How the Mafia is Ruling the World Wide Web
The murky world of organised crime is associated with guns, drugs, violence and old-fashioned beliefs that dates back centuries to the mafia organisations such as the Cosa Nostra and the Camorra.
It is less associated with the high-tech world of computer science, botnets and cybercrime, but organised crime groups are among the main players in this new criminal frontier, raking in hundreds of millions of dollars without ever having to lift a gun or strike a menacing pose.
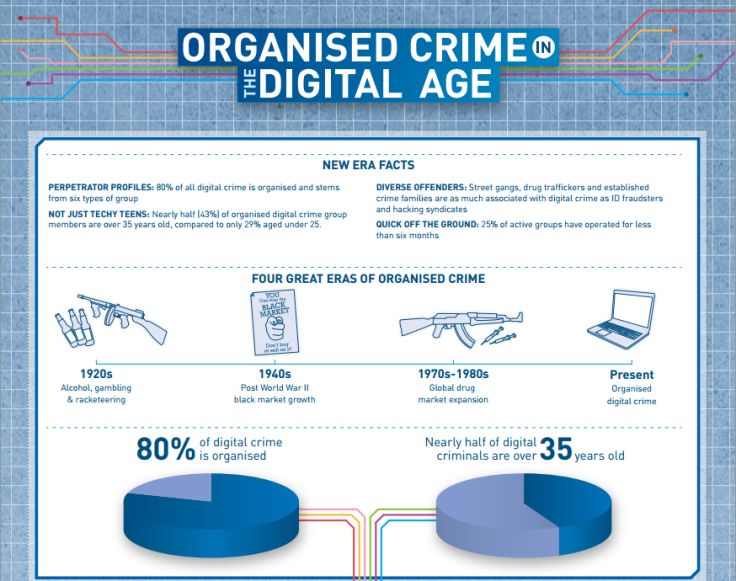
A recent survey from London Metropolitan University puts the figure as high as 80 percent of digital crime stemming from organised crime gangs and it's not just the up-and-coming criminals who are getting involved, with 43 percent of those involved over the age of 35.
One of the main avenues these criminal organisations are using to perpetrate cyber crime is through the use of botnets. Last weekend, Microsoft and a group representing 4,400 financial institutions, raided two non-descript offices in Illinois and Pennsylvania in order to disrupt a financial botnet known as Zeus.
And while they were successful in disrupting this particular version of Zeus, there are thousands of versions of Zeus in operation around the world and the trying to bring them all down will be virtually impossible because of the inherent nature of this type of pernicious software.
Botnets have been around in various forms since 2004 and all work in the same basic way. A computer scientist creates a piece of code which infects a number of PCs around the globe. These PCs then send out spam emails to other users and so the group of infected PCs grows - at times exponentially. The owner of the code is then able to direct this group of infected PCs, or botnet, to then do their bidding.
Two of the largest and most well-known botnets, called Kelihos and Waledac, were both used to send out huge amounts of spam, and so big was the Kelihos botnet network that when it was taken down in 2010, the worldwide volume of spam dropped by 50 percent immediately.
"A botnet can do anything. You can have a botnet that sends spam. You can have a botnet like Zeus that steals financial information. But the important thing is that a botnet can infect loads and loads of different users and control them all to do the same thing. So you get a scale that is kind of staggering. If you can tell nine million people around the world to do one thing for you it definitely changes the game in terms of what this can do as opposed to just crashing my computer," Wade Williamson, security Analyst with Palo Alto Networks told us this week.
Financial botnet
Zeus is a financial botnet, which is a new type of botnet which doesn't just send out spam from your email account, but searches your computer for financial data and records every keystroke associated with it, thereby capturing your usernames and passwords.
The Zeus botnet has been in existence since 2006 and was created by a "very, very skilled computer scientist," according to Williamson. The creator of the code then sells it on to people who package it up as a kit to sell to organised crime gangs who use their own servers to set up the botnet.
The current going-on rate for a Zeus kit is between $2,500 and $3,500, which is a relatively small outlay for a potentially huge return and for the crime gangs who are typically buying these kits, it is a drop in the ocean.
According to Williamson, the Zeus family of malware has been responsible for well over $100m of fraud since it was first tracked, with individual cases running into tens of millions, and one school district in the US having up to $4m stolen from them by a Zeus botnet. It is "one of the most successful financial botnets ever."
Williamson said that the criminal gangs operating the Zeus botnet would have to have a level of computer skills: "It definitely requires a level of expertise, it definitely requires a level of understanding of how law enforcement works and finds botnets, but it is a different level of expertise than it takes to build the thing."

