GCHQ and NSA Repeatedly Tried and Failed to Crack Tor Network
Top secret documents leaked by whistleblower Edward Snowden show the NSA and GCHQ have both repeatedly tried and failed to target the Tor network, which enables anonymous web browsing.

According to a top secret presentation called 'Tor Stinks' leaked by former NSA contractor Snowden, the US National Security Agency says its agents will "never be able to de-anonymise all Tor users all the time," and that even with manual analysis of their online actions, the NSA admits it can only "de-anonymise a very small fraction of Tor users."
Tor, originally standing for The Onion Router, is a system which can be used to create online anonymity by directing web traffic through a worldwide volunteer network consisting of thousands of relays, concealing the user's location and their browsing history from anyone trying to watch them.
Such anonymity meant users could buy illegal drugs, weapons and even hitmen from the SIlk Road website without fear of being caught.
The application is used by journalists, activists, and campaigners as well as terrorists and criminals around the world to maintain the privacy of their communications. According to the Guardian, Tor receives around 60% of its funding from the US government, primarily the State Department and the Department of Defense, which houses the NSA.
One presentation refers to making efforts to "shape", or influence, the future development of Tor in conjunction with Cheltenham-based GCHQ.
Attempts to monitor Tor's users are carried out by the NSA's application vulnerabilities branch, which is part of the systems intelligence directorate (SID), where the majority of NSA employees work. Here, they collect data from communications systems around the world, as has been well documented in recent months by the leaks of Snowden.

King of high security
One NSA presentation describes Tor as "still the king of high secure, low latency internet anonymity...there are no contenders for the throne in waiting."
According to the leaked presentation, a successful technique used by the NSA is to exploit the Tor browser bundle, the collection of programmes designed to make it easy for users to install Tor onto their computer. The trick discovered by the NSA identifies Tor users online, then executes an attack against their Firefox web browser (used by the Tor bundle) to capture more information and communications sent to and from their computer.
Because of the unique way Tor hides its users, their activity across the internet is easy to spot - even though their identity cannot be found.
The NSA presentation explains how, because of the agency's vast monitoring of the internet, it can sift through web traffic to spot the heavily re-routed Tor connections.
Computer security expert Bruce Schneier writes: "The very feature that makes Tor a powerful anonymity service, and the fact that all Tor users look alike on the internet, makes it easy to differentiate Tor users from other web users. On the other hand, the anonymity provided by Tor makes it impossible for the NSA to know who the user is, or whether or not the user is in the US."
FoxAcid
Once spotted, the anonymous Tor user can be redirected by the NSA from one set of secret servers to another, called FoxAcid, where the user's computer can be infected, causing the target computer to call back to the FoxAcid server, which then performs repeated attacks to make sure the computer is compromised long-term and continues to provide information back to the NSA.
According to the leaked documents, the NSA discovered a vulnerability in three older versions of the Firefox browser. Called Egotistical Giraffe, the trick would exploit Firefox 10.0 ESR - the version used in the Tor browser bundle until recently - but this was inadvertently fixed when Mozilla removed the EX4 library which contained the vulnerability.
But the NSA remains confident that a new exploit could be found against newer versions of the software.
Turmoil
Once a Tor-using target has been found, the NSA then relies on what Schneier calls its "secret partnerships with US telecoms companies" and uses secret servers placed along the backbones of the internet to reroute targets.
Codenamed Quantum, the servers can react more quickly than those delivering the website the target is trying to visit. By exploiting this speed difference, the NSA's servers can take the target's request for a website, then return an impersonating site before the legitimate page can respond, thereby tricking the target's browser to visit a FoxAcid server without the user being aware.
This same technique is used by the Chinese government to block its citizens from reading censored material, the Guardian claims.
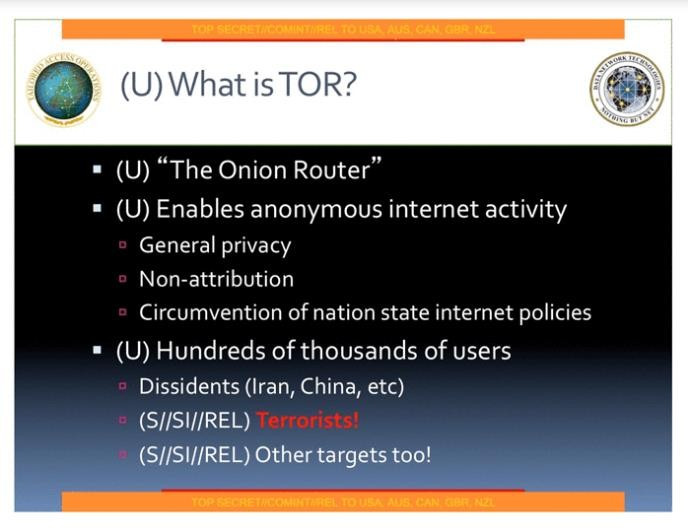
Terrorists
Another leaked NSA presentation explains who the agency believes would use the Tor browser; it lists "Dissidents (Iran, China etc)...terrorists...other targets too"
Problems in tracking Tor users, according to the presentation slides, include: "Flash in a no-no...Tor explicitly advises against using any addons or extensions other than TorButton and NoScript".
© Copyright IBTimes 2025. All rights reserved.






















