How Ryanair was hacked to see $5m stolen from its bank accounts

Ryanair has confirmed its bank account was hacked and €4.6m (£3.4m) was stolen but just how could this have happened?
While the low-cost airline has confirmed the theft of the money, it has not provided any details on how the attack took place or if it knows who is behind the theft.
Ryanair's statement simply says it has investigated "a fraudulent electronic transfer via a Chinese bank last week" and has asked the Criminal Assets Bureau in Dublin to investigate the attack.
It added: "The airline has been working with its banks and the relevant authorities and understands that the funds – less than $5m – have now been frozen. The airline expects these funds to be repaid shortly, and has taken steps to ensure that this type of transfer cannot recur."
According to the The Irish Times, the fraudulent transfer was initially not flagged as the company uses its bank accounts to purchase large amount of fuel and the money could have been siphoned off during one of these transactions.
Dyre Wolf at the door?
While we do not have any confirmation of who may be behind the attack, one cyber security expert has suggested one possible perpetrator could be the gang behind the Dyre Wolf campaign.
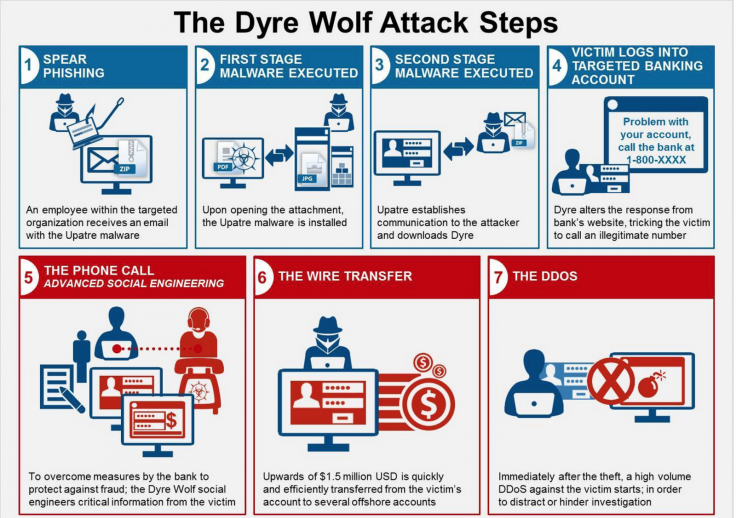
Earlier in April, IBM Security revealed details of a cybercrime campaign that leveraged the relatively simple malware together with sophisticated social engineering to steal millions of dollars from large enterprises.
The campaign works by first infecting the machines of the victim with malware which is typically spread through targeted spear phishing emails.
According to IBM Security, the people behind the Dyre Wolf campaign are targeting organisations that frequently conduct wire transfers with large sums of money.
Once the victim has clicked on the phishing email and the Dyre malware has been installed, the next phase of the campaign kicks in.
Once the infected victim tries to log in to one of the hundreds of bank websites for which Dyre is programmed to monitor, a new screen will appear instead of the corporate banking site. The page will explain the site is experiencing issues and that the victim should call the number provided to get help logging in. - IBM Security
The number - which the criminals reuse in different attacks - is of course operated by the hackers but appears to the victims to be a real support line. Using social engineering techniques, the hackers are then able to steal the credentials they need to ultimately siphon off large sums of money from the companies's bank accounts.
British security blogger Graham Cluley has posited the possibility that this was how the money was stolen from Ryanair but, as he points out, because Ryanair has not shared any more details, we simply cannot know if this is the case
He said: "I think it's a shame that Ryanair hasn't been able shed more light on the details of how the hack might have occurred, or what steps it might have taken to prevent it from happening again. After all, that would no doubt be information which could prove useful to other organisations which wish to protect themselves from similar criminal activity."
© Copyright IBTimes 2025. All rights reserved.






















