Anonymous Claims FBI Tracking iPhone Users
12 million Apple UDIDs on FBI laptop, claims AntiSec
A hacking group related to Anonymous claims to have stolen a file from an FBI laptop which contained over 12 million unique Apple device indentity numbers.
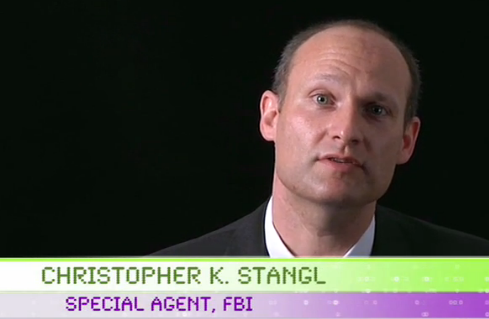
A post on Pastebin claims that during the second week of March 2012, a Dell Vostro laptop used by FBI Supervisor Special Agent Christopher K. Stangl (seen above in a video calling for computer science graduates to work with the FBI) was breached.
The group claims it found a file on the computer's desktop - labelled NCFTA_iOS_devices_intel.csv - which contained a list with details about over 12 million unique Apple iOS devices including the Unique Device Identifiers (UDID), user names, name of device, type of device, Apple Push Notification Service tokens, addresses and mobile phone numbers.
Must Read: Is This How Anonymous Hacked the FBI?
AntiSec, which is an off-shoot of the Anonymous hacking collective, and is claiming responsibility for the breach, published a list of 1,000,001 of these Apple UDIDs, but took the decision to trim the personal data.
However, the group believes there is enough data published to let a significant number of people search for their devices.
AntiSec claims the FBI is using these UDIDs to track people or at least that is its "best bet". The FBI themselves have yet to respond to the claims.
Security expert, Peter Kruse has reported on Twitter that the hacked data is correct, as he had found three of his devices among the list.
Each iOS device (iPhone, iPad, iPod touch) is assigned a unique alphanumeric number known as a UDID. This was previously used by app developers to track data usage for their apps, until Apple decided to reject any apps which sought to gain access to this number in the most recent official iOS update.
As well as believing that the FBI was using these identifiers to track people, AnticSec, in its missive on Pastebin, said it didn't agree with the idea of hardware coded identifiers anyway:
"We always thought it (UDIDs) was a really bad idea. That hardware coded IDs for devices concept should be eradicated from any device on the market in the future."
The file in which the data was supposedly found contains the acronym NCFTA, which, if the file is real, could refer to the National Cyber-Forensics Training Alliance, a non-profit organisation intended to combat cyber crimes.
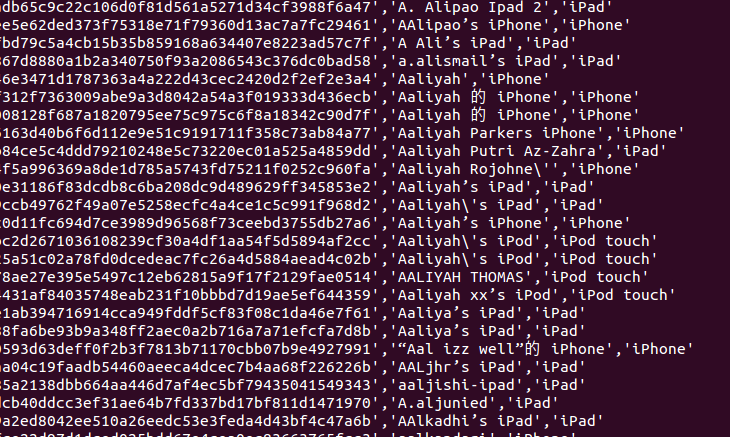
According to Swedish security company Eset, some of the names of the Apple devices on the list make for interesting reading. Among the names discovered are: Governor's iPad, Forensic iPhone, Chief Executive Officer's iPad, Riot Officer's iPad and a number with government email addresses attached.
However, as Eset's Ander Nilsson points out, people are free to name their iOS devices whatever they like.
It is unclear at this stage where the file came from, and could easily have been taken from an iOS app developer, as this would hve been the type of information they stored prior to Apple changing its policy on accessing UDID numbers.
© Copyright IBTimes 2025. All rights reserved.






















