Match.com security flaw puts 20 million user passwords at risk

Dating website Match.com is exposing the passwords of its millions of users by not securely protecting its login page.
Discovered in early March and still an issue at the time of publication, the website's home page does not use HTTPS security; instead, by using the older HTTP standard, the emails addresses and passwords of users logging into the site can be stolen by anyone on the same Wi-Fi network.
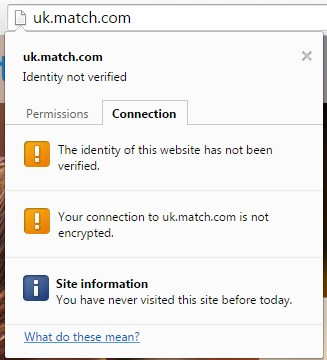
Discovered by a reader of Ars Technica, the flaw means Match.com's website is using an unprotected HTTP connection to transmit the login data, allowing anyone to perform a man-in-the-middle attack, most simply performed by logging into the same Wi-Fi network as the victim, such as in a cafe or train station.
Ars Technica states: "Had Match.com followed basic security practices and properly enabled HTTPS on the login page, the entire session would have been unintelligible to all but the end user and connecting server."
According to data published by Statistic Brain in March claims Match.com has over 21.5 million members worldwide.
As it stands, the technology website was able to view the email address and password of one of its reporters as they logged into Match.com. Given many people use the same passwords for several websites, social networks and even banking services, it wouldn't take much effort for a hacker to gain access to much more than their dating profile.
It isn't clear how long the flaw has existed. Scott Bryner, who discovered the problem, took a screenshot which suggests Match.com is experiencing a server configuration error that is redirecting all HTTPS traffic to an unsecure HTTP connection.
Match.com is part of the Match Group, which includes OKCupid and smartphone dating app Tinder, and is owned by US media company InterActiveCorp.
IBTimes UK has requested a comment from Match.com's UK press office about the security flaw.
© Copyright IBTimes 2025. All rights reserved.






















