Spammers using Facebook messages to spread the notorious 'Locky' ransomware
Scam spreads a malware downloader called Nemucod hidden in an .svg file.

Spammers are reportedly using Facebook's instant messaging (IM) feature to spread malware – including a notorious strain of ransomware called Locky – to unsuspecting users of the world's most popular social media platform.
The spam campaign, highlighted in a blog post by security researcher Bart Blaze on 20 November, was using the IM feature to spread a malware downloader called Nemucod hidden in an .svg file extension. It was reportedly able to easily bypass Facebook's spam filters.
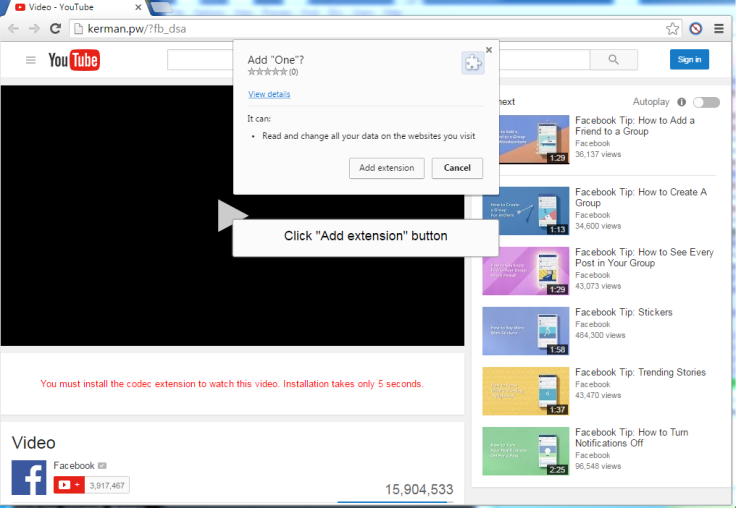
The rogue image – which will open on any modern browser – contained a "heavily obfuscated script" that redirected the victim to a fake website that mimics YouTube. The user would then instantly be prompted to install an additional extension to view a 'video'.
Upon analysis, the researcher found that – if clicked – the extension would give the spammer the ability to "read and change all your data on the websites you visit." Additionally, a separate researcher, Peter Kruse, also encountered the bug and said it was spreading Locky as the payload.
Ransomware like Locky, once deployed on a victim's computer, will lock down sensitive files and demand a financial fee for their return – usually in the form of the Bitcoin cryptocurrency. By spreading via email phishing, it has hit hospitals, schools and businesses across the world.
"As always, be wary when someone sends you just an 'image' – especially when it is not how he or she would usually behave," Blaze said. He added: "Even though both Facebook and Google have excellent security controls/measures in place, something bad can always happen."
"Remove the malicious extension from your browser immediately. Additionally, run a scan with your antivirus and notify your friends [if] you sent a malicious file."
Fraser Kyne, a chief technology officer at security firm Bromium, said: "People are far more likely to click on a link or download something if it looks like it came from a friend. You would be forgiven for writing [the spam] off as a low risk, but the real threat comes from the use of Facebook as a vehicle.
"Given that so many users check their Facebook at work, there's a big risk of this attack bleeding through into the enterprise. The best thing for businesses to do to minimise their risk is to ensure employees are aware of this scam.
"As with most attacks of this ilk, the bad guys just need a handful of their victims to fall for their ploy in order to be successful, and the self-propagating nature of this particular scam will help to ensure it continues to gather momentum even if most people smell a rat from a mile away."
Locky – a relatively new form of ransomware – was discovered in the wild by Palo Alto Networks on 16 February this year. Initially, it spread via Microsoft Word macros, however experts found it quickly evolved into using Javascript-based attachments to circulate.
IBTimes UK contacted Facebook for comment however had not received a response at the time of publication. Security researcher Bart Blaze said it has been informed of the issue.
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG
— peterkruse (@peterkruse) November 20, 2016
© Copyright IBTimes 2024. All rights reserved.






