Hackers hijack millions of Android devices to secretly mine Monero in drive-by cryptomining scheme
At least two malicious domains linked to this campaign saw over 30 million visits per month.



Hackers have managed to hijack millions of Android devices over the past few months to secretly generate Monero coins in a new "drive-by" cryptomining campaign, security researchers have discovered. According to Malwarebytes researchers, the campaign first spotted in January seems to have begun in November 2017.
In this malicious campaign, the threat actors redirect unsuspecting mobile users to dubious pages set up to perform in-browser cryptomining by exploiting their device's processing power to generate Monero coins.
Visitors are presented with a CAPTCHA to solve to prove that they are human and not a bot.
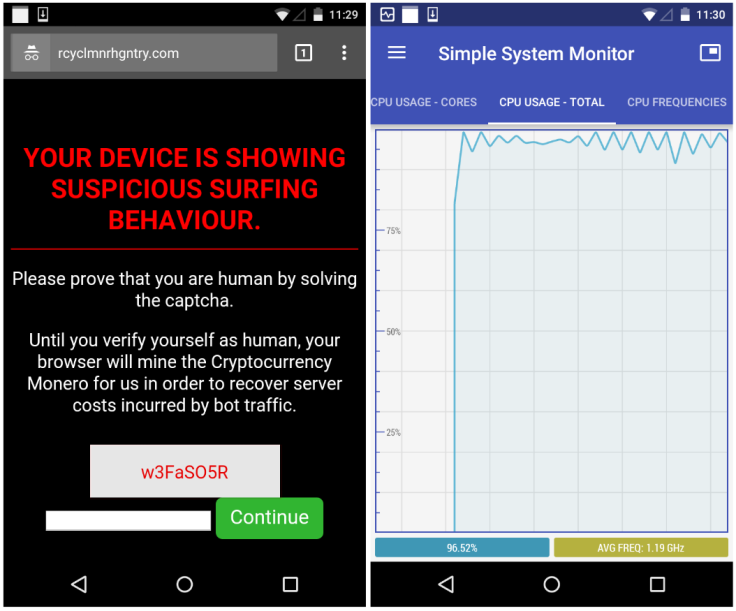
"Your device is showing suspicious surfing behaviour. Please prove that you are human by solving the captcha. Until you verify yourself as human, your browser will mine the Cryptocurrency Monero for us in order to recover the server costs incurred by bot traffic," the warning message reads.
Until users solve the CAPTCHA code, the site runs an exhaustive cryptojacking script that exploits the phone's CPU power to mine Monero - a process that could damage the device if left running long enough.
"Until the code (w3FaSO5R) is entered and you press the Continue button, your phone or tablet will be mining Monero at full speed, maxing out the device's processor," Jerome Segura, lead malware intelligence analyst at Malwarebytes, wrote in a blog post.
Once they enter the code, users are simply redirected to the Google home page.
Researchers said victims may encounter this forced redirection during regular browsing sessions or via infected apps with malicious ads.
"It's possible that this particular campaign is going after low quality traffic—but not necessarily bots —and rather than serving typical ads that might be wasted, they chose to make a profit using a browser-based Monero miner," they noted.
Five identical domains have been identified using the same CAPTCHA code but with different Coinhive site keys. At least two of them had over 30 million visits per month while the traffic combined from all five domains amounted to about 800,000 visits per day with an average four minutes spent on the mining page.
"We believe there are several more domains than just the few that we caught, but even this small subset is enough to give us an idea of the scope behind this campaign," Segura said. "It is difficult to determine how much Monero currency this operation is currently yielding without knowing how many other domains (and therefore total traffic) are out there. Because of the low hash rate and the limited time spent mining, we estimate this scheme is probably only netting a few thousand dollars each month.
"However, as cryptocurrencies continue to gain value, this amount could easily be multiplied a few times over."
Over the past few months, security experts have observed a steady rise in cryptojacking attacks, malware-based miners and browser-based cryptominers to ensnare the processing power of millions of devices to generate digital currencies without the knowledge or consent of users.
"Forced cryptomining is now also affecting mobile phones and tablets en masse—not only via Trojanized apps, but also via redirects and pop-unders," Segura noted. "While these platforms are less powerful than their Desktop counterparts, there is also a greater number of them out there.
Over the weekend, more than 4,000 websites in the US, UK, Australia and other nations were hijacked with hackers tweaking the code of a plugin named BrowseAloud to secretly mine cryptocurrency.
Some of the compromised websites included thousands of government ones including those of the Information's Commissioner's Office, the United States Courts, the Queensland Government's legislation, Student Loans Company, NHS services and more.
"Similar to what we see with IoT devices, it's not always the individual specifications, but rather the power of the collective group altogether that matters," Segura said.





