Windows 10 free upgrade scam warning: Cybercriminals spread ransomware with fake Microsoft email

As we have seen numerous times in the past, cybercriminals are quick off the mark when it comes to taking advantage of trending news events. Whether it's the birth of a royal baby, an airline crash, or the untimely death of a well-known actor, hackers are quick to try and trick people into clicking malicious links or downloading infected files.
It comes as little surprise that criminals are looking to lure victims into installing ransomware on their PCs under the guise of being a Windows 10 upgrade. Microsoft launched its Windows 10 update on 29 July and it is rolling the update out in waves to users around the world, meaning that some people will still be waiting to install the new software. An email telling them the upgrade is available will certainly be of interest.
Cisco's security research group Talos has identified the latest spam campaign which takes advantage of the interest in Microsoft's software and sees hackers impersonating the company to exploit its user base. Microsoft is offering free updates to Windows 10 to all Windows 7 and Windows 8 users and is rolling out the update to customers through the Windows Update system, which will automatically inform users when the real update is available.
Windows 10 Free Update scam
The cybercrime campaign is being spread using an email claiming to be from Microsoft with the subject line: "Windows 10 Free Update". The 'from' field features the email address update@microsoft.com which appears to be a valid and official address, but as Talos points out, "a quick look at the email header reveals that the message actually originated from IP address space allocated to Thailand".
The message is designed and formatted to replicate real emails coming from Microsoft, even down to using the same colour scheme as the software giant. However the hackers have failed to format the text correctly and certain characters are not parsed properly, as you can see in the image below:
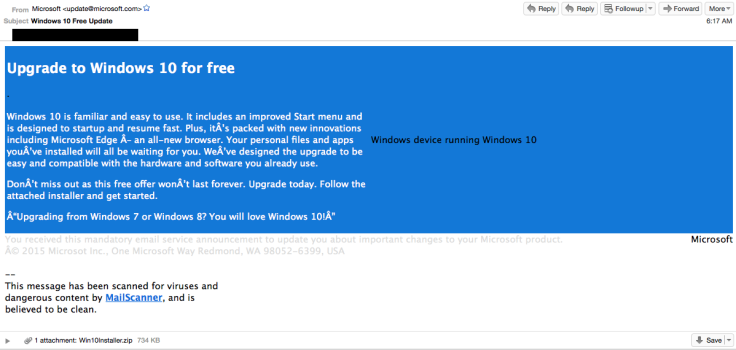
Talos researchers said the reasons for this could be "due to the targeted audience, a demographic using a non-standard character set, or the character set the adversaries were using to craft the email".
The attackers even go so far as to include a disclaimer message which looks like one you might expect in an email from Microsoft, and they have even added a section to say the email attachment has been scanned by an antivirus and is legitimate. However, if the victim does click on the attachment, downloads the zip file, extracts and runs it, the are greeted with the following message:
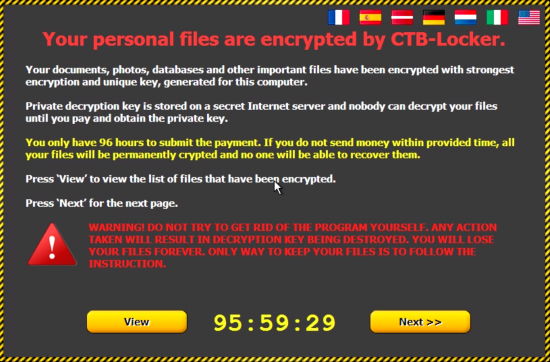
The particular ransomware variant in this case is CTB-locker and like all ransomeware it encrypts the files on your computer and demands a ransom be paid in a given period of time or risk losing the files forever. In this case the window for payment is just 96 hours which is much shorter than most ransomeware demands.
The criminals behind the campaign are asking for payment in Bitcoin and utilising the Tor network in order to remain anonymous. Talos says that it is seeing a high rate of infection for ransomware with a large number of variants being seen delivered either by spam campaigns or via exploit kits such as Angler, which currently has an 83% market share according to Sophos Labs.
© Copyright IBTimes 2025. All rights reserved.






















