Iran: The World's Worst Cyber-Terrorists - For Now

In the last 12 months Iran has emerged as a credible cyber terror threat to the US, targeting several US government agencies, but its lack of skills in this area means that for now, it has been unable to cause significant damage.
Iran is more than five years behind the likes of China, the US and Russia in terms of its cyber capabilities but with the right resources that gap could quickly be bridged especially considering the historical enmity between them and the US.
Iran's rise from cyber-obscurity to becoming a credible - if unsophisticated - threat has been tracked in the latest report from security firm Mandiant, the same company who last year revealed the extent to which Chinese government-funded cyber-espionage was being carried out.
Ever-increasing threat
According to the company's M Trends 2014 report, Iran-based threat actors "pose an ever-increasing threat due to Iran's historical hostility towards US business and government interests."
The report reveals that it has observed "threat actors" based in Iran target the networks of several US government agencies.
"Employees at a US state government office discovered evidence that someone had accessed multiple systems within their network without authorisation. An internal IT department investigation found indications of data theft and unauthorised use of privileged credentials," the report said.
The security company said the data these actors stole "lacked a discernible focus or demonstrated intent" which suggests the attack's purpose was, more than likely, "reconnaissance of the potential target's networks."
Limited capabilities
Attacks originating in Iran are on a very low level of technical skill, with those carrying out the attacking using off-the-shelf tools which are relatively easy to defend against. Mandiant says that 75% of all attacks from Iran were detected by the victim.
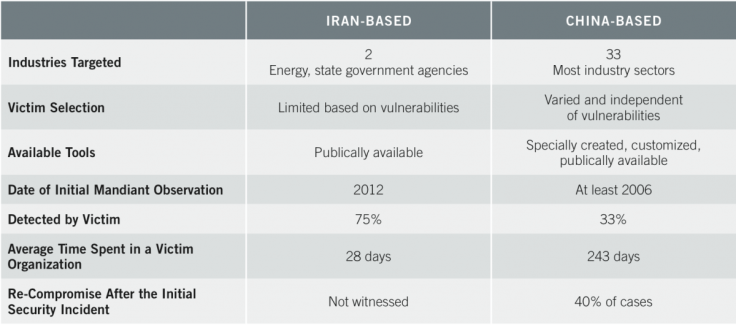
"Mandiant's observations of suspected Iranian actors have not provided any indication that they possess the range of tools or capabilities that are hallmarks of a capable, full-scope cyber actor. They rely on publicly available tools and capitalise solely on web-based vulnerabilities — constraints that suggest these cyber actors have relatively limited capabilities."
Comparing Iran's capabilities in cyberspace to more established players like China and Russia, Mandiant said: "A more capable actor would likely utilise more effective, tailored tools such as a zero-day exploit or a custom-written exploit."
Playing catch-up
Speaking to IBTimes UK ahead of the report's publication, Jason Steer, director of technology strategy at FireEye (which owns Mandiant), said that Iran was currently "five, six, seven years behind China" in terms of cyber capabilities.
"A more capable actor would likely utilise more effective, tailored tools such as a zero-day exploit or a custom-written exploit."
However Steer added that while the current attacks were primitive when compared to the capabilities of China, it would only need Iran to put more resources into their cyber capabilities to bring them quickly up to speed.
Steer said that companies like Vupen openly sell zero-day exploits to the highest bidder, meaning that with the right resources, Iran could quickly become a major player in cyberspace.
Stuxnet revenge
The report says that attacks from Iran focused on just two sectors - government agencies and the energy sector.
The report says that Iran is widely believed to have been behind the August 2012 malware infections that targeted the networks of two energy companies - Saudi Aramco and the Qatar-based RasGas.
It is believed the attacks were sponsored by the Iranian government after it was revealed that the Stuxnet worm - developed by the US and Israel - was used to try and damage the uranium enrichment plant at Natanz in Iran.
While Mandiant points out that on-going diplomatic negotiations between Iran and Western countries over Iran's nuclear program could have an impact on just how quickly the country increases its cyber capabilities, the increasingly open discussions about offensive cyber capabilities which other countries possess could encourage Iran to step up its efforts in this area.
© Copyright IBTimes 2024. All rights reserved.






