Petya vaccination discovered: How to protect your computer network from ransomware attack
It's not a killswitch, but here are preventative steps you can take to secure your computers against Petya.

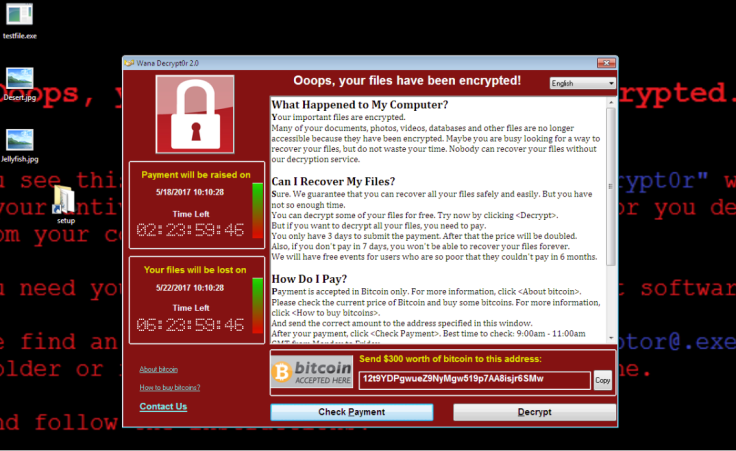
A huge cyberattack is currently affecting millions of computers in 64 countries, caused by the spread of a vicious ransomware called Petya.
It might be becoming confusing to keep track because everyone keeps calling it a different name: PetrWrap, NotPetya, GoldenEye – but basically it's an updated strain of Petya, which was already known to cybersecurity researchers last year, that seems to have spread from Ukranian accounting software that had been hacked.
The latest update means all previous decoders and prevention methods are now obsolete, but in the last 12 hours cybersecurity researchers have studied the malware and come up with ways you can prevent it from hitting your machines.
IBTimes UK has put together a step-by-step guide featuring advice from Microsoft and security firm Cybereason.
Step One: Install all Windows and anti-virus software patches
Make sure your computer is fully up-to-date with all security updates. Aside from anti-virus software updates, make sure you install the Microsoft security update MS17-010 on all Windows PCs and servers.
Step Two: Create a fake file to trick the ransomware
Overnight, Cybereason security researcher Amit Serper developed a vaccination that is able to stop Petya in its tracks and prevent it from initialising on your computers.
When Petya tries to run on a computer, it first searches for its own file name. If it finds it, then the malware is programmed not to run again (presumably because the hackers didn't want to demand ransom from the same victims twice).
To make your own fake file to trick the ransomware, open Windows Explorer, type "C:Windows" and press Enter.
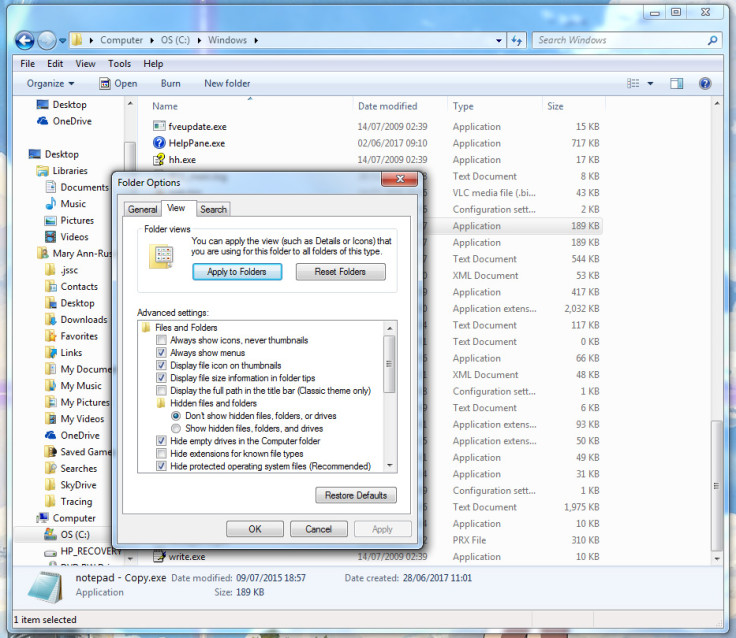
Go to Tools > Folder Options.
