Don't fall for this 'missing font' scam spreading malware to Chrome and Firefox browsers
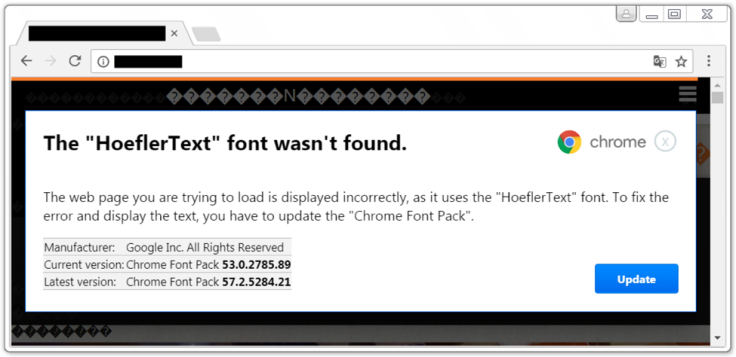
The warning reads 'HoeflerText font wasn't found'. Experts say never click it.
Hackers are now using a sneaky pop-up technique posing as a font update to spread "Locky" ransomware and a remote access tool (RAT) to users on Google Chrome and Mozilla Firefox which, if clicked, can give cybercriminals complete access over infected computers.
Palo Alto Networks security expert Brad Duncan analysed the hackers' campaign – widely known as "EITest" - which has been using pop-ups since at least December 2016. He has now published his findings in a company blog post and as an update on the SANS Internet Storm Centre.
Two separate attacks were recently spotted in the wild, each using social engineering tactics to send a victim to a compromised website which then displayed a pop-up warning: "The HoeflerText font wasn't found".
An update button – if used by the targeted victim – would instantly download a malicious package.
In one of the August 2017 campaigns, sent via botnet-based spam, Duncan revealed that the pop-up "returned a malicious JavaScript file" disguised as a font library.
It was specially crafted to download and install the Locky strain of ransomware, Duncan said.
The second attack, which took place during the same timeframe, was altered to send out a type of malware under the name "Font_Chrome.exe".
This, it transpired upon analysis, was not a form of ransomware but instead a variant of file downloader which was programmed to spread the "NetSupport Manager RAT".
Locky is a notorious strain of ransomware which typically spreads via spam emails, locks down computer files and demands digital currency for their return. It emerged in February 2016, making an immediate impact by infecting a major hospital in Los Angeles, California.
That campaign alone netted hackers $17,000. The NetSupport RAT in question, meanwhile, is commercially-available software previously linked to hacks on gaming service Steam last year.
According to Duncan, the find signified "a potential shift in the motives of this adversary". The identities of those behind the latest campaigns, however, remains a mystery.
He wrote: "It's yet to be determined why EITest HoeflerText popups changed from pushing ransomware to pushing a RAT. Ransomware is still a serious threat, and it remains the largest category of malware we see on a daily basis from mass-distribution campaigns."
Indeed, in 2017 experts documented multiple ransomware outbreaks. Two major campaigns, using malware called "WannaCry" and "NotPetya" spread to hundreds of thousands of computers across the world. In both cases, experts have suggested the involvement of nation states.
"Users should be aware of this ongoing threat," Duncan said of the EITest campaigns.
"Infected users will probably not notice any change in their day-to-day computer use. If the NetSupport Manager is found on your Windows host, it is probably related to a malware infection."
In March 2017, a security researcher called Mahmoud Al-Qudsi spotted the same HoeflerText pop-ups on a compromised website hosted on WordPress.
© Copyright IBTimes 2025. All rights reserved.






















