Verizon hack: Security researcher apologises for not going public with database flaw

In the wake of a data breach that compromised 1.5 million Verizon customer credentials, a security researcher has revealed that he encountered a similar security incident in December, 2015. Security expert Chris Vickery, who has become well-known in security circles for exposing major database vulnerabilities, said he now regrets not drawing more attention to the flaw at the time.
"To the victims of Verizon's most recent data breach, I want to say that I'm sorry. I'm sorry that I didn't make a bigger fuss back in December and January when I found the other exposed MongoDB," he said in a blog post on MacKeeper posted on 31 March. "If I had sounded the alarm on that one, then maybe things would have been tightened down just a bit more and perhaps this latest breach [...] wouldn't have happened."
As we previously reported, hackers successfully breached Verizon Enterprise Solutions and compromised over one million customer credentials. After, the cache was uploaded for sale on the dark web for $100,000 (£71,000). First uncovered by security researcher Brian Krebs, the hack made a splash as it involved a firm more accustomed to helping Fortune 500 firms recover from attacks than suffering one itself.
The rogue database
Now, Vickery has detailed his previous dealings with Verizon and outlined how he responsibly disclosed the prior flaw on 22 December last year. In the initial email sent to Jim Matteo, Verizon's director of cybersecurity, Vickery said: "I've stumbled upon what appears to be one of your databases. It is currently configured for public access without any sort of password or authentication at all. In reviewing some of the data present, I have come across, for example, secret Verizon encryption and authentication keys (PSKs)."
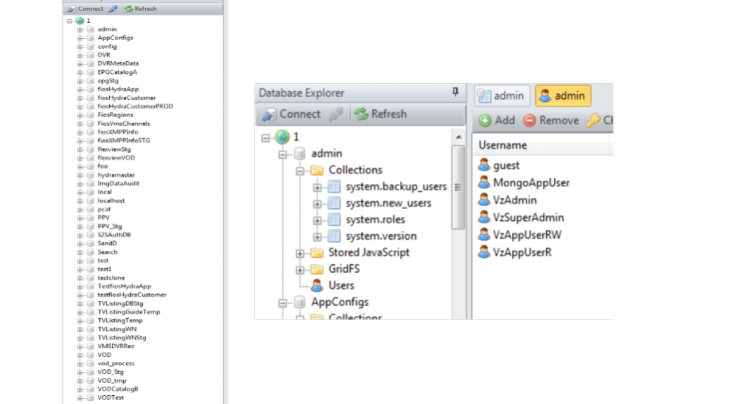
Vickery said a month passed before he heard back from the firm – on 19 January - saying they were finally on the case. However, it wasn't until 28 March that the researcher got a full explanation of the incident.
Upon further analysis, it was determined the previous flaw contained a mixture of 'test environment' content and legitimate customer data which had mistakenly been left online.
"I don't know for sure if the bad guys in the most recent breach actually used an exploit to get the data, but I can tell you that the Verizon MongoDB that I found was completely unprotected by any password or authentication. All you needed in order to access it was a MongoDB client and the IP address," said Vickery. Summing up his previous find, Vickery added: "In essence, it [was] a hybrid breach involving real data in an environment that no one was taking seriously. This is a potently dangerous practice that I'm finding more and more."
In his previous research, Vickery exposed a number of databases using the Shodan search engine. The firms he has grilled include child tracking website uKnowKids, Japan-based company Hello Kitty and software enterprise MacKeeper – which later went on to hire him for his efforts.
© Copyright IBTimes 2024. All rights reserved.