Critical Drown HTTPS vulnerability: Online payments, account details could be visible on 11 million websites

An international group of security researchers have discovered a new security vulnerability affecting OpenSSL that can decrypt HTTPS, making it possible for hackers to see credit card numbers, account usernames, passwords, emails, IM chat messages and documents on 33% of all HTTPS websites on the internet today. This could lead to huge data leaks and potential thefts.
Researchers from Google, the OpenSSL Project, Tel Aviv University in Israel, Münster University of Applied Sciences and Ruhr University Bochum in Germany, the universities of Pennsylvania and of Michigan in the US, Two Sigma and the Hashcat project have discovered that it is possible to exploit a vulnerability affecting HTTPS and other services relying on SSL and TLS in order for hackers to view all communications between users and servers.
The Decrypting RSA with Obsolete and Weakened Encryption (DROWN) vulnerability (CVE-2016-0800) can be executed in under a minute using a single PC and can be conducted in under eight hours for a total cost of $440 (£314).
Many hugely popular websites affected
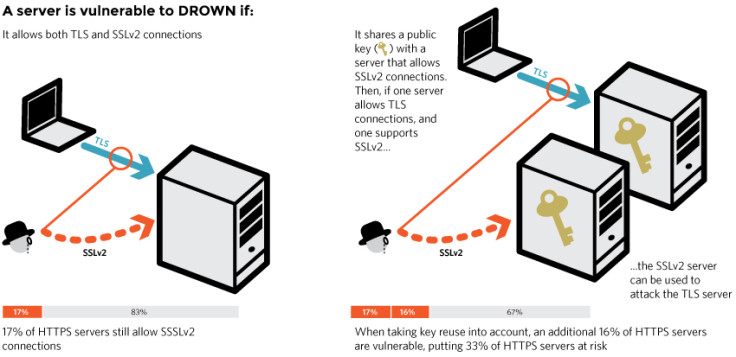
Using internet-wide scanning technology, the researchers found that the vulnerability affects 33% of all HTTPS websites today, as well as 25% of the top one million most popular websites in the world. This includes leading digital media publications, leading web service providers, betting, travel, gaming, shopping websites, messaging apps, pornographic websites and even software and security vendors, such as:
Yahoo, Buzzfeed.com, Samsung.com, Flickr.com, Blackboard.com, Weibo.com, Sina.com.cn, Alibaba.com, Stumbleupon.com. Groupon.com, NBA.com, Nature.com, EpochTimes.com, DailyMotion.com, Flipboard.com, Variety.com, CNBC.com, Avast.com, Scholastic.com, FinalFantasyXIV.com (Final Fantasy XIV online MMORPG game), Trivago.com, Mumsnet.com, Ladbrokes.com, NUS.edu.sg (National University of Singapore website), Jeep.com, HelloMagazine.com, Viber.com (messaging app), Weather.com, xHamster.com, LeMonde.fr, scmp.com (South China Morning Post), Apache.org, USNews.com, VMWare.com, FilmOn.com, NZHerald.co.nz, Nintendo.co.jp, Virginia.edu (University of Virginia website), BooHoo.com, Marvel.com, UNESCO.org and Nielsen.com
How the Drown vulnerability works
Modern servers and clients are using the TLS encryption protocol, but due to misconfigurations, many servers also still support SSLv2, a predecessor to TLS from the 1990s. SSLv2 is known to be very insecure, however until now it has never been a problem to have a server that supports the old protocol, as long as it was never in use.
The Drown vulnerability can affect your server if it allows SSLv2 connections (which is still quite a common occurrence), or if your server's private key is used on any other server that allows SSLv2 connections, even if it's for another protocol. Many companies tend to reuse the same certificate and private key for both their mail and web servers.
This means that if both servers use the same certificate and private key, hackers could get into one server and then use it to break the TLS connections on the other.
How can we protect our servers from being attacked?
The researchers have provided a handy search function on their website so you can type in the domain of your website and search to see if you are affected by this HTTPS vulnerability. However, in any case you need to make sure that your private keys are not used anywhere with server software that allowed SSLv2 connections – whether it's a web server, SMTP server, IMAP and POP server, or any other software that supports SSL/TLS.
The researchers have also provided specific instructions on how server operators can prevent problems on OpenSSL, Microsoft ISS Windows Server, Network Security Services, Apache, Postfix and Nginx.
"We have no reason to believe that Drown has been exploited in the wild prior to this disclosure," the researchers write. "[But] since the details of the vulnerability are now public, attackers may start exploiting it at any time, and we recommend taking the countermeasures explained above as soon as possible."
© Copyright IBTimes 2025. All rights reserved.






