A box will pop up. Go to the View tab and make sure that the option "Hide extensions for known file types" is unchecked. Click "OK".
In the Windows folder, scroll down until you reach the notepad.exe application.
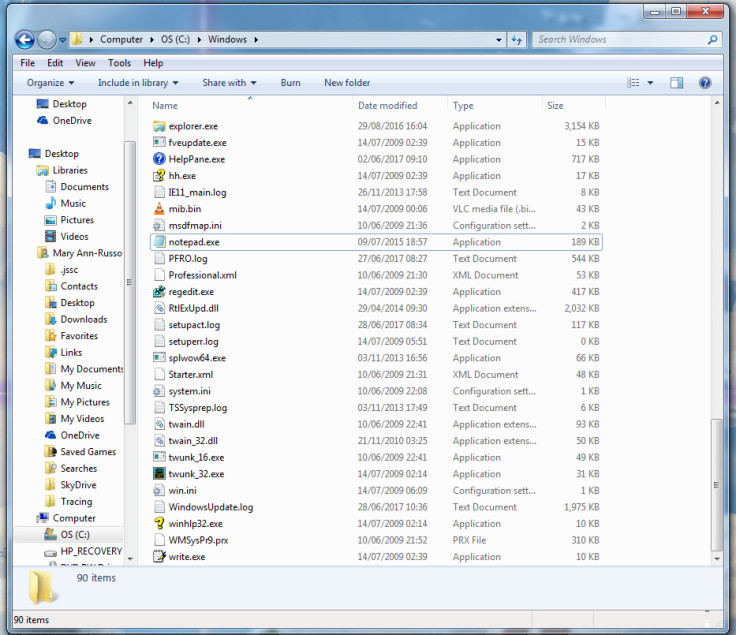
Right click it and select "Copy" from the menu. Then right click on an empty area of the window and select "Paste".
Your PC will ask you to grant permission to make this change. Click "Continue". Above notepad.exe, you should see another application appear, entitled "notepad – Copy.exe".
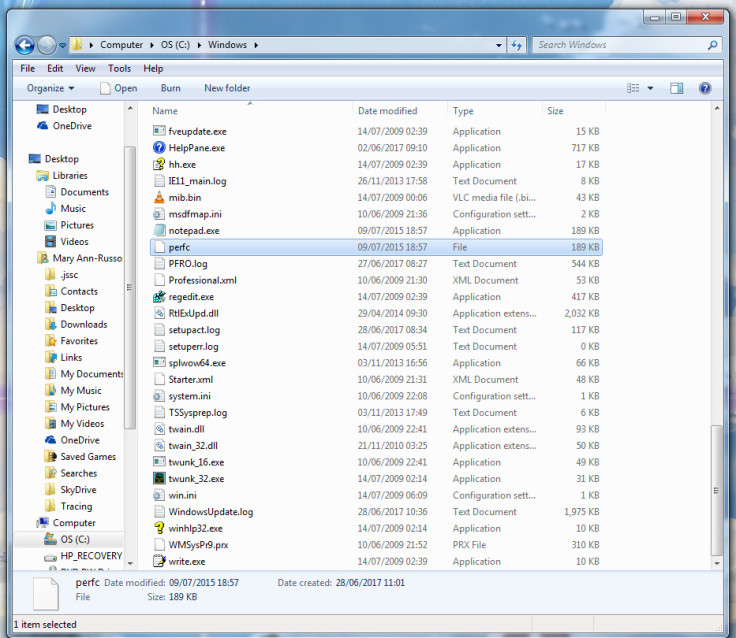
Right click it and select "Rename". Then delete the filename and type in "perfc". Don't put in any extension, just save the file as "perfc". Windows will ask if you're sure you want to change the file extension, click "Yes".
