North Korean worldwide hacking rampage steals millions from casinos and banks
Subset of Pyongyang hacking team linked to largest known case of financial cybercrime.

In February 2016, the Bangladesh Central Bank was thrown into turmoil after hackers infiltrated its computer systems and fled with millions of dollars. Now, over a year later, evidence is mounting the attack is closely linked to the reclusive nation of North Korea.
At the time, the hack was described as the largest known case of financial cybercrime. The criminals attempted to steal what amounted to over $900m (£723m, €845m) by sending fraudulent requests via Swift, a global financial transaction and messaging service based in Brussels.
The scheme paid off, but was somewhat foiled after the New York Federal Reserve (NY Fed) spotted a typo in one of five large transfer requests.
Still, the hackers were able to compromise $81m in funds, later laundered through various locations including casinos in the Philippines. Until now, the culprits' identities remained a mystery.
Loose attribution has existed since last year that a North Korea-linked hacking group – often codenamed "Lazarus" – was involved, but this week (3 April) evidence emerged claiming that the group's activities are more widespread than previously suspected.
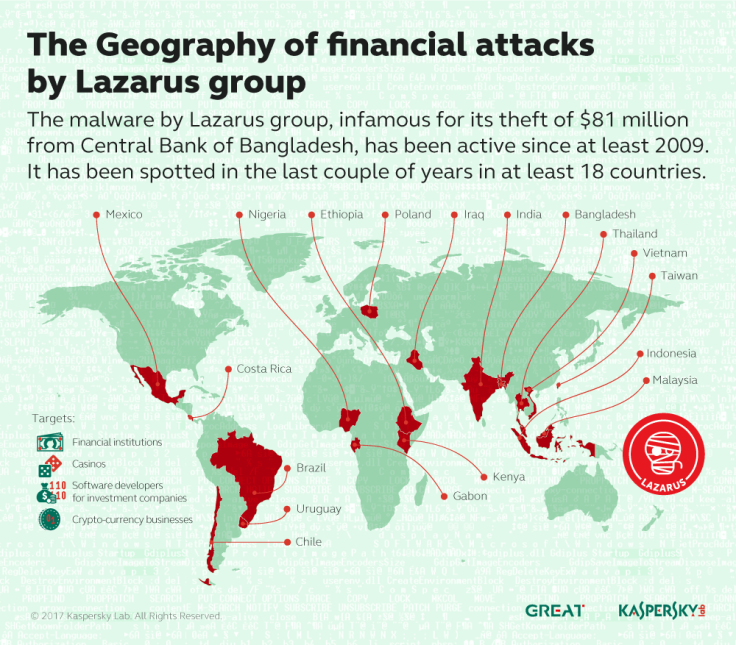
According to Kaspersky Lab, a Moscow-based cybersecurity firm, a subset of Lazarus – codenamed "Bluenoroff" – is solely dedicated to financial cybercrime and has targeted banks, casinos and crypto-currency firms in well over a dozen countries around the world.
"Lazarus is not just another APT actor," Kaspersky Lab's global research and analysis team said in a blog post, referencing the abbreviation for Advanced Persistent Threat – a term used to describe well-resourced hacking groups, often linked to governments or intelligence agencies.
It continued: "The scale of the Lazarus operations is shocking. This level of sophistication is something that is not generally found in the cybercriminal world. It's something that requires strict organisation and control at all stages of operation. That's why we think that Lazarus is not just another APT actor."
Kaspersky said in its report the hacking group has been found in countries including Russia, Norway, Mexico, Uruguay, Australia, India, Poland, Peru and Nigeria. It uses a technique known as a "watering hole" – using malware to infect websites used by its targets.
'Key part of the equation'
In total the group has been spotted in 18 countries so far, and Kaspersky said some as yet unreported hacks in Europe and south-east Asia were as recent as this year. The security firm released analysis of one command and control (C&C) server that revealed a "very unusual" IP address – originating in North Korea.
The compromised server was found due to it not being properly cleaned after an off-the-shelf cryptocurrency mining software became unresponsive and froze, Kaspersky said. In any case, researchers explained that seeing the IP address has made North Korea a "key part" of the equation.
It remains unknown if the reclusive government based in Pyongyang directly sanctioned the cyber-operations. Often, such attacks are carried out from China.
However, Lazarus, and by extension the long-standing Kim family dynasty, was previously implicated in the massive cyberattack on Sony Pictures back in 2014.
The traits of that attack – cyber-sabotage and hard drive disk wiping – echo the latest financial crimes. According to various cybersecurity firms, the group has been active for years (roughly since 2009) – however Kaspersky researchers believe the move to bank rampages are relatively new.
One hypothesis put forward is the hacking group was forced to turn to this form of attack to fund its operations. The true scope of the scheme remains unclear, but it's undoubtedly large. Samples show it has a "factory of malware" which sources hacking tools from multiple sources.
The researchers wrote: "Lazarus attacks are not a local problem and clearly the group's operations span across the whole world. It seems that they have a different set of people working on the problems of invisible money theft or the generation of illegal profit.
"We believe they started [the latest] campaign at the end of 2016 after their other operation was interrupted in south-east Asia. [It] regrouped and rushed into new countries, selecting mostly poorer and less developed locations [...] because they are, apparently, easy prey."
'Invisible theft'
Lazarus/Bluenoroff reportedly spends significant time "tearing apart" legitimate software and patches to find ways to steal the big money. Despite this, the malware used is not designed for hit-and-run operations, Kaspersky said.
"Their solutions are aimed at invisible theft without leaving a trace," researchers explained.
"Of course, attempts to move around millions of USD can hardly remain unnoticed, but we believe that their malware might be secretly deployed now in many other places and it isn't triggering any serious alarms because it's much quieter.
"The Bluenoroff group has been one of the most successful in launching large-scale operations against the financial industry. We believe that they will remain one of the biggest threats to the banking sector, finance and trading companies, as well as casinos for the next few years."
Evidence mounting
It seems we have not heard the last from Lazarus. Indeed, in February this year, Symantec, a cybersecurity firm, found one suspected link between the hackers and attacks on a Polish financial institution. It said more than 100 organisations in 31 different countries were targeted.
Analysis at the time revealed previously unidentified malware called "Ratankba" which shared "commonalities" with the suspected North Korean hacking team. It included "aggressive and destructive tactics" alongside strikingly familiar disk-wiping capabilities.
Separately, BAE Systems has said at least seven banks in the UK alone have been targeted by Lazarus' malware. It added 15 were hit in the US, 19 in Poland and nine in Mexico. Before the Kaspersky research however, it stressed true links were ultimately "unclear".
Only 12 months prior, February 2016, a global partnership of law enforcement and security giants revealed Operation Blockbuster – which detailed a form of Lazarus-linked malware dubbed "Destover" that partially led the FBI to conclude North Korea was closely linked to the group.
"The Lazarus group has developed an extensive and varied toolset which effectively combines a number of methods for delivering additional malicious tools, exfiltrating data, and launching destructive attacks," the report stated at the time.
© Copyright IBTimes 2025. All rights reserved.






















