Duterte's official website, over 100 other sites compromised by Vietnam-linked hackers OceanLotus
The hacking group has been dubbed "one of the more sophisticated APT actors currently in operation".

A hacking group allegedly linked to the Vietnamese government have managed to hijack more than 100 websites in several Asian countries including the official website of Philippine president Rodrigo Duterte, security researchers have found.
Researchers at cybersecurity firm Volexity said the sophisticated hacking group called OceanLotus or APT32, have managed to compromise websites of organisations and individuals tied to government, military, human rights, civil society, state oil exploration and media to launch future attacks.
Some of the websites compromised in this attack campaign include the official website of the Association of Southeast Asian Nations (Asean) and a number of other sites linked to it, multiple government ministries in Cambodia and Laos, China's BDStar, China National United Oil Corporation and other Chinese oil and navigation entities as well as the official website of the Armed Forces of the Philippines.
"Volexity believes the size and scale of this attack campaign have only previously been rivaled by a Russian APT group commonly referred to as Turla," researchers wrote in a report published on Monday (6 November). "The OceanLotus threat group has successfully operated, largely unnoticed, through several high-profile websites since late 2016."
Hackers targeted websites of strategic importance, particularly those whose visitors were likely to be targets of interest, and inserted malicious JavaScript into the site along with one or more webshell backdoors "to maintain persistence".
The malicious JavaScript was used to make calls over HTTP or HTTPS to domains controlled by the attacks to load one of two different OceanLotus frameworks. These JavaScript frameworks were designed to track, profile and target the compromised websites' visitors.
Visitors who were particularly of interest were flagged for specific targeting and received special JavaScript created to compromise the user's system or email accounts.
Users who were specifically targeted received a popup once every 24 hours when accessing one of the compromised websites. Once clicked, the popup would redirect the user to Google to initiate OAuth access to one of OceanLotus' Google Apps, giving the hackers permission to access to all email and contacts.
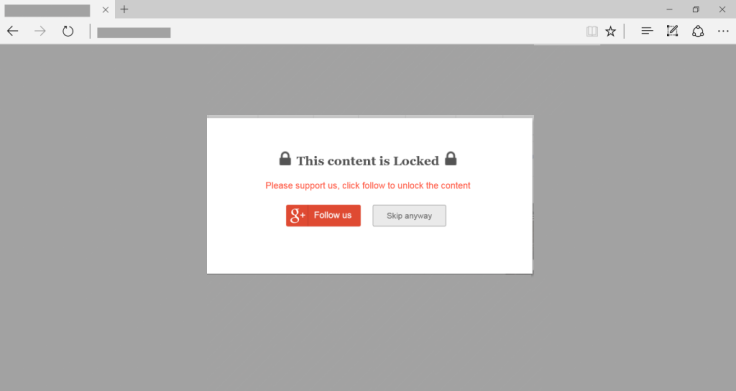
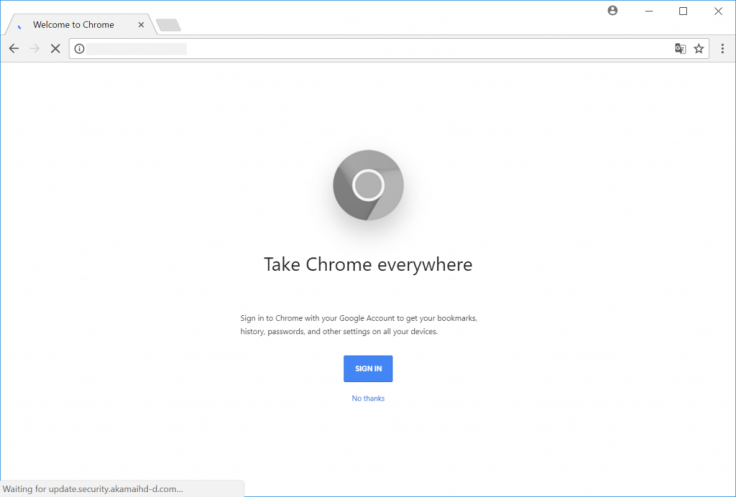
Some compromised websites were also hit with spearphishing campaigns in an effort to install backdoors on the targeted systems. The group has also been known to distribute malware through fake Chrome, Firefox and Internet Explorer updates.
Researchers said a "staggeringly large number of websites" have already been strategically compromised by OceanLotus, the majority of which belongs to Vietnamese individuals and organisations that have been critical of the Vietnamese government such as human rights and opposition groups.
The rest belonged to state-owned or affiliated organisations linked to one of three countries that share a land border with Vietnam or the Philippines, they noted.
OceanLotus managed to compromise these websites using direct working credentials to the site's content management system (CMS) or by exploiting outdated plugins or CMS components, researchers noted. However, it is still unclear how they managed to acquire the working credentials to the sites.
"In the case of exploitation, the CMS software used by the victim organisations was often woefully out of date. Both the core components and added plugins had remotely exploitable vulnerabilities that lead to compromise," researchers noted.
Volexity said the hacking group had significantly and rapidly advanced its capabilities in recent years and is currently "one of the more sophisticated APT actors currently in operation".
"While Volexity does not typically engage in attempting attribution of any threat actor, Volexity does agree with previously reported assessments that OceanLotus is likely operating out of Vietnam," researchers said.
"This is largely due to the extreme and wide-scale nature of certain targeting that would be extremely unlikely to align with the interests of those outside of Vietnam.
"As a result, Volexity believes that OceanLotus has been rapidly developing a highly skilled and organised computer network exploitation (CNE) capability."





















