Gmail iOS App Users Vulnerable to 'Man-in-the-Middle' Attacks

It seems that internet search engine major Google is yet to implement security measures to protect user data from getting stolen by hackers.
This revelation stems from the latest study conducted by mobile security firm Laconn, which states that iOS users accessing Gmail from their mobile devices could easily fall prey to cyber-criminals.
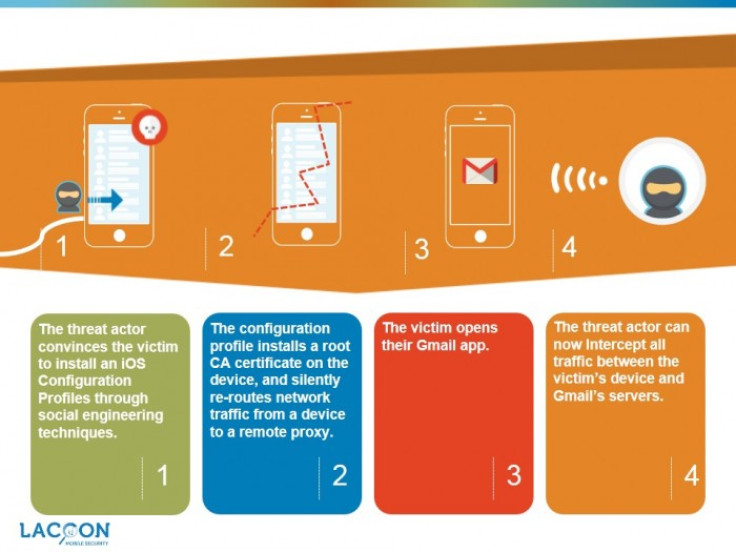
According to Lacoon, vulnerability in the Gmail iOS app activates a potential threat that launches 'Man-in-the-Middle' attacks to view and change encrypted data.
The threat actor involved in the attack has capabilities to impersonate an entire back-end Google server via Secure Socket Layer (SSL) certificate spoofing.
An SSL certificate generally validates encrypted communications between a host system (or an app) and a server, which in this case is Google's web server.
By using spoofed SSL certificates, hackers are in a position to view encrypted conversations with Google servers, and even convert encrypted data to plain text format. This phenomenon allows hackers to exploit and modify user data such as chats, emails and multiple passwords.
"In particular, in iOS, a threat actor can install a configuration profile which contains the root Certificate Authority (CA). The configuration profile is an extremely sensitive iOS file which allows to re-define system functionality parameters such as device, mobile carrier and network settings," states Lacoon in its study report.
"The root CA is what enables the threat actor to create spoofed certificates of legitimate services."
Lacoon's engineers have traced the root cause of the latest Gmail iOS app vulnerability to Google not having implemented the 'certificate pinning' mechanism.
Certificate pinning makes it mandatory for an app developer to code a particular server's certificate within the application. This process detects any communication re-routes by hackers, and recognises discrepancies by matching the server certificate coded within the app and the certificate returned from the intended server.
Without certificate pinning, a threat actor (hacker) is in a position to initiate a Man-in-the-Middle cyber attack and get exposed to confidential data, unknowing of the victim.
Lacoon's study states that Google has implemented certificate pinning within its Gmail Android app.
The best way to prevent users from getting exposed to Man-in-the-Middle attacks is to implement certificate pinning at the earliest by app developers, states Lacoon.
However, for enterprise apps with no certificate pinning, it is advised to check device configuration profiles to verify that these do not incorporate root certificates. Also, enterprises should encourage employees to make use of secure internet channels/ company's VPN when going online.
The absence of certificate pinning in the Gmail iOS app is certainly a cause for concern considering the fact that user privacy is not completely adhered to by technology service providers.
Last week, a research undertaken by US-based Electronic Frontier Foundation (EFF) revealed that Android smartphones (of reputed brands) leaked wi-fi trails of their users, by broadcasting location histories of all places that users have visited.
Currently, Lacoon says that Google has been notified of the Man-in-the-Middle vulnerability issue, and iOS users can expect a fix very soon.
© Copyright IBTimes 2024. All rights reserved.





