Another global hack? 'BadRabbit' ransomware infects computers across Europe
Reports indicate Kiev Metro, Odessa naval port and Odessa airport were all infected.

The computer networks of multiple organisations in Ukraine, Russia and Germany have been impacted by a widespread malware outbreak, reports suggest.
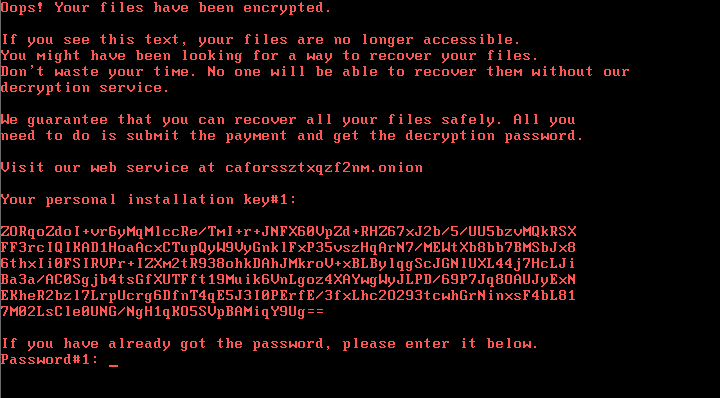
According to multiple cybersecurity firms, the spreading virus is dubbed "BadRabbit" and is a form of ransomware that locks down machines and demands bitcoin from administrators.
Screenshots of the infections posted to social media showed BadRabbit asking for 0.05BTC for decryption, which is equivalent to £215 ($280).
Reports indicate that the Kiev Metro, Odessa naval port and Odessa airport were all infected. Two Russian news outlets, Interfax and Fontanka, also had outages.
On 24 October 2017, Interfax tweeted: "Due to hacker attack Interfax servers failed. The technical services shall take all measures to restore the work systems.
"While core resources Interfax remain inaccessible due to the attacks, we publish news on our Facebook."
Eset, a Slovakian cybersecurity company, said that initial analysis suggested the malware was "Diskcoder.D" – otherwise known as "Petya". The same variant was responsible for a major cyberattack in June earlier this year which eventually spread across the globe.
The security firm found that infections were growing.
"ESET's telemetry has detected hundreds of occurrences of Diskcoder.D," it reported, adding: "Most of the detections are in Russia and Ukraine, however, also there are reports of computers in Turkey, Bulgaria and other countries are affected.
"ESET security researchers are working on a comprehensive analysis of the Diskcoder.D malware.
"According to their preliminary findings, Diskcoder.D uses the Mimikatz tool to extract credentials from the affected systems. Apart from this, it has also a hardcoded list of credentials."
In a separate blog post, Moscow-based cybersecurity firm Kaspersky Lab said that the majority of victims were located in Russia, but stressed that its probe was ongoing.
It elaborated: "We have also seen similar but fewer attacks in Ukraine, Turkey, and Germany. This ransomware has infected devices through a number of hacked Russian media websites.
"Based on our investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr [Petya] attack. However, we cannot confirm it is related to ExPetr. We continue our investigation." The firm urged victims not to pay the ransom.
In a technical advisory, it later described BadRabbit as "a previously unknown ransomware family" and said it had spotted approximately 200 targets - including news and media publications.
The report read: "The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor's infrastructure." It went on to say that "no exploits were used" in the cyberattack.
Initial analysis revealed that a malicious Adobe Flash installer played a key role in the spread.
#BadRabbit #cryptor attacked a number of Russia's major media. @interfax_news pic.twitter.com/5iLNs131Ml
— Group-IB (@GroupIB_GIB) October 24, 2017
Video of #BadRabbit in action, from @anyrun_app (doesn't show reboot) pic.twitter.com/3WpTj7f6qE
— Beaumont Porg, Esq. (@GossiTheDog) October 24, 2017
The previous Petya cyberattack spread via a hacked update from a company called MeDoc.
Months earlier, in May 2017, a strain of ransomware called "WannaCry" spread to hundreds of thousands of computers in 150 countries. In the UK, it knocked some of the National Health Service (NHS) computer networks offline, resulting in operational delays and closures.
Both Petya and WannaCry were linked to a stolen National Security Agency (NSA) exploit called "EternalBlue", released online by a mysterious unit dubbed The Shadow Brokers in March.
At least one security researcher suggested that EternalBlue was used in the BadRabbit attack.
But there was little consensus from experts on the details. "It is not confirmed," Eset researcher Jiri Kropac told IBTimes UK, adding that there instead appeared to be some similar elements.
WannaCry targeted the Windows' Server Message Block (SMB) protocol and was ultimately stopped by Marcus Hutchins, a 22-year-old security expert now facing a US federal indictment for allegations unrelated to his work on the massive ransomware outbreak.
Microsoft's Malware Protection Centre said it was investigating the potential outbreak.
This article has been updated with links to technical reports from cybersecurity firms.