Suspected Russian hackers Fancy Bears targeting Mac OSX with 'Komplex' Trojan
The hacking group goes by many names including Sofacy and Pawn Storm.

A notorious cyberespionage group with suspected links to Russian intelligence has developed a complex piece of malware designed to infect computer systems running Apple OSX, according to cybersecurity researchers at Palo Alto Networks.
The hackers, dubbed Sofacy Group by the California-based experts, have been given many titles over the years by analysts including Fancy Bears, APT28 and Pawn Storm. It is the same group believed to have infiltrated the Democratic National Committee (DNC) earlier this year.
In an in-depth blog post, Palo Alto explained how the Trojan – called 'Komplex' – does not exploit an Apple security flaw but instead takes hold via extremely targeted spearphishing tactics.
In this instance, the malware was used to infect victims in the aerospace industry.
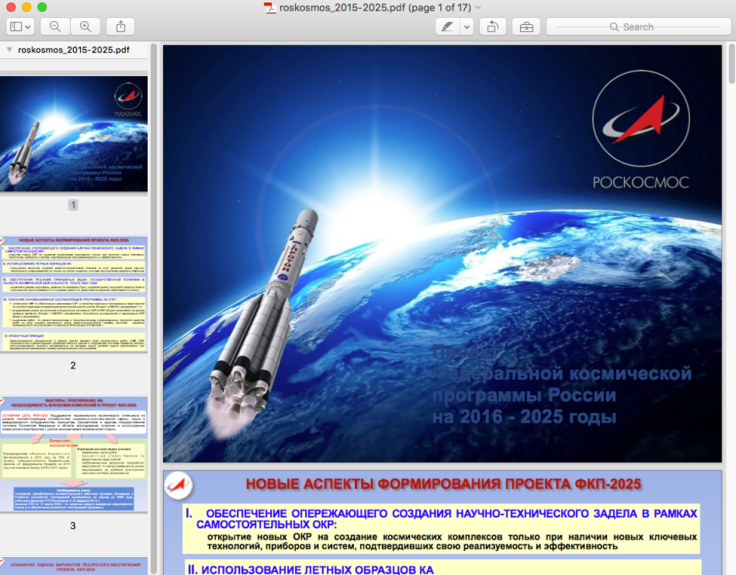
The payload is purposefully designed to hide in a 17-page Russian-language PDF document that describes the Russian Federal Space Program's projects between 2016 and 2025. According to the researchers, it appears legitimate on first inspection and will even open on the Mac's 'preview' mode.
Once the intended victim opens the link to the PDF, the file is capable of downloading additional files to the infected machine, executing and deleting files and interacting with the system shell – which is a user interface used to access the operating system directly.
While reverse engineering the Komplex payload, the researchers said they noticed a number of coding overlaps including similarities with an OSX Trojan revealed by BAE systems last year that relied upon an alleged security vulnerability in MacKeeper software.
Referencing the highly-targeted nature of the attack. Ryan Olson, intelligence director at Palo Alto's Unit42 cybersecurity team, told Information Week: "The person who received this file was expecting to get this file." He added that the hackers typically use Windows tools and that this is the first major strain the firm has analysed that targets OSX.
However, at least one other major security team has uncovered evidence that the state-sponsored group – which has targeted everyone from the German parliament to the World Anti-Doping Agency (Wada) – has infiltrated Apple devices in the past.
Crowdstrike, which probed the initial DNC cyberattack back in July, previously said that Sofacy has developed a slew of exploits since its inception in the mid-2000s including specific malware for Linux, OSX, IOS, Android and Windows phones.
"[Fancy Bears] has been responsible for targeted intrusion campaigns against the aerospace, defence, energy, government and media sectors," said Dmitri Alperovitch, CTO of CrowdStrike, in a recent blog post.
"Its victims have been identified in the United States, Western Europe, Brazil, Canada, China, Georgia, Iran, Japan, Malaysia and South Korea."
In a blog post, the Palo Alto team said the development of the Trojan showcases a "continued evolution" toward multi-platform attacks.
"The Sofacy group, also known as APT28, Pawn Storm, Fancy Bears, and Sednit, continues to add to the variety of tools they use in attacks," the researchers noted. "In this case, targeting individuals in the aerospace industry running the OS X operating system."
© Copyright IBTimes 2025. All rights reserved.






















