8 'Minecraft' apps infected with Sockbot malware on Google Play found adding devices to botnet
The apps were found ensnaring devices to a botnet to potentially carry out DDoS and other malicious attacks.

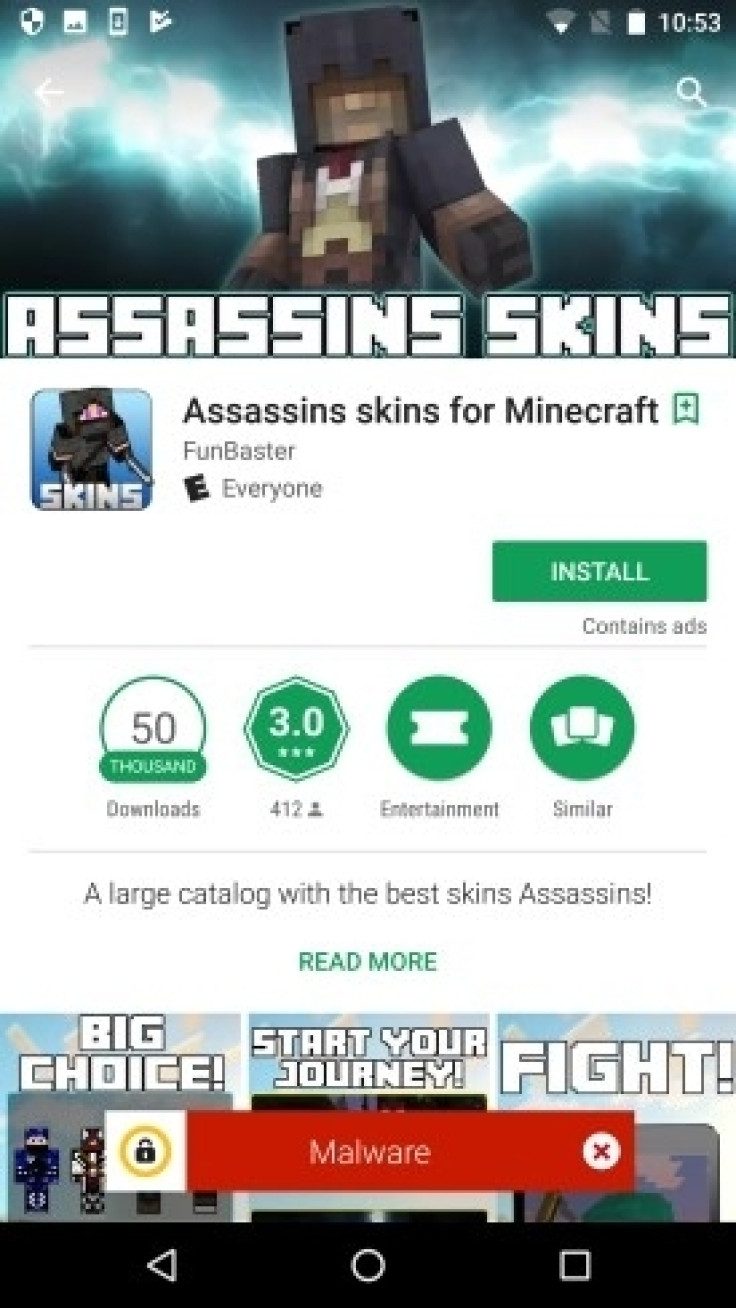
Security researchers have discovered that at least eight malware-laced apps on Google Play Store are ensnaring devices to a botnet to potentially carry out distributed denial-of-service (DDoS) and other malicious attacks. These apps claimed to provide skins to tweak the look of characters in the popular Minecraft: Pocket Edition game and have been downloaded as many as 2.6 million times.
Symantec researchers, however, discovered that these apps also carry a "new and highly prevalent type of Android malware" called Android.Sockbot that connects infected devices to developer-controlled servers.
One of the offending apps highlighted by researchers was called "Assassins Skins for Minecraft." Symantec did not name the other seven apps but noted that they were collectively downloaded between 600,000 and 2.6 million times before they were removed.
They were found to be targeting users primarily in the US, but also had a presence in Russia, Ukraine, Brazil and Germany, researchers said.
The app, once activated, connected to a command and control (C&C) server on port 9001 to receive commands. The server requests the app to open a socket using the SOCKS protocol to receive a list of ads and associated metadata. The SOCKS proxy mechanism then directs the infected device to an ad server to display advertisements.
However, researchers said there is no functionality within the app to actually display ads which could mean these servers are directing ensnared devices to eventually participate in DDoS attacks and other nefarious activities.
"This highly flexible proxy topology could easily be extended to take advantage of a number of network-based vulnerabilities, and could potentially span security boundaries," Symantec said in a blog post. "In addition to enabling arbitrary network attacks, the large footprint of this infection could also be leveraged to mount a distributed denial of service (DDoS) attack."
One developer account called FunBaster has been linked to these malicious apps and seems to have encrypted parts of the malicious code to "thwart base-level forms of detection." The developer has also signed each app with a different developer key to avoid "static analysis-based heuristics."
Symantec notified Google Play of the malicious apps on 6 October that have since been removed from the store by Google.