What is Coldroot? Nasty undetectable Mac malware can steal passwords, remotely control your computer
Once activated, the malware features various capabilities from recording and stealing passwords to remotely viewing the desktop and shutting down the system.

Security experts have uncovered a malicious strain of malware dubbed "Coldroot" that is still undetectable by most antivirus software despite being uploaded to GitHub nearly two years ago. The remote access trojan (RAT) has been freely available on GitHub since 30 March, 2016 and was apparently "made with love" to "play with MAC users".
Patrick Wardle, chief research officer at Digita Security, said the malicious code was also put up for sale by its apparent author "Coldzer0" on underground markets since 1 January 2017 who offered customers ways to customise the malware as well.
According to a video posted by Coldzer0, Coldroot is a cross-platform RAT that can used to target MacOS, Windows and Linux systems, Wardle noted in a blog post published on Saturday (17 February).
Despite being available for download for years, none of the antivirus engines are able to detect it as malicious when he initially submitted the sample, according to test service VirusTotal.
At the time of writing, the RAT triggered a "malicious" warning on just 18 out of 60 antivirus tools.
The unsigned RAT itself masquerades as a document and claims to be an Apple audio driver titled "com.apple.audio.driver2.app".
When a user clicks on it, a standard authentication prompt pops up that requests their MacOS credentials. Once entered, the RAT modifies the privacy database TCC.db, giving the malicious software accessibility rights to perform system-wide keylogging.
