Air France cyberattack: Who is the Moujahidin Team and why are they waging cyber-jihad?

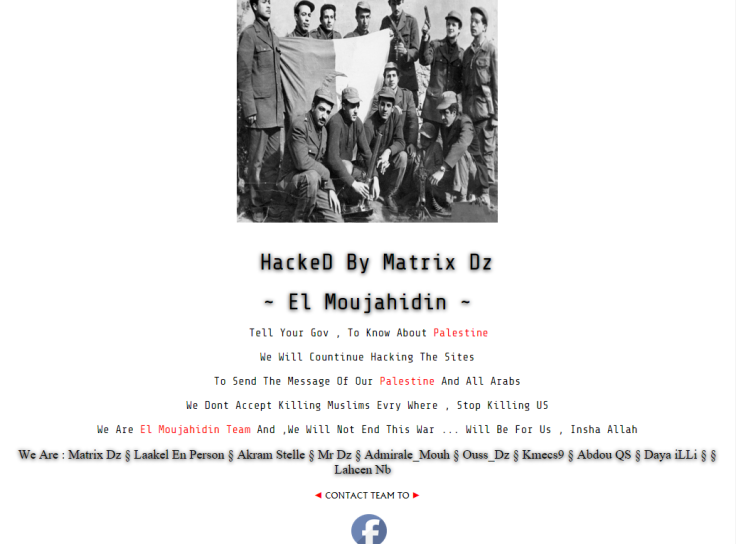
On 30 March 2015, a little-known hacking group calling itself the 'Moujahidin Team' (aka El Moujahidin) claimed credit for a cyberattack on Air France. The defacement on the website showed the group's logo and contained the message:
I promise you O my homeland that I will remain the faithful soldier that defends your border with the blood... and to protect the trust, to deliver the message, and to keep going on the method of 'Let Algeria live, freely independent, with blood and work of its sons, Allah permitting'
The group also provided two releases on Pastebin.com (a site commonly used by hackers to upload leaks or details of cyber-attacks) listing 117 French websites allegedly defaced by the group.
Recent Jihadist threats and attacks toward France made this attack by the Moujahidin Team - a name invoking other jihadist-oriented organisations - one of potential concern. However, the next day, the group targeted the Peoples National Bank of Mt. Pleasant in a defacement attack, thus raising even more questions about their ideology, agenda, and capabilities.
An analysis of the Moujahidin Team's short span of activity and statements show that while the group is a new one, its members have taken part in noteworthy operations and with other groups in the past. Furthermore, while the group claims jihadist motivations, it does not appear to demonstrate the same ideology or target focus as other jihadi hacking groups such as "CyberCaliphate."
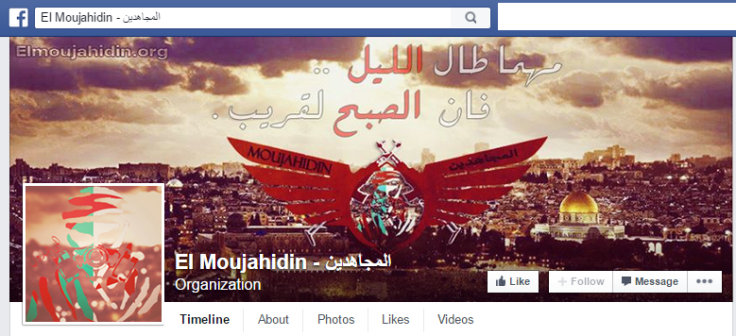
The Moujahidin Team is a newly established group mostly composed of Algerians. The hacking team created a Facebook page on 6 March 2015 and generated over 3,000 likes before being shut down between 31 March and 1 April.
The "About Us" section on the group's Facebook page explains:
(El Moujahidin) is an Algerian youth group. It appeared in 2015 on the Social Media Network Facebook, and the name of the group is back to the history of Algeria, at the days of the French colonialization and their struggle was politically and militarily to liberate Algeria.
A 30 March 2015 message from the group also claimed that they carry the "Mujahideen mentality" and that they do not "take [the] side of any party nor do we belong to any side as a group not as individuals."
The message was then followed up by claiming a troubling heightened profile following the "Anger of the Grandchildren" campaign, which they had attributed their attack on Air France to:
We will continue in penetrating [hacking] our targets despite stopping Ghadab al-Ahfad [Anger of the Grandchildren] Operation for security reasons. Members of the group are being tracked [followed] by the Interpol now... but our number is increasing and it will sharpen our thorn, and the demands of the People will be raised in the eyes of whoever participated in suppressing our voice!
The Hackers within the Moujahidin Team
The Moujahidin Team behaves and operates in a similar fashion as other groups and hackers. In addition to their Facebook page, the group's members also report their hacks via a defacement archive. Each hacking alias within the group has regularly attributed themselves to an attack - whether it be on social media or the defacement images themselves.
