Smartphone owners better at protecting personal info but failing with sensitive work data

Smartphone users may be taking the protection of their own data more seriously, but most are still blissfully unaware of the access they give apps and when it comes to work information that is not high on their agenda.
The news comes from a report by mobile security company Lookout which surveyed 1,000 smartphone owners in the UK and found that 73% of respondents say they are now very careful about protecting the privacy of their personal data.
However, when it comes to work data stored on their devices, 64% say that work data is not as important as their own pictures, videos, text messages and emails.
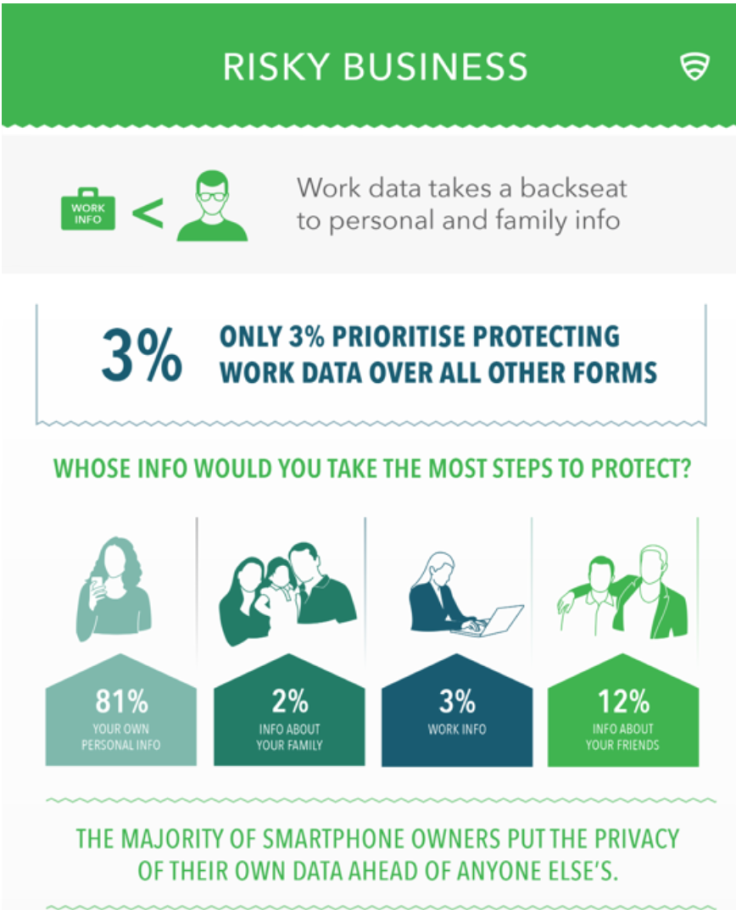
This will be a worrying statistic for enterprises who are increasingly allowing workers to use their personal devices at work to access sensitive data and networks.
Equally worrying will be the statistic that only 12% believe they are sharing access to their microphone, whereas in actual fact many of the most popular apps require microphone access. Similarly, only 13% believe they are sharing access to text messages and less than a quarter (24%) believe they are sharing their contacts.
Personal devices
Speaking to IBTimes UK ahead of the publication of the report, Aaron Cockerill, who is heading up the roll-out of the company's new enterprise products, said that "people think of their phones as their personal devices, unlike the way they think about their [desktop] computers."
Lookout's software is currently installed on some 60 million smartphones and tablets, protecting against malicious apps, behaviour and dangerous websites - but it is now branching out in an attempt to protect valuable enterprise data.
Lookout is leveraging data collected from its customers, and data collected on up to 40,000 new apps per day, to provide a continually evolving product which aims to stay one step ahead of the hackers. The company says that unlike its competitors, which use a network-based approach to protecting mobile devices, it uses machine intelligence to assess the risk of each app a user looks to download onto their device.
Since 2007, the company says it has analysed around 8 million apps in total.
Weakest link
The problem of course is that the weakest chain in the security link is inevitably the human one and while the new research shows people are finally coming around to understanding that their personal data needs to be protected (thanks in part to high profile leaks like the iCloud hacking) this is not yet the case for enterprise data it seems.
And things are likely to get worse in 2015 according to Cockerill, who echoes the concerns voiced by his boss and Lookout CEO Kevin Mahaffey, who said that significant iPhone and iPad malware threats will emerge this year with hackers having previously focused on Android:
"Bad guys are rational economic actors. Because Android is so much more popular in the world they're targeting the largest platforms first [but] criminals are soon going to double down on iOS with targeted attacks."
Cockerill said that as enterprises adopt iOS more and more as their computing platform we will see more targeted attacks against businesses who have developed their own apps.
New avenue of attack
The former Citrix employee said that in-house apps are "developed too quickly by inexperienced developers" and deployed before being tested fully. This, Cockerill says, is where he expects hackers to focus their attention, as the apps won't have passed Apple's rigorous testing procedures and will open up new avenues for attack which were previously closed off.
To help negate this problem, Lookout will be making the API it shares with Apple and Google for app submissions available to its business customers who can then submit their own apps to Lookout for testing.
Lookout is hoping that its big data approach will trump the signature-based approaches of the most popular solutions currently on the market, but as its own research shows, as long as people don't treat their work data as carefully as their personal data, hackers will always have a chance.
© Copyright IBTimes 2025. All rights reserved.





















