Watch out for this convincing Gmail phishing scam that's rifling through users' emails
Dodgy attachments look like something you have been previously sent by a contact.

Gmail users are being warned of a fresh phishing scam that tricks victims into giving up their Google credentials, before scouring their sent messages folder for new victims to pass the malicious email on to.
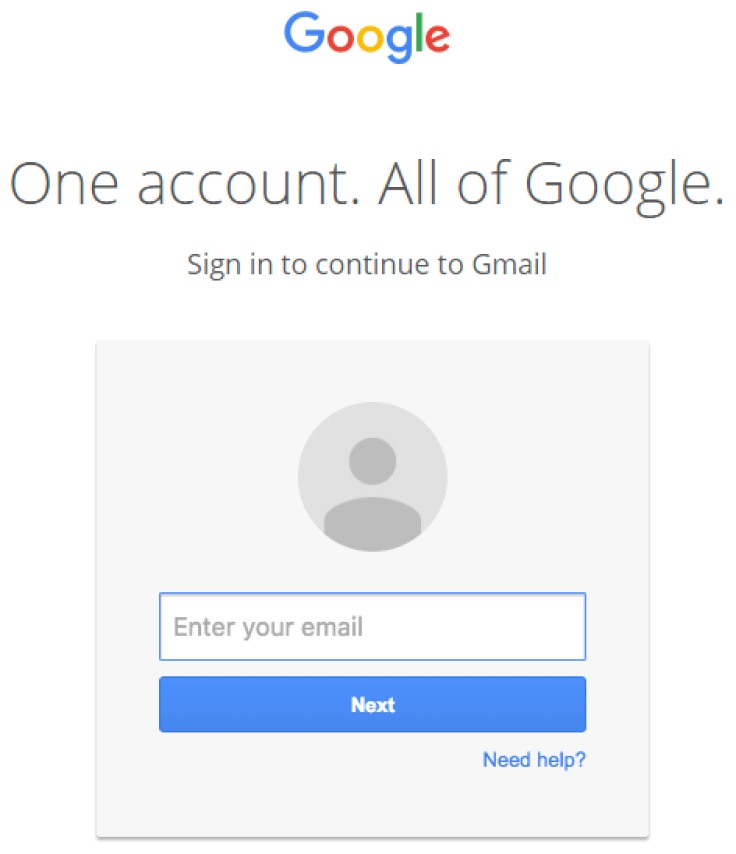
The attack uses image attachments that masquerade as a PDF file. Once clicked on, users are directed to phishing pages disguised as the Google sign-in page.
The user's Gmail account becomes compromised once they enter their information. After doing so, the attacker rifles through the victim's sent messages folder so that they can browse correspondence they have sent to their contacts, and pass on the scam using familiar subject lines and attachments.
This makes the phishing emails look ever more convincing to recipients and allows the scam to propagate quickly. What is more, the phishing pages do not appear to set off Google's HTTPS security warnings, which are designed to alert users when they land on an unsafe web page.
The phishing technique uses a data uniform resource identifier (URI) to embed a complete file into the browser location bar. Clicking on this creates a functional but fake Gmail login page that steals the user's information and sends it to the attackers.
The newly-detected scam was uncovered by Mark Maunder, CEO of WordPress security service Wordfence. According to Maunder, the scam has managed to convince even "experienced technical users", and is targeting other services in addition to Gmail.
"Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot," Maunder said.
"Now that they control your email address, they could also compromise a wide variety of other services that you use by using the password reset mechanism including other email accounts, any SaaS services you use and much more."
One victim told Hacker News that their school was targeted before the holiday break and that the attack was able to spread to several students and teachers over a two-hour period, adding it was "the most sophisticated attack" they had ever seen.
"They went into one student's account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team," the victim explained.
"We had to take our whole mail system down for a few hours while we cleaned it up."
How to spot a phishing email
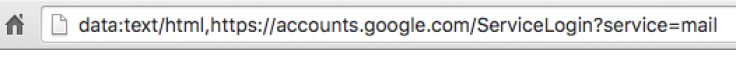
Users can avoid being targeted by enabling two-factor authentication and by looking out for the prefix 'data:text/html' in the browser location bar, which indicates that they are being directed to an illegitimate web page.
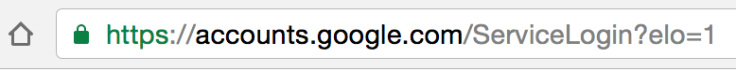
"Make sure there is nothing before the host name 'accounts.google.com' other than 'https://' and the lock symbol," warned Maunder. "You should also take special note of the green colour and lock symbol that appears on the left. If you can't verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page."
Google is now investigating the matter. "We're aware of this issue and continue to strengthen our defences against it," a spokesperson said.
"We help protect users from phishing attacks in a variety of ways, including: machine learning based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more. Users can also activate two-step verification for additional account protection."
© Copyright IBTimes 2024. All rights reserved.






