Malicious Bankbot malware found hiding in flashlight and Solitaire apps to steal your bank details
This isn't the first time the notorious banking Trojan has made its way into Google Play Store.

Security researchers have discovered that the notorious BankBot banking malware has once again snuck into Google Play store by hiding in seemingly trustworthy apps such as flashlight and Solitaire apps. According to a new report by cybersecurity firms Avast, ESET and SfyLabs, thousands of Android users have been infected by new versions of the malicious Trojan over the past few months.
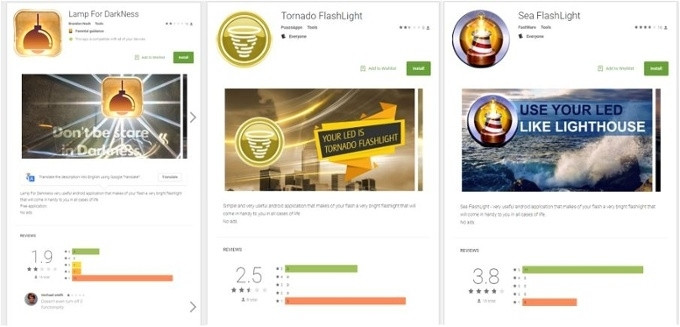
Researchers said the latest version of BankBot, first spotted in Google Play on 13 October, has been concealed in various flashlight and Solitaire apps. Some of the infected apps include "Tornado FlashLight", "Lamp For DarkNess" and "Sea FlashLight."
In late October and November, the malware was found embedded in a smartphone cleaning app and a number of Solitaire gaming apps.
Once the infected app is downloaded, the malware activates and checks what others apps are installed against a hard coded, pre-computed SHA1 list of 160 mobile apps.
"The package names are hashed, and therefore we've only been able to identify 132 of them," researchers said. "This list includes apps from Wells Fargo and Chase in the US, Credit Agricole in France, Santander in Spain, Commerzbank in Germany and many others from around the world."
According to the list of targeted apps, the malware has set its sights on DiBa, Barclays, CitiBank, SunCorp, Raiffeisen Bank, ICICI and Bank Austria among others.
"If the malware is able to identify one or more apps from the SHA1 list installed on the phone, it initiates a 'service' - an expression used for an Android application component that can perform long-running operations in the background," researchers said. "The service includes a dropper functionality that allows it to download another application from a web server in order to install it on the device."
The malware then communicates with its C&C server via Google's Firebase service and attempts to trick a user into giving the app administrative privileges by pretending to be a Play Store or system update using similar icons and package names.
After a two-hour wait to evade Google's checks, the Trojan drops its malicious payload. Once installed, the new APK also requests device admin rights as well.
The malware then waits for an unsuspecting user to open up one of the banking apps to create an overlay on top of the genuine app within milliseconds. Once the customer enters their bank details, they are swiftly sent to the threat actors.
Since many banks rely on two-factor authentication to ensure safe and secure transactions, the BankBot malware also has the ability to steal text messages. This allows hackers to grab the mobile transaction number (mTAN) sent to a customer's phone and use it to conduct illegal online transfers and send money over to their own accounts.
Moreover, researchers said the infected apps also dropped other malware such as Mazar and Red Alert.
The malware has already struck banking customers in the US, Australia, Germany, France, Poland, Spain, the Netherlands, Portugal, Turkey, Greece, Russia, Dominican Republic, Philippines and Singapore.
However, researchers noted that the malware is not active in the Ukraine, Belarus and Russia likely to "protect the cyber criminals from receiving unwanted attention from law enforcement authorities in these countries".
The apps, which managed to slip past Google's Play Protect security feature, have since been removed from Google Play. At least one of the infected Solitaire gaming apps was seen featuring a "Verified by Play Protect" badge as well.





















