What is ToastAmigo? Android malware exploits Toast overlay flaw to install other malicious software
The attack technique was already shown as potentially possible in a proof of concept earlier this year.

Security researchers have discovered a new Android malware that can secretly install other malicious software onto an infected device by exploiting the Android Toast overlay vulnerability. The malware, dubbed ToastAmigo, is the "first observed weaponized use" of vulnerability CVE-2017-0752 in Toast, Trend Micro reported.
The attack technique was already shown as potentially possible in a proof-of-concept earlier this year that could be leveraged by threat actors. Google patched the Toast Overlay flaw in September.
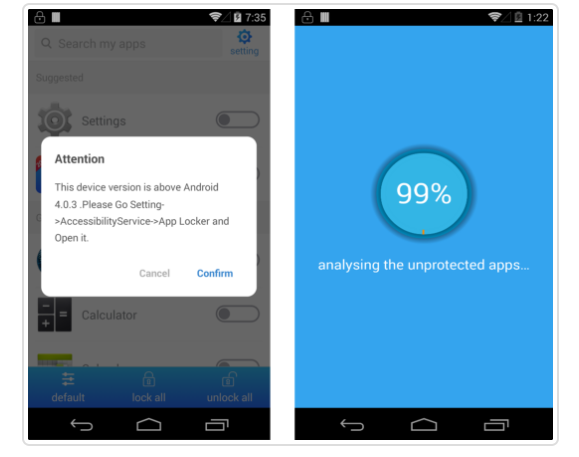
Trend Micro researchers found two malicious apps lurking in the Google Play Store masquerading as app lockers, both of which were named Smart AppLocker, which were used to spread ToastAmigo. The apps claimed to help secure a device's applications with a PIN code.
One of the apps had been downloaded more than 500,000 times as of 6 November, Trend Micro mobile threat analyst Lorin Wu wrote in a blog post.
Wu noted that the malicious apps abused Android's Accessibility features and enabled them to have "ad-clicking, app-installing and self-protecting/persistence capabilities".
Once installed, the app requests the user to grant Accessibility permissions for it to work. However, once a user grants permission, the apps launch a window that appears to "analyse" the unprotected app. Meanwhile, the app secretly carries out actions and commands in the background such as installing other malware.
"Overlay attacks entail drawing and superimposing Android View (i.e., images, buttons) atop other running apps, windows or processes," Wu explains. "A typical scenario for a Toast Overlay attack is to employ it to trick the user into clicking a window or button specified by the attacker instead of the legitimate one."
The malware has several other functions carried out behind the Toast window as well, including those to help keep itself from being removed from the device and maintain its core services.
The assortment of its malicious capabilities paired with its unique attack vector make the ToastAmigo malware a "credible threat", researchers said. They added that its functionalities can even be modified for other cyberattacks in the future as well.
The malware can "misuse Android's Accessibility feature to virtually do anything" and "update itself when getting the remote server's demands", they noted.
"ToastAmigo is the first we've seen to weaponize this proof of concept, and like many before it, we're bound to see this threat (and the other malware that it downloads/installs) being fine-tuned—given the malware's relatively low-key functionalities as of this time—or mimicked by other cybercriminals," Trend Micro said.
Researchers noted that all versions of Android OS except its latest 8.0 or Oreo version are affected and used users with earlier versions to immediately update and patch their device. Trend Micro said it notified Google of its findings and has removed the malicious apps from Google Play.





















