siphon data and removed the malware, he even sent them an email from the email address "khs-crew@live.com", threatening to publish the data relating to every single client on the server unless the company stopped trying to remove his access point and blackmailing them to pay him 2 Bitcoins.
Ferizi also maintained a Facebook account with the username "ardit.ferizi01" that used the same IP address. Rather than the FBI being clever at catching terrorists, this sounds like Ferizi was just really, really, really stupid, similar to the alleged Chinese state-sponsored hacker Ge Xing who posted his entire life on publicly-accessible social media.
"This case is a first of its kind and, with these charges, we seek to hold Ferizi accountable for his theft of this information and his role in IS's targeting of US government employees. This arrest demonstrates our resolve to confront and disrupt IS's efforts to target Americans, in whatever form and wherever they occur," the US Department of Justice said.
No offence, FBI, but at the moment, you're not really helping your case for needing to crack encryption. Good on you for stalking social media accounts just like everyone else.
© Copyright IBTimes 2024. All rights reserved.






