Gauss: The Latest Cyber Weapon in the Stuxnet, Duqu and Flame Saga
Security experts have discovered the latest high-profile cyber-security weapon called Gauss, which is based on the Flame platform and targeting users in Lebanon.

Gauss is the latest highly-complex piece of malware targeting the Middle East and created by the US and Israeli governments. As well as monitoring users' web browsing history, and stealing passwords, Gauss has also been found to steal banking credentials.
Discovered by security experts at Kaspersky Labs, the new cyber surveillance tool, which is described as a banking trojan which "carries a warhead of unknown designation", was developed by the same people behind the highly complex Flame virus, discovered earlier this year.
"Gauss is a complex cyber-espionage toolkit created by the same actors behind the Flame malware platform," the Global Research and Analysuis Team at Kaspersky said in a blog post.
It was revealed by New York Times journalist David Sagner that Stuxnet, another high-profile cyber weapon targeting an Iranian nuclear facility, was jointly developed by the US and Israeli governments.
It was also revealed two months ago that Flame shared a common heritage with Stuxnet, therefore implicating the US government in the development of that virus too.
This latest discovery would suggest that Gauss is the latest in a range of highly-sophisticated cyber weapons developed by the US government under its operation codenamed Olympic Games.
Gauss however marks the first time that apparently nation-state malware has been discovered stealing banking credentials, something normally the preserve of malware distributed by criminal hacking groups.
"When you look at Stuxnet and DuQu, they were obviously single-goal operations. But here I think what you see is a broader operation happening all in one," Roel Schouwenberg, senior researcher at Kaspersky Lab told Wired.
Lebanon
The vast majority of Gauss victims are located in Lebanon, but there are also victims in Israel and Palestine. In addition to these, there are also victims in the US, United Arab Emirates, Qatar, Jordan, Germany and Egypt.
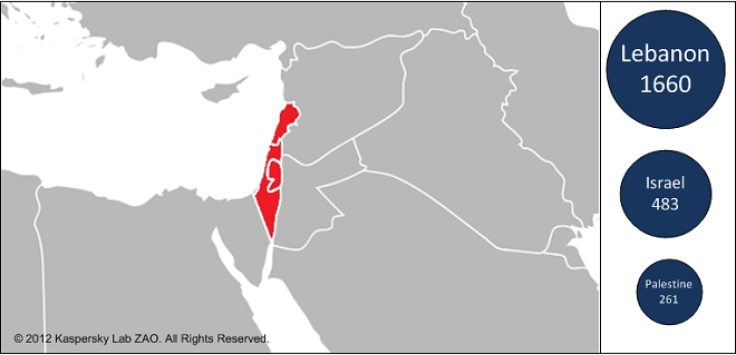
The Russian security company estimates that tens of thousands of Windows PCs have been infected. However the malware is currently in a dormant state, with the remote command and control servers having been shut down last month.
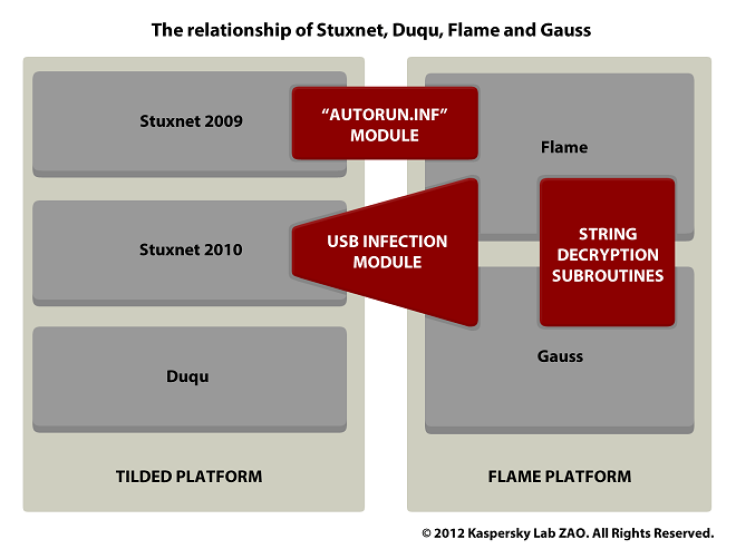
Analysis has shown that Gauss has been in operation since August/September 2011, around the same time as the discovery of the Duqu malware was announced publicly.
"We do not know if the people behind Duqu switched to Gauss at that time but we are quite sure they are related: Gauss is related to Flame, Flame is related to Stuxnet, Stuxnet is related to Duqu. Hence, Gauss is related to Duqu.," Kaspersky said.
Just like with Flame, it is still unclear just how victims' PCs get infected with Gauss. "It is possible the mechanism is the same as Flame and we haven't found it yet," Kaspersky said.
State-sponsored
Gauss is not targeting a specific industry or businesses but there is sufficient evidence to categorically claim this is a nation-state sponsored attack.
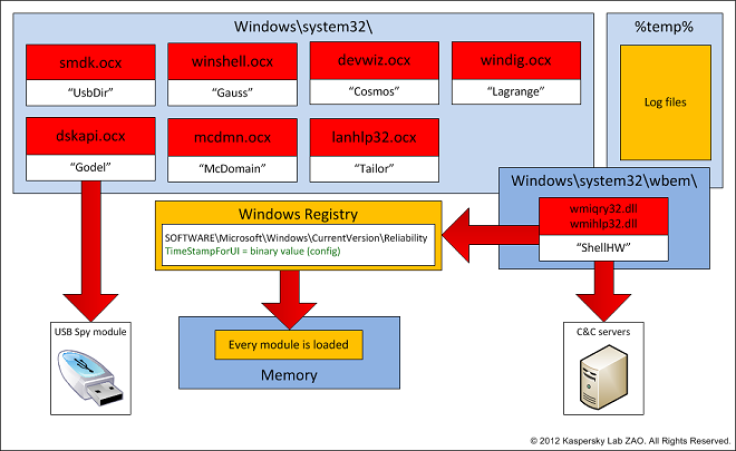
The Gauss virus is highly modular according to Kaspersky and supports a range of functions which a remote operator can control. Among the functions it can carry out include:
- Intercept browser cookies and passwords.
- Harvest and send system configuration data to attackers.
- Infect USB sticks with a data stealing module.
- List the content of the system drives and folders
- Steal credentials for various banking systems in the Middle East.
- Hijack account information for social network, email and IM accounts.
These modules have internal names which appear to pay tribute to famous mathematicians and philosophers, such as Kurt Godel, Johann Carl Friedrich Gauss and Joseph-Louis Lagrange.
According to Kaspersky, the module named "Gauss" is the most important as it implements the data stealing capabilities and this is why it has named the malware toolkit by this most important component.
Just as Duqu was based on the "Tilded" platform on which Stuxnet was developed, Gauss is based on the "Flame" platform. It shares some functionalities with Flame, such as the USB infection subroutines.
Mysterious Payload
The Gauss malware contains a mysterious payload which Kaspersky has yet to crack. It is unknown what the purpose of the payload is, but it is targetting very specific machines which have a specific configuration. The decryption key, Kaspersky believes, will be derived fromt hese specific system configurations, and so far it has been unable to find out what they are.
The experts at Kaspersky do believe it is crackable however and are looking for anyone with the relevant qualifications to help them out: "If you are world class cryptographer interested in this challenge, please drop us an e-mail at theflame@kaspersky.com."
One of the reasons the creators of the Gauss malware have gone to such lengths to encrypt this piece of the code, is to prevent it getting into the wrong hands and being used against the very people who created it in the first place.
© Copyright IBTimes 2024. All rights reserved.






