TorrentLocker ransomware infects over 2,300 UK victims but no one pays up

The criminal gang behind TorrentLocker have managed to infect 40,000 systems in countries like the UK, Turkey, Australia and Canada but only 570 people have paid the ransom to regain access to their files.
TorrentLocker is the latest is a series of pernicious pieces of malware known as ransomware which lock down your computer, encrypt your files and demand payment to release your personal data again.
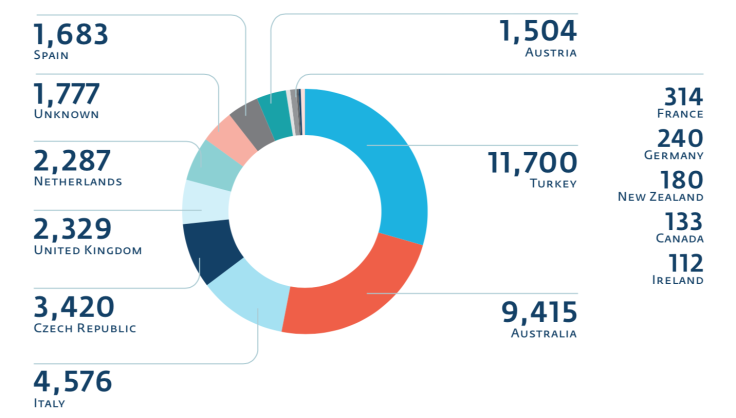
According to new research from security firm Eset, the criminals have managed to infect almost 40,000 systems in more than 12 countries around the world, but only 570 of these have resulted in people paying the ransom in bitcoin.
In the UK, Canada, Australia Ireland, Germany and New Zealand none of those infected with the malware paid any ransom. The most ransoms were paid in Turkey, Italy, Netherlands and Spain.
However despite this seemingly low conversion rate, the criminals have managed to bag a sizeable amount of money since the ransomware first appeared in February 2014.
The criminals demand payment in bitcoin ranging from just over 2 bitcoins to just over 4 bitcoins, meaning the total (based on bitcoin's price in November) is between $292,700 (£197,193) and$585,401.
Last week in a briefing in Eset's headquarters in Bratislava, security researcher Robert Lipovsky told IBTimes UK that the bitcoin wallet being used by the criminals had seen a total of 82,000 bitcoins (worth between £16 million and £34 million) deposited in it this year, meaning the group is clearly making money from other endeavours.
According to Eset's latest research the criminal gang spreading TorrentLocker is the same as the one behind the Hesperbot family of banking trojan malware which was uncovered last year.
The identity and location of the criminals is still unknown.
Royal Mail
The TorrentLocker malware is spread using well-crafted phishing emails which are tailored for specific countries. In the UK the criminals send messages which look like they come from the Royal Mail, directing victims to visit a fake website which even has a working Captcha feature to add to the look of authenticity.
Infections have been found in Austria, Canada, Czech Republic, Italy, Ireland, France, Germany, Netherlands, New Zealand, Spain, Turkey and the United Kingdom.
In total 39,670 ransom demands were made with more than 280 million documents encrypted. However just 1.44% of those infected have actually paid up, totalling 570 victims.
Turkey is the country with the most infections (11,700) and the country which has paid the most ransoms (228) followed by Australia which has seen more than 9,400 infections - however no one in Australia has paid the ransom according to Eset's research.
ESET researcher Marc-Etienne M. Léveillé who published the research, said that the criminals are adapting their methods once certain aspects of TorrentLocker has been made public:
"The attackers have been reacting to online reports by defeating Indicators of Compromise used for detection of the malware and changing the way they use Advanced Encryption Standards (AES) from Counter mode (CTR) to Cipher block chaining mode (CBC) after a method for extracting the key stream was disclosed."
© Copyright IBTimes 2025. All rights reserved.






















