Can hackers really hijack a plane using the in-flight entertainment system?
Stay grounded, people. There's no direct evidence that in-flight system tampering can bring down a plane.

An ethical hacker has disclosed multiple cybersecurity vulnerabilities that could be used to tamper with in-flight entertainment (IFE) systems made by Panasonic Avionics and featured in over a dozen major airlines including Virgin, United, Qatar and AirFrance.
The problems, reported to Panasonic in March last year, could potentially give a hacker the ability to gain control over how passengers are shown information about the plane on seat screens – spoofing data like map routes, speed statistics and altitude values.
The flaws were outlined by Ruben Santamarta, a security consultant at IOActive, in a research paper released on 12 December. The analysis said an attacker could use the flaws to control the PA, lighting panels and – at a stretch – compromise customer credit-card information.
"I've been afraid of flying for as long as I can remember," said Santamarta. "It might sound like a sick cure to some but, as a hacker, learning everything I could about how planes work, from the aerodynamics to electronics, has reduced the fear significantly."
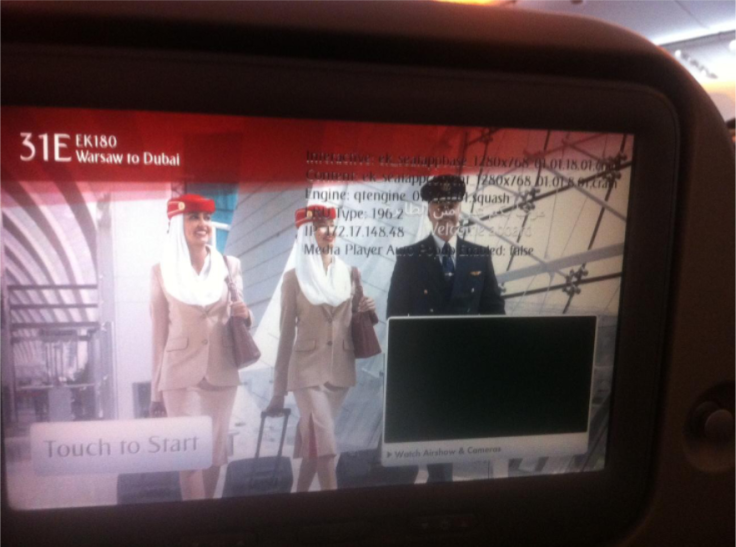
"On a flight from Warsaw to Dubai, I discovered I could access debug codes directly from a Panasonic in-flight display," he continued. "A subsequent internet search allowed me to discover hundreds of publically available firmware updates for multiple major airlines, which was quite alarming."
On the surface the flaws appear alarming (and some coverage has been overly sensationalist) however, in good news for anyone flying home for Christmas, there is no evidence in the IOActive paper that states planes will soon be falling out of the sky because of this in-flight system snafu.
Instead, it notes a hacker may be able to, "create a baffling and disconcerting situation for passengers." Santamarta added that based on how aircraft entertainment systems are isolated, in some scenarios this form of attack would be "physically impossible."
He did note it could, "theoretically be possible that such a vulnerability could present an entry point to the wider network depending on system configurations" and added the ability to cross the "red line" between passenger entertainment and aircraft control was "feasibly possible."
In reality, the assertions remain vague and the methods largely untested.
Aircraft networks are isolated into separate domains: passenger entertainment, passenger owned devices, airline information services, and aircraft control. This means that complete takeover of a plane is highly unlike by hacking one section, the research indicated.
"We cannot definitively say if an attacker could or could not get to the aircraft controls domain as a result of the vulnerabilities identified, as it would depend on the specific configuration of the system on a plane," Ruben told IBTimes UK.
"Reaching the avionics from the passenger domains does not depend on how secure the IFE is but how insecure the other devices are. There is no generic scenario, each case, each aircraft's model and its deployment needs to be reviewed to properly answer that question."
"Yet to prove"
Stephen Gates, chief research intelligence analyst at security firm NsFocus, said the IOActive research shows that physical separation of in-flight entertainment systems and aircraft control systems, "could never be more important."
But he added: "This research demonstrates that hackers could cause all sorts of issues that could impact a customer's 'experience' while flying, but have yet to prove they could impact flight control systems. Let's all hope that remains the case, long-term."
The IOActive research in many ways echoes the claims of a security researcher called Chris Roberts, who told the FBI last year he was able to exploit "vulnerabilities" with a plane's entertainment system to tamper with engine control systems between "15 to 20 times from 2011 to 2014."
Roberts later said his statement had been taken out of context.
IOActive's team of researchers hit the headlines last year after successfully demonstrating cybersecurity issues with the on-board entertainment systems of a Jeep Cherokee that could be exploited – under tested conditions – to kill the engine, disable the brakes and more.
Fiat Chrysler later issued a safety recall of 1.4m vehicles in the US over the hacking revelations.
© Copyright IBTimes 2025. All rights reserved.






















