MoneyTaker hackers exposed: Russia-linked group rob $10m from global banks
Previously undetected hackers targeted Swift, the world's finance network.
A Russian-speaking hacking group – aptly dubbed "MoneyTaker" – has covertly stolen up to $10m (£7,485,052, €8,472,327) from global banking targets in under two years, new research suggests.
According to Moscow-based firm Group-IB, the previously unknown group used clever tactics – including "fileless malware" - to remain under the radar from authorities, hitting more than 20 institutions in the past 18 months. Victims were based in the US, UK and Russia.
The report, released Monday (11 December), claimed the hackers had stolen key documentation about Swift, the global financial transfer system. It warned that banks in Latin America may be targeted next.
The average financial loss from each successful attack was roughly $500,000, the analysis paper confirmed.
"MoneyTaker uses publicly available tools, which makes the attribution and investigation process a non-trivial exercise," commented Dmitry Volkov, co-founder and head of intelligence at Group-IB.
"In addition, incidents occur in different regions worldwide and at least one of the US banks targeted had documents successfully exfiltrated from their networks, twice," Volkov added. Group-IB, which described the attackers as "Russian-speaking", expects a new wave of thefts "in the near future".
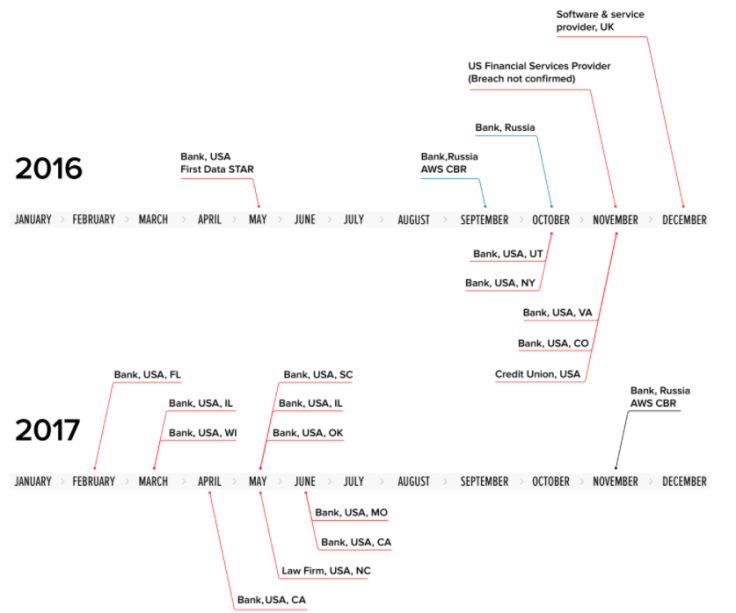
The first recorded incident was in May 2016, with hackers accessing a US bank's network via a portal operated by First Data, a payments processing company. Later, it hit targets based in California, Utah, Oklahoma, Colorado, Illinois, Missouri, North Carolina and more.
This year alone, Group-IB said the MoneyTaker cell – named after one of its own cybercrime tools – had compromised eight US banks, one law firm and one Russian bank. Last December, an unnamed "software and service provider" located in the UK was the latest victim, it added.
Until now, thanks to tactics which circumvented antivirus software, the group had gone unnoticed.
One unique feature of the hackers' modus operandi was the use of a "persistence server" which would only deliver malware to victims with IP addresses in MoneyTaker's whitelist, researchers said.
When it did attack, it used fileless malware which could essentially self-destruct. The Group-IB team found one hack was launched after probing a bank staffer's home computer network.
MoneyTaker relied on sneaky malware which could take screenshots of machines and snoop on keystrokes.
Group-IB said it would exfiltrate bank documents and lurk inside a network to spy, even after stealing cash.
Hijacked material would later be sent to popular Russian services, including Mail.ru and Yandex.
In February 2016, the Swift network was compromised by hackers, exploited to help steal roughly $81 million from the Bangladesh Central bank - arguably one of the largest digital heists ever recorded.
The culprits of that hack remain unknown, but some experts found links to North Korea.
In its report Group-IB said it had found "no evidence" to suggest that MoneyTaker was involved in the Bangladesh cyber-assault. Instead, it had pilfered Swift documentation. Volkov, speaking to Bloomberg indicated the latest findings were just the tip of the iceberg.
Group-IB provided its analysis to police agencies Europol and Interpol for further investigation.
Explained: How the hackers' operation worked
The Group-IB report described the cybercrime gang's scheme as "extremely simple", using money mules hired in foreign countries to help steal the cash. The analysts wrote in a blog post:
"After taking control over the bank's network, the attackers checked if they could connect to the card processing system. Following this, they legally opened or bought cards of the bank whose IT system they had hacked. Money mules – criminals who withdraw money from ATMs – with previously activated cards went abroad and waited for the operation to begin.
"After getting into the card processing system, the attackers removed or increased cash withdrawal limits for the cards held by the mules. They removed overdraft limits, which made it possible to overdraw even with debit cards. Using these cards, the mules withdrew cash from ATMs, one by one."






