The malware also maintains persistence on an infected system by installing itself as a launch daemon, which means the malicious code automatically launches every time the compromised system is rebooted.
"Behind the scenes, the application will automatically beacon out to a server. While creating a network connection is itself not inherently malicious, it is a common tactic used by malware - specifically to check in with a command & control server for tasking," Wardle said.
Once activated, the malware can record and steal passwords, list, rename and delete files, execute or kill processes, upload and download documents, remotely view the desktop in real time and even shut down the system.
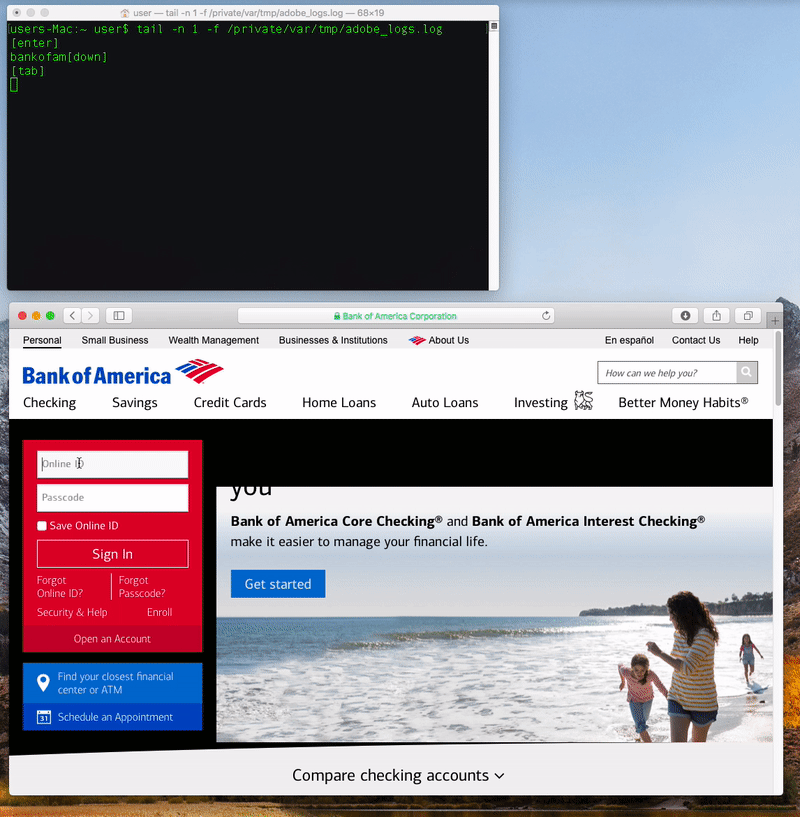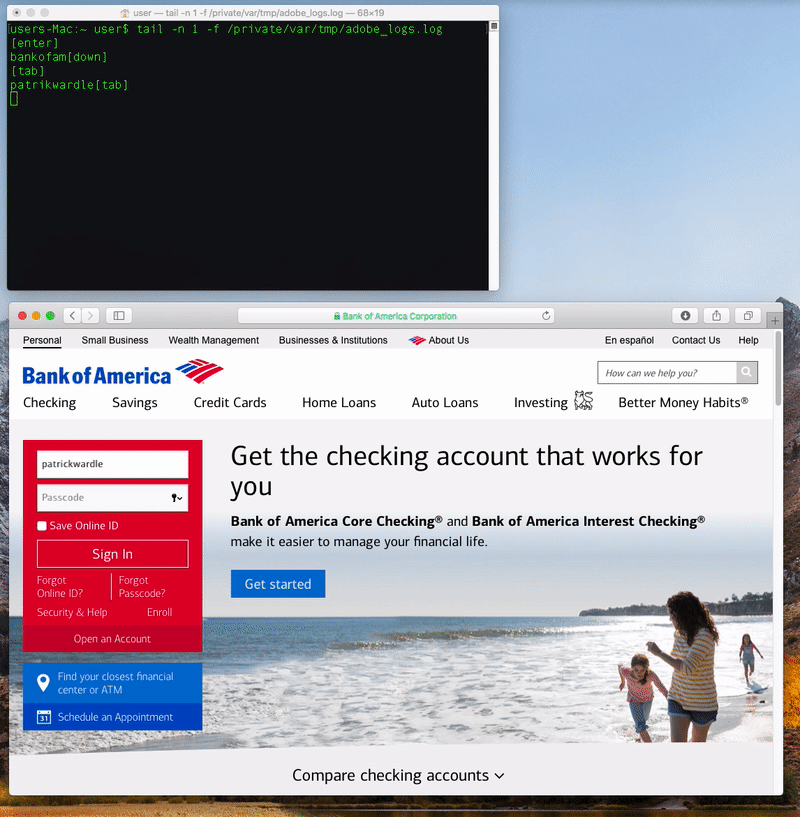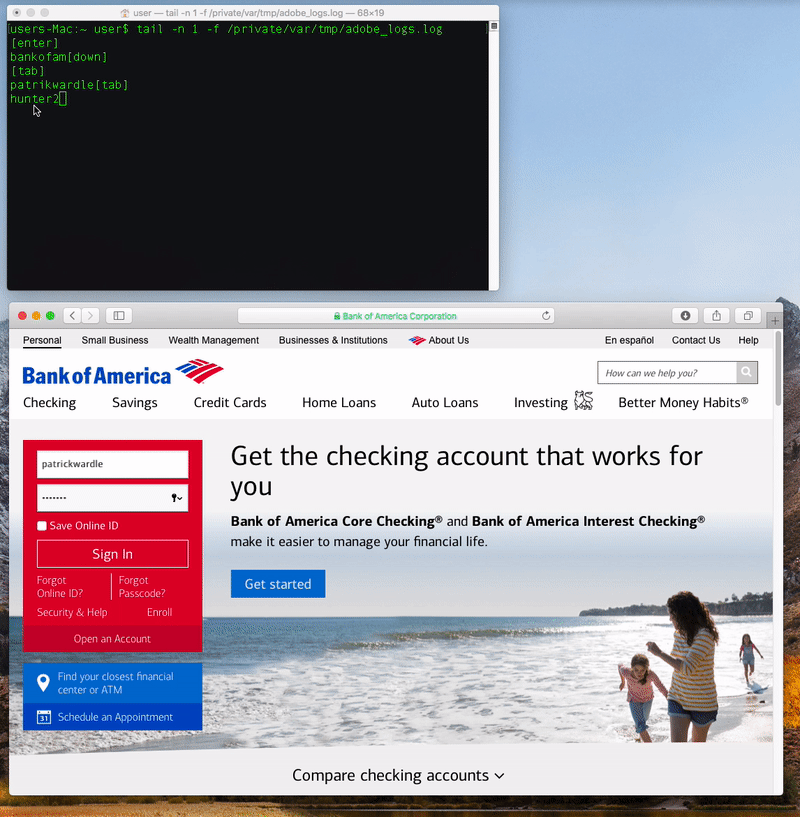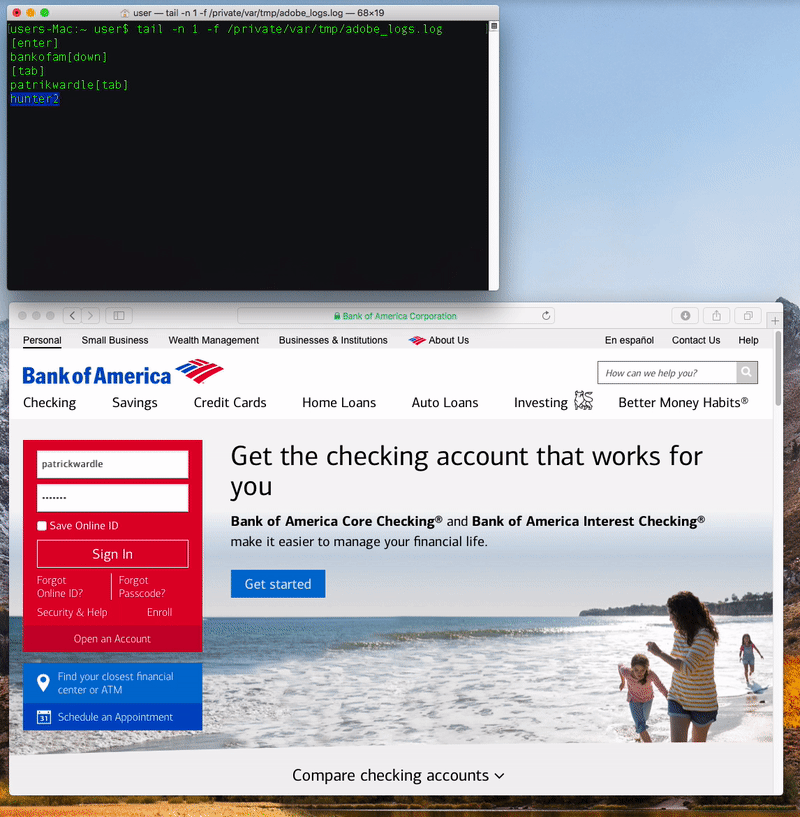
"It should be noted that if no command or tasking is received from the command & control server, the malware will simply continue beaconing... interestingly, sending the name of the user's active window in each heartbeat," he said.
Wardle noted that the script may fail on newer operating systems such as MacOS High Sierra since Apple now protects TCC.db through its System Integrity Protection (SIP).
Wardle said the malware is "not particularly sophisticated" but is rather "feature complete".
"Moreover, it is a good illustrative example that hackers continue to target macOS!" he added. "And remember if you want to stay safe, running the latest version of macOS will definitely help!"





