Android malware 'Catelites Bot' can pretend to be 2,200 banks - and will drain your account
Joint research by Avast and SfyLabs exposes malware with cyber-gang links.

A new strain of Android malware has the ability to pose as more than 2,200 banks – including Santander and Barclays – in order to steal passwords and plunder accounts.
Dubbed "Catelites Bot", the software has been tentatively linked to the criminal operations of a recently-dismantled Russian gang who used the "CronBot" Trojan to infect more than 1 million users and pilfer $900,000, according to joint research by Avast and SfyLabs.
In a blog post Wednesday (20 December), experts revealed that CronBot and Catelites Bot malware samples shared some key similarities – and warned that the hackers may only be getting started.
"Catelites Bot has developed a sophisticated way to target more than 2,200 banks worldwide with fake mobile banking app interfaces," said Avast mobile threat researcher Nikolaos Chrysaidos.
"The malware has the ability to automatically and interactively pull Android banking applications' logos and names from the Google Play Store," he continued.
"While the manipulative mobile banking screens don't resemble the original banking apps, the power lies within the malware's shotgun approach: Targeting millions of users of thousands of banks to increase the likelihood a few victims will fall for the trick."
Catelites Bot is spread via third-party app stores, researchers revealed. In recent months there has been "one or two fake apps per week" attacking Android devices. First, the malware seeks administrator permissions. If granted, it unleashes a slew of "sophisticated" tactics.
Chrysaidos told IBTimes UK: "So far, the Catelites malware is focusing on users in Russia. We believe it's in an early testing stage with the threat actors responsible looking to increase its spread worldwide, targeting banks across the globe. Our analysis of the command and control (C&C) server shows that around 9,000 users have been infected to date."
As noted, it is able to stealthily adopt logos and mobile app names of banks, and use generic login templates in an attempt to hijack usernames, passwords and credit card information.
These won't fool tech-savvy users, but others may still fall victim to the phishing pages:
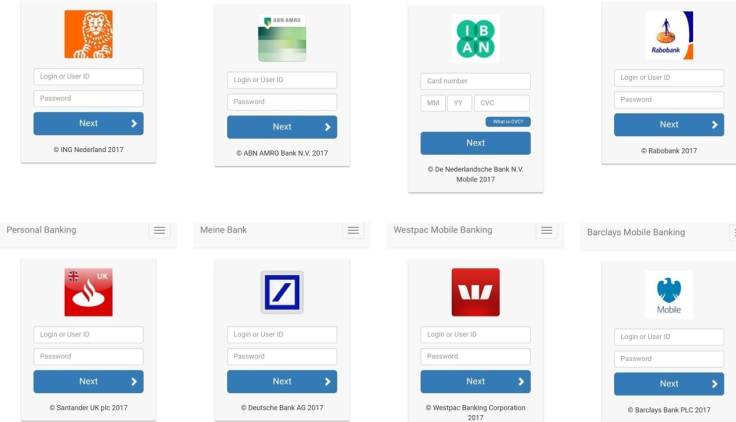
Catelites Bot uses the "overlay screens" to dupe users, and if details are entered they will be sent to the hackers. Avast and SfyLabs found it has a number of functions that are not yet active.
These include the ability to intercept texts (frequently needed to access two-factor authentication codes), wipe device data, lock the smartphone, access phone numbers, peek into message conversations, force password unlocks and even change the speaker volume.
"While we don't have any evidence that the Catelites Bot actor is linked to CronBot, it is likely that Catelites members have gotten their hands on the Cron malware and repurposed it for their own campaign," Avast's Chrysaidos added in the blog post.
"The malware spreads via unofficial sources, so for users it's important to set their phone to only accept app downloads from official app stores, like Google Play, and to double-check if their banking app is clean by looking their app's interface to see if it has drastically changed."
Overlay screen attacks have, in the past, been branded "cloak and dagger" incidents. Other Trojans – including 'BankBot' and 'FalseGuide' have been known to mirror legitimate apps.