The group listed its members on the bottom part of its website:
Members of the Moujahidin Team are known to have experience with defacements going back to 2013. Among the most prominent of the group's members is "Red Hell Sofyan," the alias of a hacker (or potentially hackers) who acted as the admin of the "Algerian Cyber Army," also known as DZ Electronic Army. Many of the Moujahidin Team's attacks have been credited to Red Hell Sofyan, such as one from 28 March, in which the group claimed to have hacked a French electricity co-op.
Though Red Hell Sofyan currently only has only 69 defacements credited to the alias, it has also appeared on numerous hacking groups' defacements as a member of their organization. These hacking groups have included AnonGhost team, Moujahidin Team, and Algeria Cyber Army.
"Laakel En Person," another listed member of the Moujahidin Team, has recorded a total of 995 defacements on Zone-H, a popular defacement archive used by hackers, since November 2014. Laakel En Person appears to have been affiliated with Dz Mafia, an Algerian hacking group, as seen in a defacement claim attributed to the user.
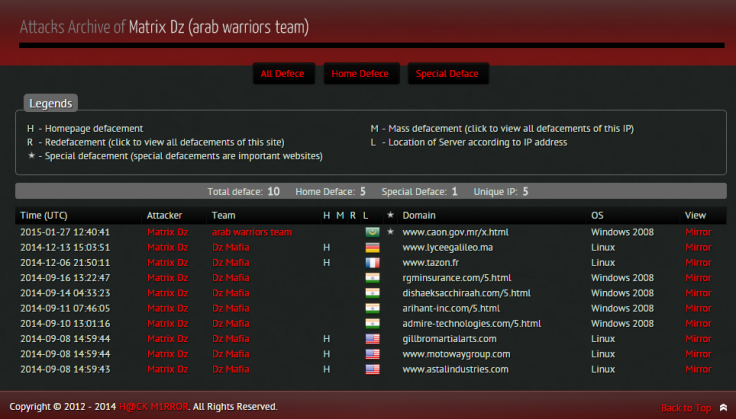
According to Zone-H records, Moujahidin Team member "Matrix DZ" has been defacing websites under this alias since 20 March 2014, and appears to have been formerly affiliated with Dz Mafia and the Arab Warriors team, a hacking group focused on issues relating to Islam and Palestine:
Other active hacking aliases within the group include "Fikou39," who holds connections to Virus Mafia Team, an Algerian hacking group that had previously threatened Morocco and Qatar.
Members of the Moujahidin Team have also collaborated long before the group's formation, with Fikou39 and Laakel En Person both attributed to a defacement attack on a Polish website.
Targets and Methods
The Moujahidin Team has attributed many attacks to the #OpFrance umbrella campaign, but it has not limited its targets to one country or type of website. A review of the group's attacks show a random selection of both private and government targets across the globe, including: the Russian domain of Fila sportswear; the Egyptian newspaper Alkhabar24.com; TheHubRadio in the UK; People's National Bank of Mt. Pleasant in the US; the General Elections Committee website for Jambi City, Indonesia; and recently, a string of attacks on Belgian domains.
While they have claimed many defacements, these hackers don't appear to have released sensitive data—at least on the individual level. Furthermore, the majority of the defacements conducted appear to have targeted low-hanging fruit: websites of smaller targets and subdomains of large corporations (as was the case with Air France).
In certain instances, the group has claimed to have "rooted" servers, which typically means that the group or hacker gained access to the root. However, while they claim to have rooted servers or sites, they have offered little to no proof that they were able to in fact gain root access.
Ideology
The Moujahidin Team's attacks and accompanying religious rhetoric come at a time when jihadist groups like the Islamic State begin welcoming attacks in cyberspace. These aspirations were seen this past January when the group "CyberCaliphate," which claimed to exist "under the auspices" of the Islamic State, claimed hacking social media accounts of the United States Central Command (CENTCOM).
The group's statements indicate a political/nationalistic focus along with a religious one. Written attacks against France by the group, while claiming grievance over the killing of Muslims, also touch on issues like France's colonial history in Algeria and treatment of Palestinians.
The group's activity is often accompanied by phrases like "Smoke Weed Everyday" and rap music, activities considered impermissible by the hardline Islamist standards of pro-Islamic State hacking groups. To that point, the group has even claimed to have performed cyber-attacks with no claimed ideological motivation at all, doing so "Just For Fun."
Furthermore, the group has never claimed any support for the Islamic State, al-Qaeda, or any other jihadi group in or outside of Algeria. The Moujahidin Team's name should not be used as any kind of false connector to recently formed hacking groups claiming to support the Islamic State or other jihadist groups.
It appears that most of the Moujahidin's Team's attacks are limited to defacements - an easy and relatively non-damaging type of attack to execute. However, its members' connections with other prominent hacking aliases and groups may provide the Moujahidin team the potential for more sophisticated and dangerous attacks in the future.
The article was provided by VARA Cyber Security, which monitors threats coming from the hacking community and monitors primary sources. For more info visit www.varacyber.com
© Copyright IBTimes 2025. All rights reserved.



















