Bitcoin traders beware: Hackers using fake Gunbot tool to deploy Orcus RAT in new phishing campaign
The nefarious developers behind the trojan also used a website designed to imitate the bitcoin forum bitcointalk.org.
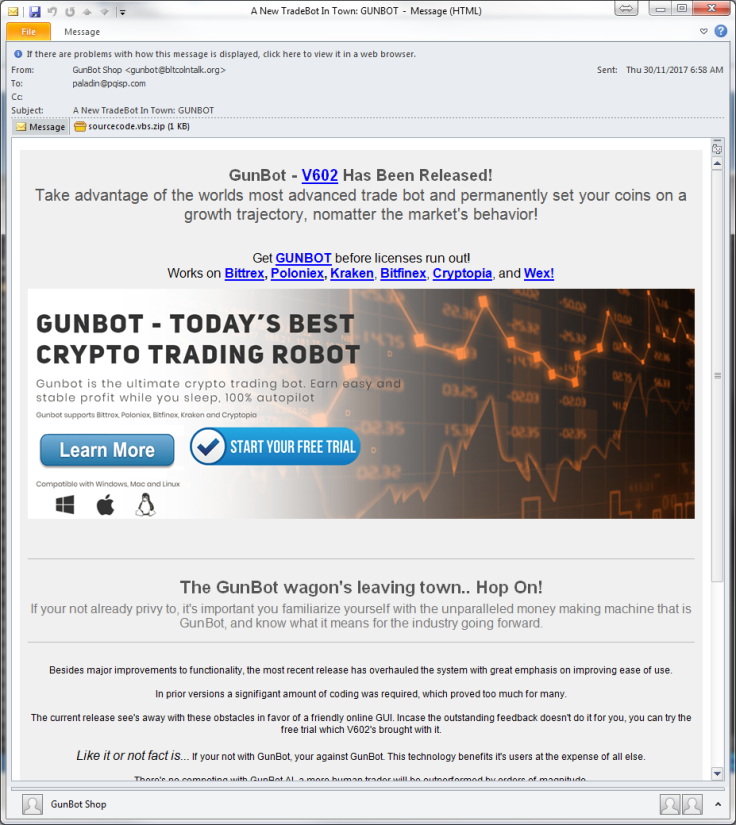
Hackers are looking to exploit the surging interest and value in Bitcoin by targeting traders with a fake advertisement for a bitcoin trading bot called Gunbot, researchers have found. However, the advertisement actually spreads the malicious Orcus remote access trojan (RAT) to steal bitcoin.
Bitcoin is currently the talk of the town as it continues to grow in acceptance, and has soared in value. At the time of publication, 1 BTC is worth $16,116 (£12,035). Traders can visit Bitcoin Equaliser where it offers an easy and reportedly highly profitable way to trade BTC.
Bitcoin trading bots are used to monitor price differences between different trading platforms. If an opportunity for profit happens to pop up, they automatically buy or sell bitcoin between the platforms based on limits previously set by the user.
Researchers at Fortinet spotted a new phishing campaign that targets eager bitcoin investors through a phishing campaign that claims to offer Gunbot, a new and legitimate bitcoin trading app developed by GuntherLab or Gunthy.
"However, instead of being a tool designed to ensure more profit, it serves an Orcus RAT malware that results in the loss of investments and more," Fortinet researchers wrote in a blog post on Thursday (7 December).
The phishing email with the phony ad actually comes with a .zip file attachment called "sourcode.vbs" that contains a simple VB script. When executed, it downloads a file that looks like a JPEG image but is actually a PE binary file. Researchers said the comments on the script suggest that the hackers behind the phishing campaign had no intention of hiding its behaviour.
"It's possible that they lack the technical knowledge and simply bought the components used in this campaign elsewhere," researchers said. "It can also be that they just simply don't care as long as there's someone out there that double-clicks the file without any inspection, which may well be the case.
"At first glance, the downloaded executable appears to be a benign inventory system tool with a lot of references to SQL commands for inventory procedures. After further analysis, however, we found that it is a trojanized version of an open source inventory system tool named TTJ-Inventory System."
Since 2016, the developers behind Orcus have been advertising it as a remote administration tool since that comes with all the features one can expect from a RAT software. However, what sets this one apart is its capability to load custom plugins developed by users or plugins available in the Orcus repository.
One plugin available in the repository can be used to perform Distributed Denial of Service (DDoS) attacks.
Like other remote access trojans, it also features password retrieval and key logging capabilities to steal everything a victim types on their device. This RAT can also remotely execute C# and VB.net code on an infected machine in real-time.
"Basically, if a server component gets "installed" to your system, the person on the other side is practically in front of your machine while seeing and hearing you at the same time – yes, it can activate your microphone and webcam even without you knowing," researchers warned.
It is also capable of disabling the light indicator on the webcam to avoid alerting a user that their webcam is active and even trigger the Blue Screen of Death (BSOD) if anyone tries to shut down the process.
"This makes it harder for targets to remove it from their systems," researchers said.
The nefarious developers behind the trojan also used a website designed to imitate the bitcoin forum bitcointalk.org to download the malware by posing as the Gunbot tool. The fake tool contained a similar trojanised "Inventory System" and a VB script download.
"We speculate this small change in the setup is being (will be) used in another campaign," Fortinet researchers said.
The domain seemed to be registered to "Cobainin Enterprises," an entity that had other questionable domains registered as well, the researchers noted. They suspect that the hackers cycle these websites between their malware campaigns.
"In our investigation of Orcus RAT, we have again proven again that its capabilities go beyond the scope of a harmless administration tool," they warned. "Regardless of the developer's claim and defense, the reality is that the application is being used in cybercrime campaigns."






