The people who build these botnets will try and remove themselves from the situation, preferring to sell the code to those looking to commit the crime. However, they are still liable to be prosecuted and therefore are fiercely protected by the criminal gangs.
"Whether you directly work for organised crime or not, you are talking about some of the most valuable assets of a criminal enterprise. If you are employed by a criminal gang, you are probably the crown jewel of that criminal gang and they will protect you as much as possible," Williamson said.
However it is not just the Zeus botnet that the security industry, technology companies and law enforcement agencies are trying to combat. Earlier this year Palo Alto Networks detected a new variant of the Waledac botnet, which Microsoft had taken down in 2010.
However this was not the same code and the new botnet had similarities with the old Waledac code combined with the old Kelihos code. It was also no longer just a spamming botnet, but also now records passwords you type into your computer.
According to Williamson, it is "very, very savvy at stealing passwords. Passwords from your browser accounts, passwords from email, from FTP and from Bitcoin. When you can have this massive botnet that has previously grown into the millions and now it is scraping passwords out of every device it infects and it can start figuring out that based on this IP address, it's this company where this device lives and we now have passwords inside this company, that becomes a very different animal altogether."
While it is difficult to say how big the new version of Waledac is currently it has grown quickly from first being spotted in early February.
"Insanely Complicated"
The task of taking down a botnet is "insanely complicated" according to Williamson. It requires you to co-ordinate across multiple jurisdictions, multiple countries and takes a huge amount of research. In the same way a weed will continue to grow back unless you get rid of it completely, botnets like Zeus will continue to propagate unless you excise all servers controlling the distributed network of computers around the globe.
"Microsoft is one of the few technology firms that has a worldwide vision and breadth to go to seven different countries and talk to seven different law enforcement agencies and say these are all the servers around the world we need to take down. They're one of the few entities that can pull that off."
However, another security analyst, Rik Ferguson from Trend Micro, believes that Microsoft acted in haste by not working in conjunction with law enforcement agencies. "All 39 of the online handles mentioned in the court submission are now fully aware that they are under active investigation and have the chance to "disappear", probably to resurface elsewhere and carry on business as usual," Ferguson said in his blog yesterday.
Ferguson goes on to point to the successful dismantling of the Esthost botnet last year which was the result of a six year operation, and was the proper model of how such an investigation should be carried out in conjunction with law enforcement, resulting in the arrest of the criminals involved. "Long term law enforcement success should not be sacrificed on the altar of marketing initiatives."

Whatever the thinking behind this action, a botnet takedown remains the exception to the rule. And it remains unclear whether the people behind the original Waledac and Kelihos botnets, who were not arrested in 2010, are the same people behind the new Waledac botnet.
Williamson also sounded a word of warning regarding the future of this type of malware. "Where it gets really scary is when you get into mobile devices and [they] are very open to this kind of threat. We are starting to see malware showing up in mobile devices, but mobile botnets in particular are pretty scary because you are talking about devices that don't have a firewall, have very limited AV [anti-virus software] and are always connected to a network."
We recently spoke to Cesare Garlati, Senior Director of Consumerisation at Trend Micro, who pointed out just how insecure our smartphones really are. Consider that botnets have flourished in environments such as laptops and desktop PCs which have anti-virus security on them and are only connected to the internet intermittently and you soon realise the potential threat which is posed by the mobile phone environment.
"You project that [botnet growth on PCs] to your phone, which has far less security on it and is permanently connected through a carrier of some kind, that is an area where I would expect to see a lot of growth because there is an infrastructure there that is really primed for the way botnets work, and we don't see it there nearly as much as we do say for laptops or desktops."
While this all sounds very scary, Williamson says there are a number of things users should be doing to protect themselves. "It still comes down to clicking on a bad link somewhere so you should keep a good reputable anti-virus updated on your machine."
But he says you should also be very wary of any solicitation coming from an untrusted or even a trusted source. "You get something [email] from your bank, don't click on anything from your bank that says it's from your bank. Go back to your browser, type in the address for your bank and go there directly."
He also says that credit monitoring, where your bank contacts you once something unusual happens in your account is a good thing. While it may be annoying, it will at least let you know immediately when something happens so you can tell if it's something that you have done or not.
According to the survey by the London Metropolitan Museum, we have now entered the fourth great era of organised crime, called Organised Digital Crime. While it may not sound as 'romantic' as the old world mafia, and we may never see films directed by Martin Scorcese about botnets and the Cosa Nostra in the virtual world, it is clear from the size and pervasive nature of these botnets that they are here to stay and will be difficult to police.
© Copyright IBTimes 2024. All rights reserved.






