Docker Hub Images Leak Auth Keys — Millions of Users Might Be at Risk Now
The leaked secrets, including AI model tokens and live production credentials, affect over 100 organisations

A major security vulnerability has surfaced in the container world, directly impacting Docker Hub users.
Due to leaked authentication keys found within certain images, millions of accounts could now be compromised.
Secrets Spilt: Credentials Found in 10,000 Images
Sensitive data that should have been secured—such as active login details for production systems, CI/CD databases, or LLM model keys—has been exposed in more than 10,000 Docker Hub container images. This issue affects slightly over 100 companies, including a top national bank and a Fortune 500 company.
As the largest container registry, Docker Hub lets developers upload, host, share, and quickly distribute pre-built Docker images that contain everything an application needs to operate.
Usually, developers rely on Docker images to simplify and expedite their entire software development and deployment lifecycle. Past studies, however, indicate that mistakes made while generating these images often expose valid secrets that persist for lengthy periods.
Security researchers from Flare, a threat intelligence company, analysed Docker Hub images uploaded in November and reported that 10,456 of them contained one or more exposed keys. The largest category among these 4,000 uncovered secrets was access tokens for AI models, notably from providers such as OpenAI, Hugging Face, Anthropic, Gemini, and Groq.
Sensitive Data Found in 42% of Scanned Images
The analysis of the images revealed that 42% of the scanned containers exposed five or more sensitive items. The analysis of the images revealed that 42% of the scanned containers exposed five or more sensitive items.
As Assaf Morag, Cybersecurity Researcher at Flare, pointed out: 'These multi-secret exposures represent critical risks, as they often provide full access to cloud environments, Git repositories, CI/CD systems, payment integrations, and other core infrastructure components.'
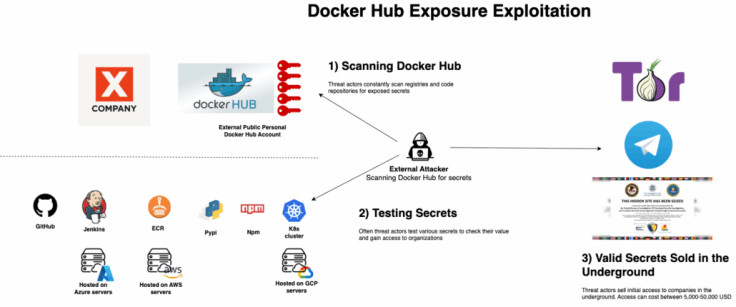
'Secrets exposure on Docker Hub isn't new. Many threat actors actively scan Docker Hub and other registries and code repositories, so exposed secrets are likely already compromised. What surprised us was the scale of exposure in 2025, despite increased awareness. That's why we believe the most effective approach is to keep raising awareness across the industry, not just about Docker Hub,' he added.
Who is at Risk? The 101 Compromised Companies
The analysis of 205 namespaces identified 101 companies in total, primarily small- and medium-sized businesses, along with some larger enterprises.
The findings showed that the highest number of organisations with exposed secrets were in the software development sector, followed by the market and industrial sectors, and AI and intelligent systems. Furthermore, sensitive data was exposed to more than 10 financial and banking companies.
The researchers stated that a persistent error was the use of .ENV files, which are meant to store database credentials, cloud access keys, tokens, and other authentication data required by a development project.
Aside from that, the researchers found hardcoded API tokens for AI services embedded directly in Python application files, config.json files, YAML configurations, and also noted GitHub tokens and login details for multiple internal environments. A portion of this sensitive data was even present in the Docker image manifest, a file that specifies the image's characteristics.
Many of these leaks seem to come from what are called 'shadow IT' accounts. These are Docker Hub accounts that avoid the company's stricter corporate monitoring, such as those used for personal projects or belonging to contractors.
Flare's Action Plan: From Static Keys to Vaults
According to Flare, approximately 25% of developers who unintentionally leaked secrets on Docker Hub fixed the error by removing the secret from the container or manifest within 48 hours. However, the key was not revoked in three-quarters (75%) of these cases. Therefore, anyone who managed to steal the credentials while they were exposed can still utilise them to compromise systems.
Flare provided clear guidelines: developers should refrain from storing secrets in container images and stop using long-lived, static credentials. Their advice is to centralise secrets management using a dedicated vault or secrets manager. For organisations, it is essential to implement active scanning across the entire software development life cycle and to revoke exposed secrets and invalidate previous sessions instantly.
© Copyright IBTimes 2025. All rights reserved.






















