Is WannaCry ransomware back? 2 new variants emerge hinting at future global attacks
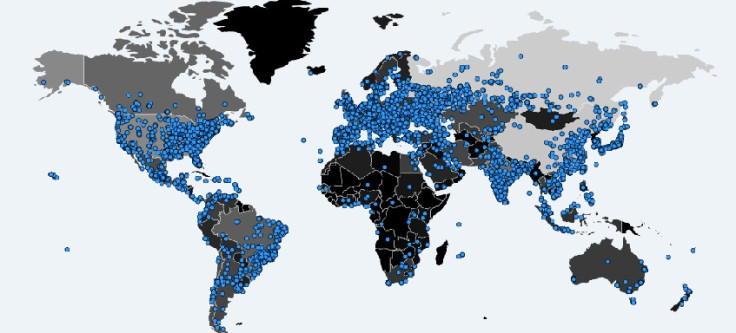
Experts estimate that the ransomware infected over 100,000 computers across nearly 150 countries.
Hundreds of thousands of people across the globe fell victim to a massive ransomware attack over the weekend. The ransomware, dubbed Wannacrypt or WannaCry, also hit the NHS in England, German train stations, the Russian government and numerous other organisations in over 100 countries. Although the attacks were stopped, due to quick thinking by a 22-year old British security expert, who prefers to be referred to as MalwareTech, experts are warning users to brace themselves for further attacks.
Security researchers have uncovered two new variants of the ransomware, which hint at the possibility of further attacks. Experts had previously warned that attackers may be working on upgrading the ransomware to renew their global onslaught.
"We have never seen such a fast spreading, well-coordinated attack with as many victims in enterprises who used to have proper security countermeasures against malware," Csaba Krasznay, director of the cybersecurity academy at Hungary's National University of Public Service and product manager at security firm Balabit, told IBTimes UK.
Experts have warned that further attacks could be in the offing. As MalwareTech told us previously, the kill switch he activated only worked for one particular strain of the WannaCry ransomware. Experts have now detected new WannaCry strains, which hint that attackers have been rolling up their sleeves and creating new versions of the ransomware to renew their attacks.
"New variants today are now spreading with a modified kill-switch domain," Chris Doman, security researcher at AlienVault told us. "Someone, likely different to the original attackers, made a very small change to the malware so it connects to a slightly different domain. That allowed it to continue propagating again.
"Thankfully some researchers are already registering the new domains as they identify them. The cat-and-mouse will likely continue until someone makes a larger change to the malware, removing the kill-switch functionality completely. At that point, it will be harder to stop new variants."
Have new attacks begun?
The main question probably on everyone's mind now - is WannaCyr back? Not yet, rather not completely. New variants uncovered by researchers hint at hackers working on upping their game.
Two variants of the WannaCry ransomware have been detected, according to Matt Suiche, founder of security firm Comae Technologies. Suiche said that one of the variants was "working" but that he "found a kill switch". He also said that he "immediately" registered the domain to "stop the new wave of global attacks".
Symantec has no evidence of a Wannacry email infection vector and no evidence of a non-killswitch version of the worm. #wannacry #wcry
— Security Response (@threatintel) May 14, 2017
Suiche said that a new WannaCry variant was discovered by Kaspersky that came without a kill switch. According to Suiche, this variant works only partially. Although this particular variant of the ransomware, which was shared by Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Lab, does not encrypt files yet, it can still spread using the NSA malware strains DoublePulsar and EternalBlue.
However, Suiche said that the ransomware variant working only partially may be a "temporary mistake from the attackers." This indicates that further attacks may be imminent. "The fact I registered the new kill-switch today to block the new waves of attacks (sinkhole.tech reported to me they are receiving hits) is only a temporarily relief which does not resolve the real issue which is that many companies and critical infrastructures are still dependent on legacy and out of support Operating Systems," Sucihe said.
How to stay safe?
Over 100,000 computers across at least 150 countries were infected by the ransomware attacks, according to Kaspersky. A Twitter account tracking the three bitcoin addresses tied to the WannaCry ransomware, the attacks have so far net a little over $38,000 in ransom and have so far, received 134 payments.
The three bitcoin wallets tied to #wcry ransomware have received 134 payments totaling $38,193.22 USD.
— actual ransom (@actual_ransom) May 15, 2017
Given that there is currently no decryptor for the ransomware and experts have warned that paying the ransomware is no guarantee that their data will be decrypted, it is essential that people do all they can to protect themselves from such attacks.
The most important thing to do is to patch your systems and ensure that all your computers are running the latest versions of their OS (operating systems). Microsoft has already issued out new patches to address and defend against WannCry ransomware. You can find out more about how to keep your Windows PC safe from such attacks, here.
© Copyright IBTimes 2025. All rights reserved.






















