CryptoWall Ransomware: Millions Exposed to Cybercrime Threat via Yahoo, Match.com, AOL and Other Websites
CryptoWall Ransomware campaign earns criminals $25,000 per day

A sophisticated cyber-crime campaign is leaving millions of people vulnerable to having malware installed on their computers simply by visiting high profile websites such as Yahoo, Match.com, and AOL.
The campaign is using the fast-growing method of 'malvertising' to spread a pernicious form of malware called ransomware - in this case CryptoWall 2.0 - which encrypts all the files on the hard drive of a victim's computer, and if the victim doesn't pay a ransom by deadline, those files are lost forever.
Research by security company Proofpoint indicates that up to 3 million people would have been exposed to the malvertisments since the campaign was first detected on 18 September, 2014.
The researchers were even able to estimate how much money the criminals were earning on a daily basis as the ransoms are charged in bitcoin, meaning all payments are traceable via the public blockchain (although not linked to a culprit).
According to the data collected by Proofpoint, the criminals are earning up to $25,000 (£15,500) every day from the scheme, and are using a complex bitcoin laundering method to hide their ill-gotten gains.
Failure to pay the ransom before the deadline expires - which is a dynamically generated amount of bitcoin equating to $500 - results in victims' hard drives being permanently encrypted, thus rendering them effectively useless, with all information inaccessible.
At this time, Proofpoint does not have any information about who placed the Malvertising with the ad networks - and the nature of malware and bitcoin is such that there's no conclusive data at this time about who's behind the campaign.
Ad networks
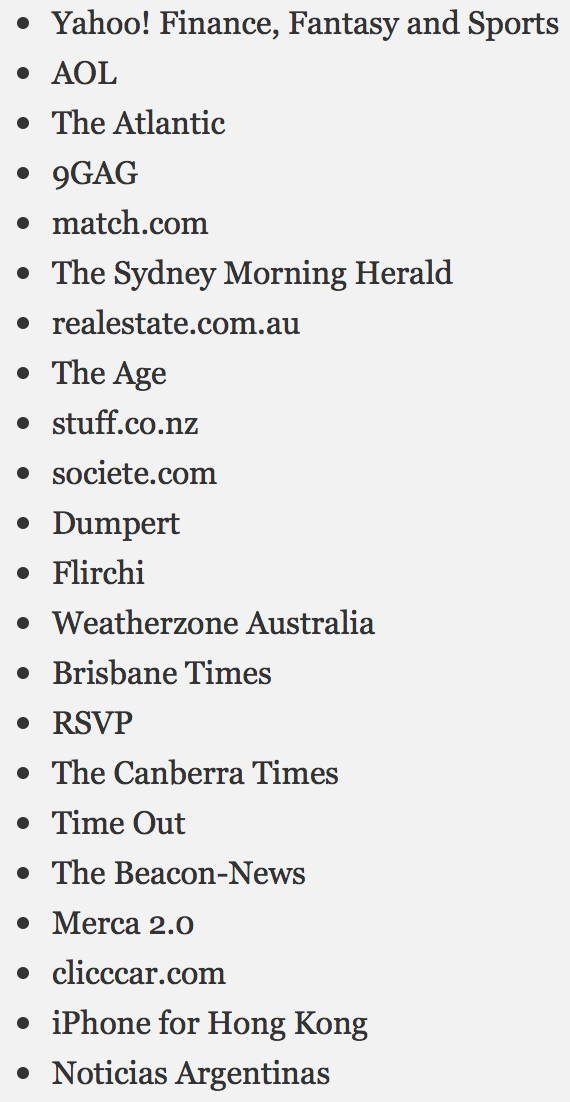
Proofpoint has identified a large number of websites serving the malware (listed on the right) but points out that the websites themselves have not been compromised, as the malicious ads are served through advertising networks.
The researchers discovered that the malware was being spread through three high-profile ad networks - Rubicon Project, OpenX, and Right Media/Yahoo Advertising.
Again, it was not that these companies' networks were compromised, but they simply failed to carry out adequate checks as to whether or not the ads being served on their networks were malicious.
Proofpoint says it "believes the issue to be resolved" at this stage as the last detection of issues related to this campaign was 18 October.
Pernicious
However, while this campaign may be finished, the malicious adverts are likely to be re-used and could be active once again as part of a new campaign targeting different websites/ad networks.
The campaign used stolen images and advertising copy from brands such as Fancy, Bing, and Case Logic which looked identical to real ads which might appear on the website.
The pernicious nature of this type of cyber-attack means there is no obvious indicator that a site has been compromised, yet a victim's computer can be infected just by visiting the website, and without having to click on a link.
According to Proofpoint: "Malvertising attacks are particularly hard to detect because most advertising on trusted sites comes from a variety of ad networks – different visitors will see different ads from different places, not all of which will be malicious."
The use of ransomware in the form of CryptoWall 2.0 is another indication of a growing trend among cyber-attacks. The rapid proliferation and success of another piece of ransomware - Cryptolocker - beginning in late 2013 has raised awareness of this threat in both enterprise IT security and among the general public.
© Copyright IBTimes 2025. All rights reserved.






















