Syrian opposition battle plans stolen by Lebanese hackers using Skype

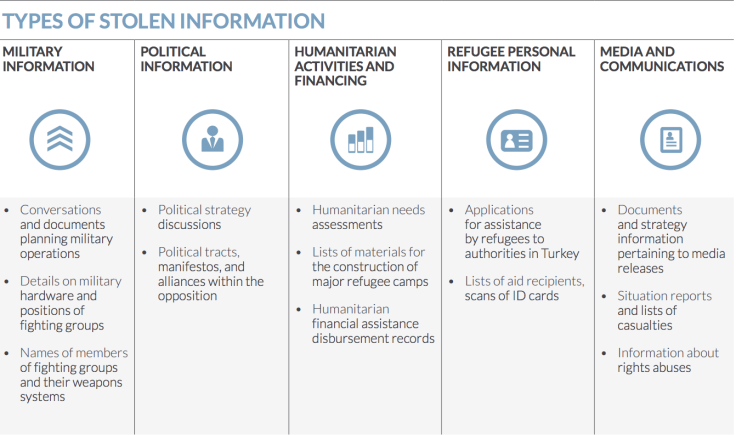
Information on the names, dates of birth, blood type, phone numbers and even the brand of gun carried by hundreds of Syrian opposition fighters have been stolen by a hacker group with possible ties to Lebanon.
The unknown group of hackers stole a cache of critical documents and Skype conversations revealing the Syrian opposition's strategy, tactical battle plans, supply needs, and troves of personal information and chat sessions between November 2013 and January 2014, research company FireEye has discovered.
In a report entitled Behind the Syrian Conflict's Digital Front Lines, FireEye researchers reveal the hackers stole information relating to a wide range of individuals including: an opposition leader who was planning an upcoming battle; a high-profile defector who was formerly a high-ranking officer within Assad's security service; a humanitarian working for a charity based in Turkey; and a media activist who was working from inside Syria with a local media centre.
The group was able to hack its victims' computers by spreading malware which was embedded within images it shared over Skype.
Fake 'femme fatale'
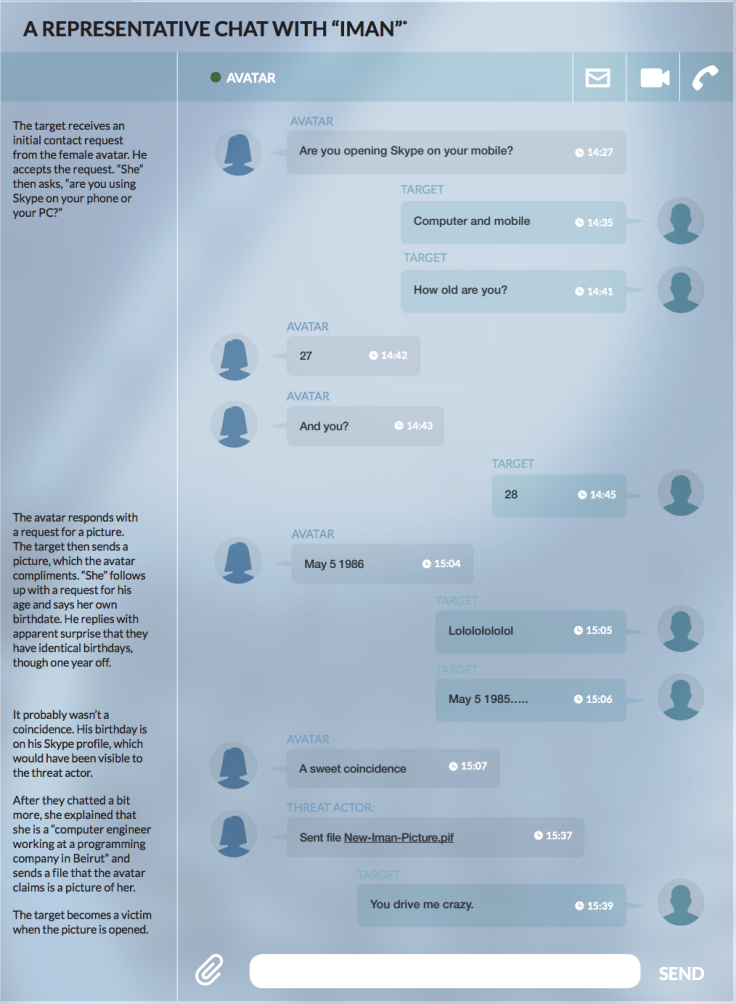
The hackers would pretend to be a seemingly sympathetic and attractive women in conversations with their victims on Skype. As the conversations progressed, the "femme fatale" would offer up a personal photo, laden with malware and developed to infiltrate the target's system.
When the victim opened the file it would display a picture of a woman, but silently in the background the DarkComet malware was installed, giving the hackers remote access to the victims' computer.
The hackers managed to weave a question into the Skype conversation prior to sending the malware-laden image to ascertain whether their targets were using a Windows PC or Android smartphone, and tailor the malware accordingly.
In order to avoid being caught out, the hackers created a Facebook profile for their fake female avatar which used the same picture and was filled with pro-opposition rhetoric. The hackers also maintained a fake Syrian opposition website which purported to support the rebels but which in fact hosted the same DarkComet malware.
In total the hackers were able to breach the accounts of 64 victims, with most based in Syria or Turkey, stealing 7.7GB of data including 12,356 contacts, 31,107 conversations, and 240,381 messages.
It is unknown if any of the stolen information has been used to actively target opposition fighters or thwart opposition attacks.
Syrian Electronic Army
The hackers' pro-Assad bias would immediately bring to mind the Syrian Electronic Army (SEA), a group of hackers who have been active for the last couple of years. Predominately this group has been targeting media organisations (including IBTimes.com) which it believes are showing bias for the opposition.
However, the methods used in these attacks would suggest the SEA are not involved.
FireEye has not specifically named the group of hackers behind the attacks, but multiple references to Lebanon were found during the company's research:
"We observed a user in Lebanon upload what appears to be two test versions of malware used to target opposition elements. The avatars, social media seeding, and fake opposition website are also filled with references to Lebanon.
"During chats, for example, the female avatars often state that they are in Lebanon and demonstrate familiarity and interest in talking about issues there. Social media pages suggest that the avatars are refugees in the country, or are Lebanese."
FireEye discovered another link to Lebanon when it found a reference to a three-day hacker training course in the country in 2012 that described "eerily similar methods" to those being used in the attacks described in its report.
While this group is unlikely to be sponsored directly by the Lebanese government, it is a possibility that it is linked to the Hezbollah, which has long been an ally of Al-Assad's Ba'ath government and has helped the Syrian government during the Syrian civil war.
FireEye concluded:
Unlike other threat activity that we have profiled, this is not just cyber-espionage aimed at achieving an information edge or a strategic goal. Rather, this activity, which takes place in the heat of a conflict, provides actionable military intelligence for an immediate battlefield advantage. It provides the type of insight that can thwart a vital supply route, reveal a planned ambush, and identify and track key individuals. This intelligence likely serves a critical role in the adversary's operational plans and tactical decisions. However, this tactical edge comes with a potentially devastating human cost.
© Copyright IBTimes 2024. All rights reserved.






