Qatar National Bank: Database leak gives data on al-Jazeera journalists and British 'spies'
A 1.4GB trove of internal documents, files and sensitive financial data purporting to be from the Qatar National Bank (QNB) has been leaked online.
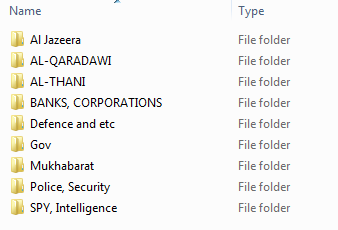
The massive data dump appears to contain hundreds of thousands of records including customer transaction logs, personal identification numbers and credit card data. Additionally, dozens of separate folders consist of information on everything from Al Jazeera journalists to what appears to be the Al-Thani Qatar Royal Family.
However, it is a folder listed as "SPY, Intelligence" that quickly catches the eye. Upon analysis, it contains a slew of records listed as Ministry of Defence, MI6 (the UK foreign intelligence service) and Qatar's State Security Bureau, also known as "Mukhabarat".
The MI6 file, which sits alongside similar documents reportedly holding information on Polish and French intelligence, opens up an in-depth report on an alleged agent. This includes names of close relations, phone numbers, social media accounts and credit card data. Furthermore, in one instance, a file marked "wife", opens a photo showing a woman and two children.
There are roughly a dozen of these intelligence dossiers included in the Qatar data dump. However, this data is not likely to have been collated by the bank and remains unverified by IBTimes UK.
The alleged banking leak also openly lists a folder marked "Al Jazeera" that stores nearly 30 separate profiles alongside a Microsoft Excel file that holds more than 1,200 records – including national ID numbers, telephone numbers and home addresses. Much like the intelligence files, the Al Jazeera disclosure contains a number of entries labelled "SPY" and also includes images of the person alongside social accounts, banking data and passwords.
When contacted, multiple sources confirmed to IBTimes UK the data is legitimate.
On the customer-facing side, the data dump contains a number of folders that are likely to concern users. Some of the listed database spreadsheets are labelled: "Account Master", "User Profile" and "Transactions" however, much like the rest of the contents, IBTimes UK is still in the process of verifying the entire leak. It remains unknown how current the data is – and how or when it made its way into the public domain.
The massive leak was initially uploaded at Global-Files.net however was quickly removed without explanation. Then, a separate well-known whistle-blowing website mirrored the entire data dump in an easily-accessible format.
In response to questions from IBTimes UK, Maha Mubarak, QNB media relations officer said: "It is QNB Group policy not to comment on reports circulated via social media. QNB would like to take this opportunity to assure all concerned that there is no financial impact on our clients or the bank. QNB Group places the highest priority on data security and deploying the strongest measures possible to ensure the integrity of our customers' information. QNB is further investigating this matter in coordination with all concerned parties."
The same statement has since been posted online.
After analysing the data Simon Edwards, cybersecurity expert with Trend Micro, said: "The breach seems to be a classic attack on a bank, with the majority of data leaked online exposing customers' bank account details, such as account numbers, credit cards and addresses.
"There's also a lot of information on banking transactions, suggesting that the perpetrators were trying to expose specific transactions. This theory can be further strengthened by the hacker's attempts to profile the bank's customers into different categories, mostly focusing on Qatar's TV network along with other foreign agencies, some of which are categorised as 'spies'."
He added: "Interestingly, there is also additional data about mainly foreign bank account holders, which includes information such as their Facebook and LinkedIn profiles, along with 'friends' associated through those social networks. This data doesn't appear to have come directly from the bank itself, rather the perpetrator used the data held by the bank to then build up profiles of further targets."
IBTimes is currently attempting to verify the contents of the leak and is in the process of contacting a number of the people named in the disclosures.
© Copyright IBTimes 2025. All rights reserved.






