Step Three: Block the ransomware with hash rules
It's possible to block files based on their hash values, so that even if the file is renamed, it will not be able to execute if it somehow infects your computer. However, this requires some technical knowhow, and is best suited for someone with in-depth IT administrator skills.
Access the anti-virus software or security software that is securing your computer network and add the following hashes to the blacklist. If the prevention driver is installed, mark these hashes for prevention:
06eff17186695d8f9ea466d159b3316d
82ed636b43a9739457b7460bc79bbd13
f7e6475366a65ac81740b539e1c58c1f
ccd721b4794a82167f94c9e6c54a7e09
3501a946998bbb35fca74e686591be41
5308e42d3978f5db730138ccdd0bd6dd
41787c17eb6e11018c31433a34c5e2f7
f22943e464da1294d732cdf688b0df21
c1232a57e1c929dfba38aea58b227598
bffabed92d5c9a6a5844bde6eccce651
674e86e29d34facd7a69bc5ccf626bc3
415FE69BF32634CA98FA07633F4118E1
0487382A4DAF8EB9660F1C67E30F8B25
A1D5895F85751DFE67D19CCCB51B051A
If you are not using the Windows SysInternals' PSExec tool to administrate the computers on your network, you should also considering blocking the hash that was used to infect PSExec in the attack:
aeee996fd3484f28e5cd85fe26b6bdcd
Step Four: Block Petya's IP addresses at the network layer
IT administrators should also ensure that you block all known IP addresses and domains relating to Petya on all firewalls and any other network control systems you have in place for monitoring both inbound and outbound traffic:
95.141.115.108
84.200.16.242
111.90.139.247
185.165.29.78
Yadi[.]sk
Sundanders[.]online
Coffeinoffice[.]xyz
french-cooking[.]com
Step Five: If you still haven't, please disable the SMBv1 protocol
Also for IT administrators: You really should have blocked the terribly insecure Server Message Block version 1 (SMBv1) networking protocol by now, especially since the WannaCry cyberattack.
But if you haven't, please do so now, as it prevents the ransomware from moving around your network to infect more computers.
Here is a guide from Microsoft that explains exactly how to do this.
Step Six: Enable secure boot for all computers
If you have laptops as part of your computer network that were recently upgraded to Windows 10, then you need to enable Secure Boot.
Secure Boot is already enabled by default on all computers that were sold with Windows 8 or Windows 10, but if you have any older laptops that were recently upgraded, then here is a handy guide from HP about how to enable the feature.
Step Seven: Warn employees about unexpected restarts
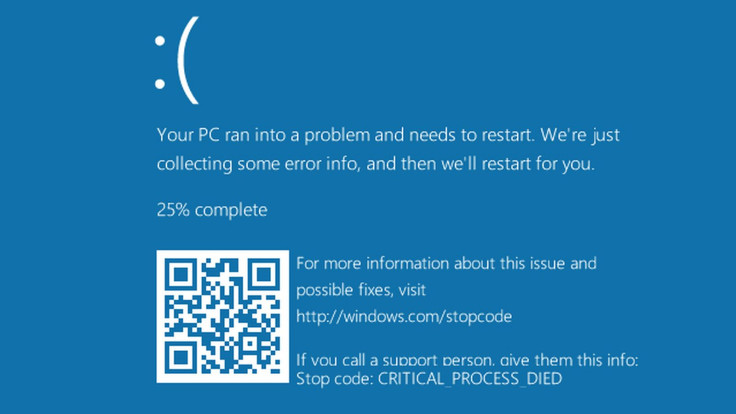
There is no reason for your computer to suddenly restart itself (unless your organisation forcefully pushes windows updates and schedules restarts to apply these updates), and in any case, it should not be preceeded by a blue screen of death.
If this happens, instruct all users to shut the computer down. Don't restart the computer, as this enables Petya to continuing encrypting all your data.
If you can manage to shut your computers down fast enough, IT Support teams can restore the original master boot record (MBR) using a Windows boot disk to prevent encryption of files.
It's also a good idea to install this MBR filter by Talos Intelligence.
© Copyright IBTimes 2024. All rights reserved.