GandCrab ransomware: Hackers distribute new malicious malware via RIG and GrandSoft exploit kits
The note demands victims pay up 1.5 Dash (currently $1038, £733) as a ransom.

Security researchers have uncovered a new nasty strain of ransomware called GandCrab that is being distributed through two separate exploit kits. First spotted on 26 January, Malwarebytes researchers said hackers are using the exploit kits, RIG EK and GrandSoft EK, to spread the ransomware - an unusual tactic in itself.
Exploit kits are deployed by hackers to take advantage of security flaws and holes in systems to deliver malware, RATs, coining miners and other malicious payloads. Ransomware, however, is usually deployed via dubious emails.
The only other ransomware distributed through an exploit kit was Magniber, they noted.
"It is interesting to see a new ransomware being distributed via exploit kits in what so far seems to be a few ongoing campaigns," the researchers wrote in a blog post published 30 January. "The other interesting aspect is that two distinct exploit kits are delivering it, although it is unclear if the same actor is behind both campaigns and experimenting with different distribution channels."
According to Malwarebytes, the infamous Seamless malvertising campaign is being used to push the RIG EK distributing the GandCrab ransomware. The older GrandSoft exploit kit, which was believed to have disappeared, has also been found redistributing the ransomware.
Once the payload is dropped and run on the system, GandCrab collects a trove of information from the infected PC including username, keyboard type, computer name, processor type, IP address, OS version, disk space, active drives, location, current Windows version, processor architecture, presence of any antivirus software and system language.
It also specifically checks whether the keyboard layout is Russian, likely to avoid encrypting these machines and evade detection. Meanwhile, the harvested information is sent to a command-and-control server.
GandCrab Ransomware - Welcome! WE ARE REGRET, BUT ALL YOUR FILES WAS ENCRYPTED! - .GDCB ... ðŸ§ðŸ§ðŸ§ pic.twitter.com/YkYNAAmvgG
— David Montenegro (@CryptoInsane) January 26, 2018
GandCrab then behaves similarly to other ransomware, encrypts files using an RSA algorithm and demands payment in exchange for the "GandCrab Decryptor" to unlock the files.
"Welcome! We are regret, but all your files was encrypted," the ransom note reads. "But don't worry, you can return all your files. We can help you!"
The note demands victims pay up 1.5 Dash (currently $1038, £733) as a ransom which will later bump up to 3 Dash if it isn't paid within a few days.
It also offers victims free decryption for one file, information about how to buy Dash and pay the ransom, a support chat and the current exchange rate for Dash.
"Attention! Don't try use third-party decryptor tools!" it warns. "Because this will destroy your files."
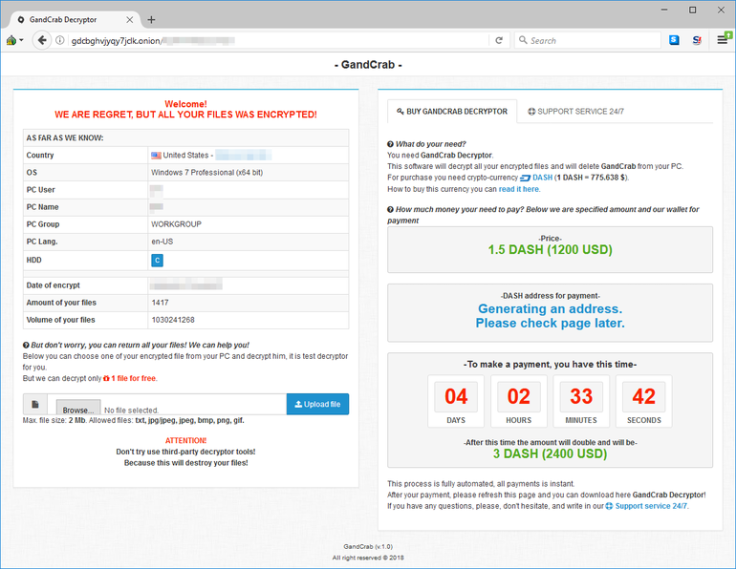
"Interestingly, GandCrab is not demanding payment in the popular Bitcoin currency, but rather a lesser-known cryptocurrency called Dash," MalwareBytes said. "This is another sign that threat actors are going for currencies that offer more anonymity and may have lower transaction fees than BTC."
The GandCrab server is hosted on a .bit domain, which is not recognised by the Internet Corporation for Assigned Names and Numbers (ICANN).
As of now, there is no way for victims to decrypt GandCrab ransomware files for free which means users should make sure they have the latest software updates and patches installed to avoid having any lingering vulnerabilities exploited by the exploit kits.





