Was a nation-state behind 'Petya'? Hack posed as ransomware for destruction not financial gain
Evidence suggests motivation behind 'Petya' outbreak more complex than assumed.

Roughly 48 hours after the Petya ransomware outbreak infected tens of thousands of Windows computers in dozens of countries, security experts have claimed the motivation behind the attack is becoming clearer: it was intended to cause destruction, not make money.
According to multiple cybersecurity firms the cyberattack was dressed up to look like typical ransomware but - in reality - contained powerful disk wiping capabilities more reminiscent of Shamoon, a notorious exploit which has been linked to nation-state activity.
"The ransomware was a lure for the media, this version of Petya actually wipes the first sectors of the disk," wrote Comae Technologies' Matthieu Suiche in a blog, adding the code sets it apart from other versions.
"It was to destroy" he told IBTimes UK.
Suiche said in his research that Petya, which at this stage has been given roughly half a dozen other names, was made to resemble the WannaCry attack in May – a previous global ransomware pandemic which eventually spread to Windows computers in 150 countries.
"Pretending to be a ransomware while being in fact a nation state attack is [...] a very subtle way for the attacker to control the narrative," he wrote, adding the malware was unlikely to be part of a money-making scheme but instead manufactured to do "irreversible" damage.
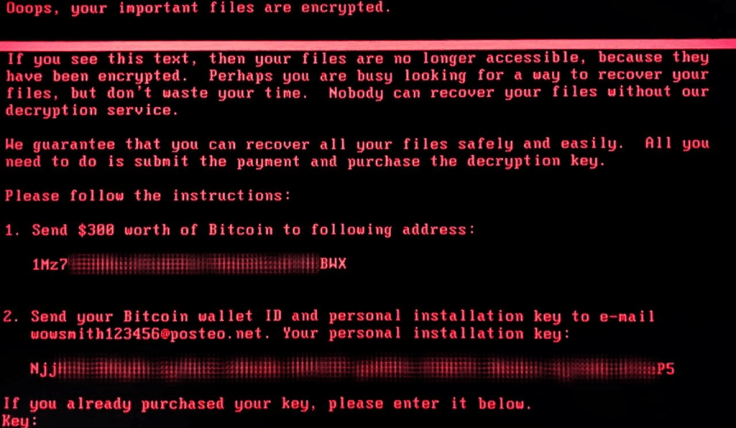
This week (27 June), companies in Ukraine and Russia were among the first to report infections from unexpected ransomware, which was locking down computers and demanding $300 worth of bitcoin. At time of writing the bitcoin wallet linked to the ransomware has collected just $10,200 (£7,937, 3.99 Bitcoin) — a paltry sum, which is again indicative that this was not a financially-motivated attack by money hungry hackers.
How Petya spread
It allegedly spread via hacked updates from MEDoc, accounting software widely-used in the region.
The variant of Petya, it emerged, was also super-powered by two exploits stolen from the US National Security Agency (NSA), titled EternalBlue and EternalRomance. But as Microsoft pointed out in its own in-depth analysis, the malware boasted a slew of sophisticated capabilities.
It circulated fast, but experts concluded the vast majority of infections were in Ukraine – patient zero. Furthermore, evidence from Russian cybersecurity firm Kaspersky Lab suggested that even if victims paid the ransom it was never made to give their data back.
"This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware," an analysis from researchers Anton Ivanov and Orkhan Mamedov stated on 28 June.
"This was a straight forward cyberattack with a target space of basically every company that does business in Ukraine," wrote security researcher The Grugq in a blog post.
No doubt, speculation will now move to who was the culprit of the attack, with fingers highly likely to point in the general direction of Ukraine's closest neighbouring country.
Many referenced other attacks in Ukraine of late, including a number of successful power grid cyberattacks (which also reportedly used 'wiping' malware) and the suspicious murder of an military official on the same day as the hack.
What it points to is a complex, if possibly unprovable, set of assertions.
"Non-Ukrainian organisations were affected, however, this may have been unintentional," noted Symantec Security Response expert Gavin O'Gorman. "This attack was an ineffective way to make money, but a very effective way to disrupt victims, and sow confusion."
So the possibility exists the attack may not have been a straightforward cyberattack, but instead a more targeted – and intentionally destructive – campaign which took advantage of known NSA tools to help masquerade as malware, confuse experts and maximise causalities.
"Not only have criminals found that ransomware is a great money-making scheme, but nation states and terrorist organisations have realized pseudo-ransomware makes a misleading and effective weapon," noted cyber expert Lesley Carhart. The investigation continues.
© Copyright IBTimes 2025. All rights reserved.






















