Huffington Post, Yahoo News, AOL and TMZ hit by malware ads – over 1.5bn visitors at risk
Last week, 24 major websites including the Huffington Post, Yahoo News, AOL, TMZ, FHM, GameZone, Match.com, 123greetings.com, Weather.com and Gaia Online unwittingly displayed malicious advertisements (malvertising) that infected computers with ransomware and locked them down.
On 31 December 2014, Cybersecurity firm Cyphort Labs spotted that malware had hijacked the AOL Platforms ad network, which serves ads to these websites. AOL Platforms has 199 million unique visitors a month and reaches 88.8% of the US internet audience.
For six days until AOL shut the malvertisements down on 5 January 2015, malicious ads were displayed on the websites, silently infecting computers with the Neutrino Exploit Kit, so users didn't even need to click on the ads to be infected.
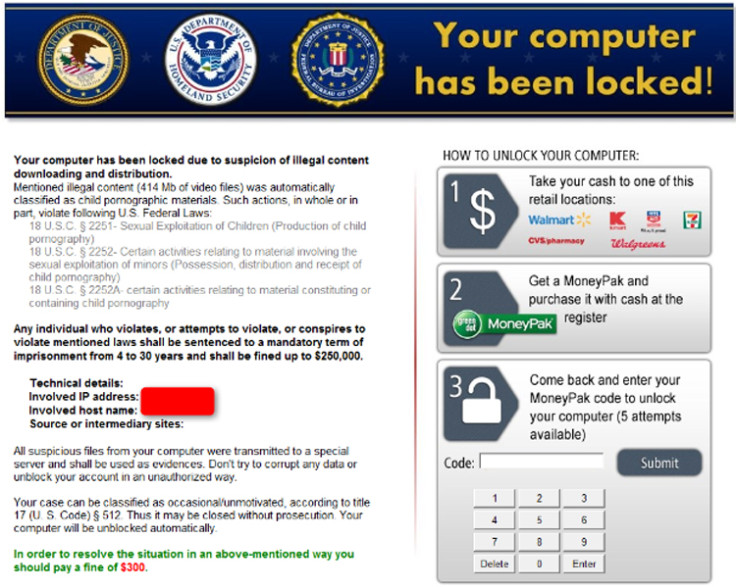
The ransomware, known as "Kovter ", was tailored to display a customised fake message from either US, UK, French, German and Turkish national police bodies such as the FBI and la Police Nationale, depending on the user's geographic location.
FHM's publisher Bauer Media UK told CNN that it was investigating the incident, but none of the other websites have commented or released statements.
Customised ransomware scam
The message informed the user that their computer had been locked down "due to suspicion of illegal content downloading and distribution" and that "suspicious files" had been transferred to a special server as evidence.
In order to unlock their computer and avoid prosecution, the scam would demand the user pay a fine. The US version of the ransomware demanded $300 (£198), only accepted using prepaid MoneyPak MasterCard and Visa cards that could be obtained from supermarkets.
Users who have been infected by the malware can solve the problem by booting their Windows PCs into Safe mode and then running an anti-malware program like Adwcleaner (which is free).
It is still unclear how many computers were infected, but the silver lining in the cloud is that the attacks have only affected people on Windows PCs who were using old, outdated web browsers such as Microsoft's Internet Explorer 8, which is the most-used version of the browser.
Users of modern, updated browsers like Internet Explorer 11, Google Chrome or Mozilla Firefox would not have been affected.
Redirecting to a Polish domain
Cyphort Labs says that the exploit kit used was Neutrino EK, which shares similarities with the Sweet Orange kit, a malicious tool kit that has been around since 2012.
The infected ads redirected their sources eight times, finally ending up at Polish .pl domains that had been compromised by the group behind the attack.
Malwarebytes Labs, which tracks malvertising, says that it is one of the top security threats of 2015 and is unlikely to go away anytime soon.
"Cyber criminals will likely continue to hijack ad networks with malicious code and pocket the dividends from hundreds of thousands of successful infections," said Jerome Segura, senior security researcher at Malwarebytes Labs, in a blog.
"This particular campaign is likely to migrate to other controllers or evolve into something else since it is now in the public domain and affected parties are cleaning up and securing their systems."
© Copyright IBTimes 2025. All rights reserved.






















