What is SpriteCoin? Fake cryptocurrency scam delivers ransomware, installs more malware if you pay up
The threat dubbed "SpriteCoin" has been advertised on forums as the hottest new cryptocurrency.

Security researchers have discovered a new strain of ransomware that tricks users with the lure of the next hot cryptocurrency that is "sure to be a profitable coin". According to researchers from Fortinet's FortiGuard Labs, the threat dubbed "SpriteCoin" has been advertised on forums as a new cryptocurrency, luring people to download a wallet to tap into the "new cryptocurrency written entirely in JavaScript".
People who do download and run the .exe file are prompted to enter a wallet password. They are then notified that the file is downloading the blockchain. However, the ransomware is actually secretly busy running its encryption routine and encrypting the infected computer's files.
During this process, the user's Chrome and Firefox browser credentials are also harvested and stored using an embedded SQLite engine and sent to the attackers' Tor website via POST requests.
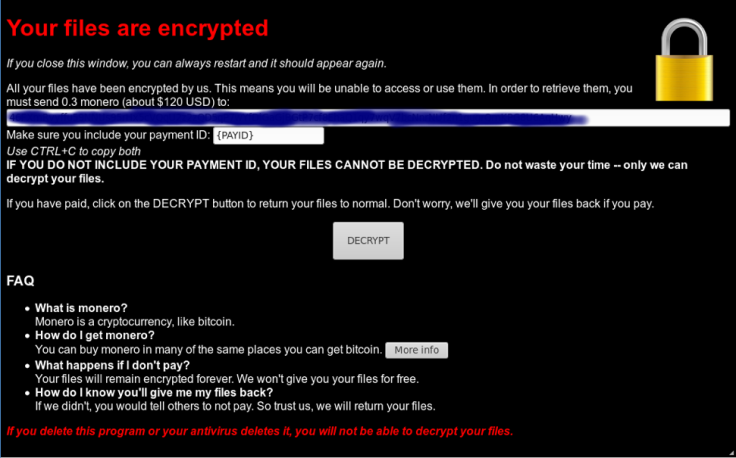
Victims are met with a ransom note that demands they pay 0.3 Monero (currently about $93, £66) to get a decryption key. The hackers also provide information about what Monero is, how to purchase it and how to pay up.
"Do not waste your time - only we can decrypt your files," the ransom note reads. "If you have paid, click on the DECRYPT button to return your files to normal. Don't worry, we'll give you your files back if you pay.
"If you delete this program or your antivirus deletes it, you will not be able to decrypt your files"
To add insult to injury, users that do decide to pay and obtain a decryption have a new malicious executable identified as "W32/Generic!tr" delivered to them. The additional malware program is capable of activating web cameras, harvesting certificates, parsing keys and likely "leaves the victim more compromised than before".
In this case, however, researchers believe "the intent was not just about money".
"What we infer is that the intent is not about the amount of money, but possibly about proof of concept or testing new delivery mechanisms, and to see how many people would fall for it," senior security researcher at Fortinet, Tony Giandomenico, told ZDNet.
"This is very similar to when attackers would test to see how effective or fast a worm would spread before really launching it. This could be the same concept."
The discovery comes as cybercriminals increasingly tap into cryptocurrency as lures, payment options or attacks such as cryptojacking with the hype surrounding digital currencies worldwide.
"The allure of quick wealth through crypto-currency seems to be enough to trick unsuspecting users to rush toward the wallet app du jour without consideration," the Fortinet researchers said.
"Malware authors have done their homework to ensure higher success rates. They understand that most people don't back up their systems regularly, but if someone should perform a shadow volume or similar backup, they have logic built into the malware to defeat it. Instead, a simple offline back up of important files will save a lot of time and frustration."





