Inside a digital honey pot: How state hackers pose as hot women to steal secrets
On LinkedIn, 'Mia Ash' was a photographer. In reality, it was a honey-pot ruse from Iran.

Hackers with links to the Iranian government are using honey-pot operations to lure victims into downloading secret-stealing malware, a security firm revealed this week (27 July). Yes, it seems the oldest trick in the book is working better than ever in the digital age.
A group dubbed "Cobalt Gypsy" is reportedly using well-established fake online personas of attractive women to befriend targets, gain their trust and later dupe them into opening malicious software that could provide hackers with "full access" to private computer networks.
According to security firm SecureWorks, the hackers were caught posing under the name "Mia Ash" in order to direct phishing scams against entities in the Middle East and North Africa (MENA) region. They also had a strong focus on Saudi Arabia, experts said.
Analysis of the "Mia Ash" LinkedIn page, which was active online since at least April last year using stolen information and a hijacked profile image, showed that some of the targeted industries included technology, oil/gas, healthcare, aerospace and consulting.
On 13 January 2017, "Mia Ash", who claimed to be a London-based photographer, used LinkedIn to contact an employee at one targeted organisation, which remains unnamed. Over the next few days the pair exchanged messages and by 21 January the conversation had moved to Facebook.
As part of the long-winded phishing scheme, communications were later sent via email and WhatsApp – giving the hackers plenty of avenues to exploit. On 12 February, "Mia" sent a document titled "Copy of Photography Survey.xlsm" and urged the victim to open while it at work.
The so-called survey contained macros that, once enabled, downloaded a strain of malware known as "PupyRAT", which can infect Windows, Linux, OSX, and Android-based devices.
It remains unclear how many, if any, of the intended victims fell for the hackers' scam.
"Researchers conclude that Cobalt Gypsy created the persona to gain unauthorised access to targeted computer networks via social engineering," the SecureWorks team said in a blog post detailing its findings. "It is likely one of many personas managed by the threat actor.
"The use of the 'Mia Ash' persona demonstrates the creativity and persistence that threat actors employ to compromise targets. The persistent use of social media to identify and manipulate victims indicates that Cobalt Gypsy successfully achieves its objectives using this tactic."
The team linked the operation to the Iranian group by analysing the tools and techniques deployed in previous cyberespionage operations.
The analysis conducted by SecureWorks' experts provided an intriguing glimpse behind the curtain of an ongoing phishing campaign using honey-pot lures. The made up "Mia Ash", it emerged, was on every major social network including LinkedIn, Facebook, Blogger, and WhatsApp.
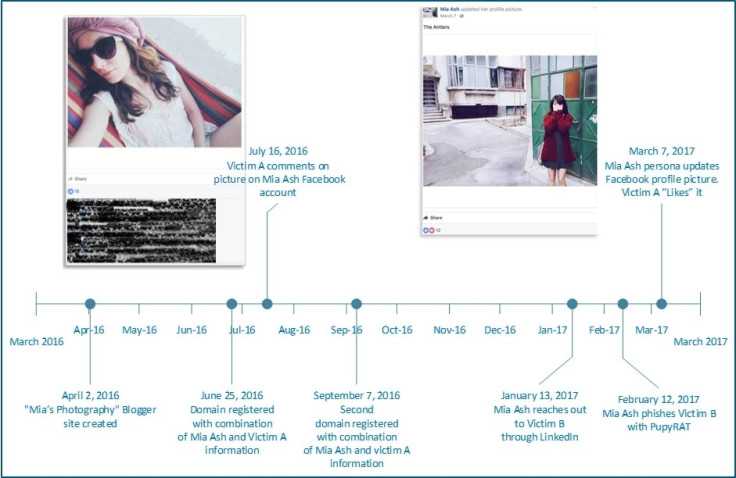
"Images of 'Mia Ash' were consistent across the various accounts and profiles," the experts noted. "They were likely taken from several social media accounts belonging to a Romanian photographer."
Other information, including an uploaded CV, was seemingly lifted from a US account.
Friends on LinkedIn and Facebook had significant overlap, with connections spanning Saudi Arabia, United States, Iraq, Iran, Israel, India, and Bangladesh. Most job titles, of course, indicated the majority of the people were chosen as juicy targets with access to sensitive corporate networks.
"The individuals' locations and industries align with previous Cobalt Gypsy targeting and Iranian ideological, political, and military intelligence objectives," SecureWorks concluded.
© Copyright IBTimes 2024. All rights reserved.









